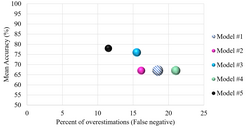
In statistics and machine learning, leakage (also known as data leakage or target leakage) is the use of information in the model training process which...
9 KB (1,027 words) - 22:44, 12 May 2025
by a microphone intended for a different source Leakage (machine learning) Leakage (retail) Leakage effect, the loss of tourist revenue from a country...
1 KB (188 words) - 11:55, 16 September 2023
Automated machine learning (AutoML) is the process of automating the tasks of applying machine learning to real-world problems. It is the combination...
9 KB (1,034 words) - 10:43, 30 June 2025
integrity Artificial intelligence in healthcare Data privacy Leakage (machine learning) "Who created AI app MediSafe? Hong Kong student and US software...
12 KB (1,148 words) - 03:36, 2 July 2025
Purged cross-validation (category Machine learning)
splits from the space of all possible combinations. Information leakage Machine learning in finance Cite error: The named reference Lopez2018 was invoked...
13 KB (1,358 words) - 18:41, 27 June 2025
of machine learning (ML) in earth sciences include geological mapping, gas leakage detection and geological feature identification. Machine learning is...
49 KB (4,482 words) - 03:34, 24 June 2025
Cross-validation (statistics) (category Machine learning)
(statistics). Boosting (machine learning) Bootstrap aggregating (bagging) Out-of-bag error Bootstrapping (statistics) Leakage (machine learning) Model selection...
44 KB (5,781 words) - 09:14, 19 February 2025
wasted leakage flux (stray flux). The corresponding inductance is called leakage inductance. Due to the presence of air gap, the role of the leakage flux...
10 KB (1,375 words) - 17:08, 14 June 2025
Language model benchmark (category Datasets in machine learning)
category, regardless of what the sentences actually say. contamination/leakage: Some benchmark questions may have answers already present in the training...
101 KB (10,887 words) - 05:45, 24 June 2025
losing the data on the originating side. Other terms associated with data leakage prevention are information leak detection and prevention (ILDP), information...
13 KB (1,443 words) - 18:44, 27 December 2024
Microsoft Azure (redirect from Azure machine learning studio)
feature of Screen Capture to provide additional security against data leakage. Entra ID connect is used to synchronize on-premises directories and enable...
91 KB (7,383 words) - 06:20, 25 June 2025
Mechanical engineering (redirect from Machine engineering)
Mechanical engineering is the study of physical machines and mechanisms that may involve force and movement. It is an engineering branch that combines...
61 KB (6,962 words) - 23:16, 30 June 2025
considers leakages and injections. 'Leakage' means withdrawal from the flow. When households and firms save part of their incomes it constitutes leakage. They...
32 KB (4,139 words) - 09:53, 23 June 2025
Finance (redirect from Cash leakage)
managed using computer-based mathematical techniques (increasingly, machine learning) instead of human judgment. The actual trading is typically automated...
67 KB (6,110 words) - 19:11, 26 June 2025
Data Version Control (software) (category Data mining and machine learning software)
"Asset Management in Machine Learning: A Survey". arXiv:2102.06919 [cs.SE]. Kapoor, Sayash; Narayanan, Arvind (2022). "Leakage and the Reproducibility...
30 KB (2,472 words) - 22:24, 9 May 2025
Euthanasia device (redirect from Mercy machine)
Unlike helium cylinders, nitrogen cylinders can be refilled in the event of leakage and nitrogen gas is naturally present in all tissues and this use cannot...
25 KB (2,904 words) - 10:40, 17 June 2025
Brain–computer interface (redirect from Mind–machine interface)
the control scheme. This results in very slow pace of the gameplay. Machine learning methods were used to compute a subject-specific model for detecting...
144 KB (16,742 words) - 02:47, 26 June 2025
Non-revenue water (redirect from Water leakage)
Wayback Machine Water 21, Journal of the IWA, April 2006, p. 30 A.O. Lambert and R.D. McKenzie:Practical Experience in using the Infrastructure Leakage Index...
31 KB (3,794 words) - 18:53, 6 March 2025
commitment scheme that are provably suboptimal in terms of storage and privacy leakage amount or using nested polar codes that can be made asymptotically optimal...
35 KB (4,103 words) - 12:39, 23 May 2025
Blocked rotor test (section Leakage reactance)
short-circuit current at normal voltage, power factor on short circuit, total leakage reactance, and starting torque of the motor can be found. It is very important...
6 KB (771 words) - 02:04, 19 November 2024
Welding power supply (redirect from Welding machine)
have significant leakage inductance for short circuit protection in the event of a welding rod becoming stuck to the workpiece. The leakage inductance may...
10 KB (1,355 words) - 18:43, 23 June 2025
act of creating fake content is not new, deepfakes uniquely leverage machine learning and artificial intelligence techniques, including facial recognition...
205 KB (19,323 words) - 09:27, 1 July 2025
Earthing system (section Earth leakage protection)
current restriction it is safer for gassy mines. Since the earth leakage is restricted, leakage protection devices can be set to less than 750 mA. By comparison...
41 KB (5,262 words) - 00:51, 4 April 2025
Electromagnetic coil (section Electric machines)
either a circular or rectangular cross section. This geometry has minimum leakage flux and radiates minimum electromagnetic interference (EMI). A coil with...
20 KB (2,464 words) - 20:10, 8 March 2025
Refrigerator (redirect from Refrigerating machine)
a welded container, "sealed unit", with greatly reduced likelihood of leakage or contamination. By comparison, externally-coupled refrigeration compressors...
79 KB (9,161 words) - 10:24, 25 June 2025
Cyworld (section 2011 data leakage and decline)
it was soon flooded with lawsuits demanding compensation for the leakage. The leakage yielded costly lawsuits for the company, in a country with virtually...
41 KB (4,149 words) - 07:46, 20 February 2025
Reinforcement Learning". Proceedings of the 39th International Conference on Machine Learning. International Conference on Machine Learning. PMLR. pp. 12004–12019...
89 KB (10,524 words) - 20:59, 29 June 2025
Programming paradigm (section Machine code)
onto patterns in the execution model (which have been inserted due to leakage of hardware into the abstraction). As a consequence, no one parallel programming...
24 KB (2,666 words) - 19:04, 23 June 2025
inadequate randomization, inadequate security, possibilities of sensory leakage, and inadequate documentation." Honorton himself had reported that only...
38 KB (4,480 words) - 14:56, 26 February 2025
growler is used to check the armature for short and open circuits and leakages to ground. The word armature was first used in its electrical sense, i...
11 KB (1,368 words) - 18:54, 8 May 2025