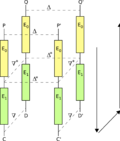
1994, the differential-linear attack is a mix of both linear cryptanalysis and differential cryptanalysis. The attack utilises a differential characteristic...
4 KB (385 words) - 03:30, 1 February 2024
cipher from the attack, for an n-bit non-linear function one would ideally seek as close to 2−(n − 1) as possible to achieve differential uniformity. When...
13 KB (1,677 words) - 11:30, 9 March 2025
and stream ciphers. Linear cryptanalysis is one of the two most widely used attacks on block ciphers; the other being differential cryptanalysis. The discovery...
6 KB (812 words) - 13:20, 1 November 2023
differential equations (SDEs) where the progression is random. A linear differential equation is a differential equation that is defined by a linear polynomial...
44 KB (5,187 words) - 16:53, 2 June 2025
The differential analyser is a mechanical analogue computer designed to solve differential equations by integration, using wheel-and-disc mechanisms to...
26 KB (2,772 words) - 21:05, 9 March 2025
Phase" "Differential-Linear Attacks against the Stream Cipher Phelix" Yaser Esmaeili Salehani; Hadi Ahmadi (2006). "A Chosen-key Distinguishing Attack on Phelix"...
8 KB (789 words) - 08:24, 28 November 2023
cryptanalysis, and has acted as a catalyst in the discovery of differential and linear cryptanalysis. There have been several different revisions of FEAL...
5 KB (551 words) - 01:40, 17 October 2023
provably secure against differential cryptanalysis, linear cryptanalysis, and even certain types of undiscovered cryptanalytic attacks. The cipher uses a block...
5 KB (435 words) - 15:07, 29 October 2023
Cryptology ePrint Archive. Wu, Hongjun; Preneel, Bart (2007). "Differential-Linear Attacks Against the Stream Cipher Phelix". In Biryukov, Alex (ed.). Fast...
12 KB (975 words) - 17:42, 26 May 2025
Data Encryption Standard (section Brute-force attack)
Chosen-Plaintext Linear Attack on DES. Fast Software Encryption - FSE 2000: pp262–272 Langford, Susan K., Martin E. Hellman: Differential-Linear Cryptanalysis...
60 KB (6,717 words) - 14:31, 5 July 2025
was that the forward- and backward-differential trails that need to be combined, did not share any active non-linear elements. How is it known that this...
18 KB (3,173 words) - 22:38, 29 October 2023
S-boxes can be analyzed using linear cryptanalysis and differential cryptanalysis in the form of a Linear approximation table (LAT) or Walsh transform and Difference...
10 KB (929 words) - 20:28, 24 May 2025
becomes available. Although the differential and linear attacks, currently best attack on DES-X is a known-plaintext slide attack discovered by Biryukov-Wagner...
4 KB (533 words) - 09:53, 31 October 2024
cryptography, the eXtended Sparse Linearization (XSL) attack is a method of cryptanalysis for block ciphers. The attack was first published in 2002 by researchers...
15 KB (1,834 words) - 05:42, 19 February 2025
encryption • DFC (cipher) • Dictionary attack • Differential cryptanalysis • Differential-linear attack • Differential power analysis • Diffie–Hellman key...
67 KB (2,932 words) - 14:09, 20 July 2025
output (a hook which Differential cryptanalysis uses), thus improving LOKI91's immunity to this attack, as detailed by the attacks authors (Biham and Shamir...
6 KB (723 words) - 23:05, 27 March 2024
interpolation attack is a type of cryptanalytic attack against block ciphers. After the two attacks, differential cryptanalysis and linear cryptanalysis...
12 KB (2,288 words) - 21:31, 30 July 2024
Block cipher (section Linear cryptanalysis)
cryptanalytic attacks. Both differential and linear cryptanalysis arose out of studies on DES design. As of 2016[update], there is a palette of attack techniques...
51 KB (6,569 words) - 04:44, 14 July 2025
cryptography, the boomerang attack is a method for the cryptanalysis of block ciphers based on differential cryptanalysis. The attack was published in 1999...
9 KB (864 words) - 04:16, 17 October 2023
has been published. An attack on 7 rounds with time complexity of 257 operations has been published. A differential fault attack has been published using...
13 KB (1,376 words) - 13:37, 2 May 2024
rounds composed of S-boxes and linear transformations. The general idea of the attack is to construct a differential characteristic that has its most...
14 KB (1,939 words) - 19:32, 23 September 2020
operations are linear. DES's S-boxes are its only non-linear component, and flaws in them are what both differential cryptanalysis and linear cryptanalysis...
5 KB (717 words) - 21:33, 16 March 2024
attack to be merely a reinvention of this existing technique. Secondly, Dinur and Shamir credit Michael Vielhaber's "Algebraic IV Differential Attack"...
6 KB (785 words) - 15:39, 11 April 2025
It was found to be susceptible to an effective theoretical differential cryptanalysis attack considerably faster than an exhaustive search. LOKI Advanced...
4 KB (412 words) - 07:03, 27 April 2022
Jongsung Kim; Guil Kim; Seokhie Hong; Sangjin Lee (July 2004). Differential-Linear Type Attacks on Reduced Rounds of SHACAL-2. ACISP 2004. Sydney: Springer-Verlag...
9 KB (903 words) - 07:08, 27 April 2022
Camellia remains unbroken in its full implementation. An impossible differential attack on 12-round Camellia without FL/FL−1 layers does exist. The S-boxes...
18 KB (1,805 words) - 21:49, 19 June 2025
described differential related key attacks on five and six rounds of KASUMI. Differential attacks were introduced by Biham and Shamir. Related key attacks were...
5 KB (688 words) - 10:33, 3 January 2025
Cipher security summary (section Best attack)
(2002-02-04). Linear Cryptanalysis of Reduced Round Serpent. FSE 2002. doi:10.1007/3-540-45473-X_2. Junod, Pascal (2001). On the Complexity of Matsui's Attack. Selected...
15 KB (801 words) - 01:34, 22 August 2024
successfully attacked. The best published attacks on Simon in the standard attack model (CPA/CCA with unknown key) are differential cryptanalysis attacks; these...
18 KB (1,841 words) - 22:50, 2 July 2025
cryptography, impossible differential cryptanalysis is a form of differential cryptanalysis for block ciphers. While ordinary differential cryptanalysis tracks...
10 KB (850 words) - 15:40, 7 December 2024