In computing, a naming scheme is a system for assigning and managing names of objects connected into computer networks. It typically consists of a namespace...
3 KB (280 words) - 08:11, 17 July 2025
programming, identifier naming conventions In computer networking, naming scheme In humans, naming offspring In industry, product naming conventions In the...
5 KB (544 words) - 13:54, 25 July 2025
A computer network is a collection of communicating computers and other devices, such as printers and smart phones. Today almost all computers are connected...
102 KB (11,999 words) - 04:54, 8 August 2025
JANET NRS (category Wide area networks)
The JANET NRS (Name Registration Scheme) was a pseudo-hierarchical naming scheme used on British academic and research networks in the 1980s. Its purpose...
8 KB (871 words) - 16:23, 19 July 2025
Location transparency (category Computer networking)
matter to the user. A distributed system will need to employ a networked scheme for naming resources. The main benefit of location transparency is that...
2 KB (286 words) - 21:26, 19 March 2023
delivery model. NDN names are opaque to the network. This allows each application to choose the naming scheme that fits its needs, and naming can thus evolve...
35 KB (4,514 words) - 08:02, 25 June 2025
Communication protocol (redirect from Computer networking protocol)
result in the best and most robust computer networks. The information exchanged between devices through a network or other media is governed by rules...
64 KB (8,182 words) - 03:50, 2 August 2025
In computer programming, a naming convention is a set of rules for choosing the character sequence to be used for identifiers which denote variables, types...
37 KB (3,883 words) - 13:59, 25 July 2025
Uniform Resource Identifier (redirect from URI scheme)
retrieving information resources on a network (either on the Internet or on another private network, such as a computer filesystem or an Intranet) are Uniform...
37 KB (4,462 words) - 22:13, 7 August 2025
Images with Deep Neural Networks". Medical Image Computing and Computer-Assisted Intervention – MICCAI 2013. Lecture Notes in Computer Science. Vol. 7908....
168 KB (17,611 words) - 12:10, 26 July 2025
The NPL network, or NPL Data Communications Network, was a local area computer network operated by the National Physical Laboratory (NPL) in London that...
55 KB (5,776 words) - 20:11, 19 July 2025
uniform resource identifier (URI) scheme is a specific format of URI, used to specifically identify a file on a host computer. While URIs can be used to identify...
9 KB (1,322 words) - 16:40, 24 June 2025
electronic devices like computers and smartphones. This network attack typically happens under the usage of unsecured networks, such as public wifi connections...
31 KB (3,860 words) - 13:18, 5 August 2025
The Network Time Protocol (NTP) is a networking protocol for clock synchronization between computer systems over packet-switched, variable-latency data...
63 KB (6,452 words) - 15:30, 7 August 2025
Web, is a reference to a resource that specifies its location on a computer network and a mechanism for retrieving it. A URL is a specific type of Uniform...
17 KB (2,346 words) - 14:41, 20 June 2025
conjectured that no single kind of name can achieve more than two. For example: DNSSec offers a human-meaningful, secure naming scheme, but is not decentralized...
5 KB (447 words) - 15:51, 29 July 2025
A Uniform Resource Name (URN) is a Uniform Resource Identifier (URI) that uses the urn scheme. URNs are globally unique persistent identifiers assigned...
15 KB (1,570 words) - 07:32, 30 July 2025
field of information security. It focuses on protecting computer software, systems and networks from threats that can lead to unauthorized information...
220 KB (22,295 words) - 22:54, 28 July 2025
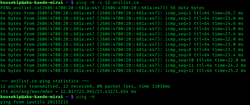
Ping is a computer network administration software utility used to test the reachability of a host on an Internet Protocol (IP) network. It is available...
19 KB (2,070 words) - 15:35, 4 August 2025
ALOHAnet (redirect from Pure aloha in computer network)
Reservation ALOHA scheme first analyzed by a group at BBN Technologies. One of the early computer networking designs, development of the ALOHA network was begun...
34 KB (4,365 words) - 09:29, 20 July 2025
the computer system, and are designed to be modular in the sense of network science. The network on chip is a router-based packet switching network between...
17 KB (1,774 words) - 06:31, 4 August 2025
before its initial release as part of the "World Class Cities" naming scheme by Apple Computer cofounder Steve Jobs. Designed as a bitmap face, New York was...
2 KB (190 words) - 02:52, 12 March 2025
today. Acorn in the 1990s released the Risc PC line and the Acorn Network Computer, and also had a stint in the set-top box and educational markets. However...
136 KB (14,172 words) - 08:16, 3 August 2025
Aadhaar (category Computer security in India)
welfare schemes and unemployment benefit schemes such as the domestic LPG scheme and MGNREGA. In these Direct Benefit Transfer (DBT) schemes, the subsidy...
187 KB (16,663 words) - 02:03, 28 July 2025
Feistel cipher (redirect from Feistel scheme)
for IBM; it is also commonly known as a Feistel network. A large number of block ciphers use the scheme, including the US Data Encryption Standard, the...
10 KB (1,316 words) - 19:41, 2 February 2025
Port forwarding (category Computer network security)
In computer networking, port forwarding or port mapping is an application of network address translation (NAT) that redirects a communication request...
14 KB (1,822 words) - 12:27, 20 March 2025
client computer to access files over a computer network much like local storage is accessed. NFS, like many other protocols, builds on the Open Network Computing...
24 KB (2,611 words) - 01:40, 7 August 2025
NetBIOS (redirect from Network Basic Input/Output System)
for Network Basic Input/Output System. It provides services related to the session layer of the OSI model allowing applications on separate computers to...
22 KB (2,533 words) - 14:22, 29 July 2025
about is an internal URI scheme (also known as a "URL scheme" or, erroneously, "protocol") implemented in various web browsers to reveal internal state...
29 KB (1,177 words) - 18:51, 25 March 2025
Subdivision surface (redirect from Refinement scheme)
In the field of 3D computer graphics, a subdivision surface (commonly shortened to SubD surface or Subsurf) is a curved surface represented by the specification...
13 KB (1,373 words) - 20:30, 19 March 2024