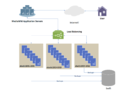
In computing, a handshake is a signal between two devices or programs, used to, e.g., authenticate, coordinate. An example is the handshaking between a...
8 KB (1,017 words) - 19:40, 28 March 2025
are many other types of handshaking in computing.) – discuss] Handshake deal, another term for an oral contract Handshaking lemma, a specific statement...
675 bytes (105 words) - 22:06, 10 March 2025
Transmission Control Protocol (redirect from TCP handshake)
connection based on agreed parameters; they do this through three-way handshake procedure. The server must be listening (passive open) for connection...
109 KB (12,941 words) - 18:55, 17 June 2025
Transport Layer Security (redirect from SSL handshake)
layer and is itself composed of two layers: the TLS record and the TLS handshake protocols. The closely related Datagram Transport Layer Security (DTLS)...
178 KB (17,519 words) - 21:07, 27 June 2025
In computing, load balancing is the process of distributing a set of tasks over a set of resources (computing units), with the aim of making their overall...
49 KB (6,593 words) - 07:51, 19 June 2025
In computing, bandwidth is the maximum rate of data transfer across a given path. Bandwidth may be characterized as network bandwidth, data bandwidth...
12 KB (1,217 words) - 18:06, 22 May 2025
In computing, the Challenge-Handshake Authentication Protocol (CHAP) is an authentication protocol originally used by Point-to-Point Protocol (PPP) to...
6 KB (755 words) - 07:44, 28 May 2024
User Datagram Protocol (redirect from UDP (computing))
different functions at the source and destination of the datagram. It has no handshaking dialogues and thus exposes the user's program to any unreliability of...
22 KB (2,789 words) - 14:22, 6 May 2025
characteristic – Hall effect – Hamming code – Hamming distance – Handoff – Handshake (computing) – Hard copy – Hardware register – Harmonic analysis – Harmonic oscillator...
34 KB (2,802 words) - 02:36, 17 December 2024
Triangular number (redirect from Handshake problem)
words, the solution to the handshake problem of n people is Tn−1. Equivalently, a fully connected network of n computing devices requires the presence...
25 KB (3,594 words) - 22:10, 19 June 2025
In graph theory, the handshaking lemma is the statement that, in every finite undirected graph, the number of vertices that touch an odd number of edges...
29 KB (3,598 words) - 02:01, 24 April 2025
communicating machines to use is determined by the handshake process. Modifications were done in TLS 1.3 to the handshake process to cut down on the number of messages...
19 KB (2,358 words) - 16:00, 5 September 2024
WebSocket (category 2011 in computing)
making it compatible with HTTP. To achieve compatibility, the WebSocket handshake uses the HTTP Upgrade header to change from the HTTP protocol to the WebSocket...
54 KB (3,918 words) - 16:52, 27 June 2025
This is a list of computing and IT acronyms, initialisms and abbreviations. 0–9 A B C D E F G H I J K L M N O P Q R S T U V W X Y Z See also References...
92 KB (6,595 words) - 20:48, 20 June 2025
In computing, a stateful firewall is a network-based firewall that individually tracks sessions of network connections traversing it. Stateful packet...
6 KB (614 words) - 15:30, 13 April 2024
List of TCP and UDP port numbers (redirect from List of well known ports (computing))
remote method invocation (RMI) registry 1100 Unofficial SaltoSystems - Handshake for IP-Components 1112 Unofficial ESET virus updates 1113 Assigned Yes...
320 KB (13,096 words) - 00:34, 25 June 2025
VNC (redirect from Virtual Network Computing)
VNC (Virtual Network Computing) is a graphical desktop-sharing system that uses the Remote Frame Buffer protocol (RFB) to remotely control another computer...
14 KB (1,767 words) - 16:37, 19 June 2025
store client credentials for later impersonation to the server. Challenge-Handshake Authentication Protocol (CHAP) secures against this sort of replay attack...
15 KB (2,054 words) - 08:39, 30 May 2025
exchange. Developed by Trevor Perrin, the framework defines a series of handshake patterns—predefined sequences of message exchanges—that outline how parties...
75 KB (6,873 words) - 05:17, 13 June 2025
Remote procedure call (category Distributed computing)
In distributed computing, a remote procedure call (RPC) is when a computer program causes a procedure (subroutine) to execute in a different address space...
15 KB (1,750 words) - 09:26, 23 June 2025
Shared snapshot objects (category Distributed computing problems)
In distributed computing, a shared snapshot object is a type of data structure, which is shared between several threads or processes. For many tasks,...
25 KB (3,328 words) - 04:51, 18 November 2024
Number sign (section Computing)
in the URL https://en.wikipedia.org/wiki/Number_sign#Computing the portion after the # (Computing) is the fragment identifier, in this case denoting that...
41 KB (4,333 words) - 08:41, 26 June 2025
UUCP (section Initial handshake)
session. The session has three distinct stages: Initial handshake File request(s) Final handshake On starting, uucico will respond by sending an identification...
31 KB (4,277 words) - 20:59, 15 June 2025
additional password authentication, see e.g. US patent "Advanced modular handshake for key agreement and optional authentication". X3DH was initially proposed...
47 KB (5,306 words) - 11:21, 27 June 2025
Asynchronous circuit (redirect from Four-phase handshake)
the components are driven by a handshaking circuit which indicates a completion of a set of instructions. Handshaking works by simple data transfer protocols...
57 KB (6,031 words) - 12:33, 17 June 2025
acknowledge it, allowing the sender to remove the data, thus completing the handshake, and allowing another datum to be transmitted. In a delay-insensitive...
4 KB (524 words) - 17:35, 22 August 2018
synchronization is the task of coordinating multiple processes to join up or handshake at a certain point, in order to reach an agreement or commit to a certain...
21 KB (2,575 words) - 06:16, 2 June 2025
Computer terminal (redirect from Terminal (computing))
professional computing series. Addison-Wesley. ISBN 978-0-13-142901-7. Rodgers, Ulka (1990). UNIX database management systems. Yourdon Press computing series...
52 KB (6,535 words) - 19:04, 15 June 2025
source implementations published as OWL and OpenDrop. During the initial handshake devices exchange full SHA-256 hashes of users' phone numbers and email...
24 KB (2,336 words) - 00:54, 4 June 2025
ALTS (section Handshake protocol)
by the client, and contains a handshake authenticator, similarly to the one in ServerFinished. Once both parties computed the session key (record protocol...
7 KB (734 words) - 21:30, 16 February 2025