C string handling (redirect from Strcpy)
there are 7,813,206 uses of strlcpy, versus 38,644 uses of strcpy_s (and 15,286,150 uses of strcpy).[citation needed] "The C99 standard draft + TC3" (PDF)...
48 KB (3,568 words) - 02:41, 20 February 2025
== MAP_FAILED || zero == MAP_FAILED) errx(1, "either mmap"); strcpy(anon, str1); strcpy(zero, str1); printf("PID %d:\tanonymous %s, zero-backed %s\n"...
10 KB (1,155 words) - 08:10, 14 May 2025
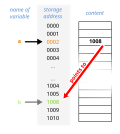
Null-terminated string (redirect from Strcpy s)
In computer programming, a null-terminated string is a character string stored as an array containing the characters and terminated with a null character...
9 KB (1,152 words) - 01:23, 25 March 2025
new_student.student_number = get_new_student_number(); strcpy(new_student.first_name, first_name); strcpy(new_student.last_name, last_name); //copying the result...
8 KB (1,099 words) - 13:23, 23 June 2025
rant about strcpy, strncpy and strlcpy." Archived 2016-02-29 at the Wayback Machine Keith Thompson. "No, strncpy() is not a "safer" strcpy()". 2012. "The...
41 KB (5,027 words) - 16:16, 11 May 2025
null-terminated string "excessive" with ASCII encoding in the A buffer. strcpy(A, "excessive"); "excessive" is 9 characters long and encodes to 10 bytes...
46 KB (5,132 words) - 08:55, 25 May 2025
containing those addresses using string manipulation functions such as strcpy(). However, this technique does not work if the attacker has a way to overflow...
5 KB (587 words) - 01:42, 8 November 2024
char *); char *strcpy (char *, const char *); #ifdef __cplusplus } #endif Thus, code such as: if (strcmp(argv[1], "-x") == 0) strcpy(a, argv[2]); else...
39 KB (4,519 words) - 11:00, 27 May 2025
This is illustrated with strcpy() in the following example: #include <string.h> void foo(char *bar) { char c[12]; strcpy(c, bar); // no bounds checking...
22 KB (2,668 words) - 14:19, 8 June 2025
The most criticized items are: string-manipulation routines, including strcpy() and strcat(), for lack of bounds checking and possible buffer overflows...
37 KB (3,694 words) - 11:18, 26 January 2025
functions in the C standard library, such as strlcat for strcat and strlcpy for strcpy Toolchain alterations, including a static bounds checker Memory protection...
131 KB (8,638 words) - 14:17, 2 July 2025
main(void) { int sock; struct sockaddr_in sa; int bytes_sent; char buffer[200]; strcpy(buffer, "hello world!"); /* create an Internet, datagram, socket using UDP...
29 KB (3,502 words) - 22:52, 30 June 2025
return address to avoid altering the canary. This prevents attacks using strcpy() and other methods that return upon copying a null character, while the...
25 KB (2,836 words) - 13:59, 27 April 2025
Wikispecies: Streptococcus pyogenes BacDive: 14758 CoL: 52Y4S EoL: 975366 EPPO: STRCPY GBIF: 3227092 iNaturalist: 130852 IRMNG: 10541361 ITIS: 966482 LPSN:...
41 KB (4,043 words) - 17:26, 16 July 2025
maliciously. int risky_programming(char *input) { char str[1000]; // ... strcpy(str, input); // Copy input. // ... } The function will result in undefined...
14 KB (1,744 words) - 12:13, 10 May 2025
_FORTIFY_SOURCE, which is a feature where unsafe string and memory functions (such as strcpy(), strcat(), and memcpy()) include checks for buffer overruns. These checks...
15 KB (1,852 words) - 10:00, 9 July 2025
"Bounds-checking interfaces (Annex K)" in C11. Some function name examples are strcpy_s(), memcpy_s(), printf_s(). This library was released along with Open Watcom...
16 KB (1,049 words) - 01:11, 2 May 2025
class Foo { public: Foo(): data_(new char[sizeof("Hello, World!")]) { std::strcpy(data_, "Hello, World!"); } Foo(const Foo& other) = delete; // disable copy...
11 KB (1,130 words) - 05:01, 26 April 2025
is int vulnerable_function(char * large_user_input) { char dst[SMALL]; strcpy(dst, large_user_input); } If the user input is larger than the destination...
8 KB (988 words) - 17:30, 1 September 2024
malloc(strlen(name) + 1); if (item->name == NULL) { free(item); return NULL; } strcpy(item->name, name); /* Return the newly created Item object */ return item;...
72 KB (9,654 words) - 15:55, 13 July 2025
first(); mem_buffer = malloc(300); // allocate a resource printf("%s\n", strcpy(mem_buffer, "first succeeded")); // not reached } free(mem_buffer); // NULL...
15 KB (1,784 words) - 01:57, 17 April 2025
reason why ffirst is so innovative, and is best illustrated by memcpy or strcpy when implemented with standard 128-bit non-predicated non-ffirst SIMD. For...
61 KB (8,675 words) - 10:31, 28 April 2025
CAN_RAW)) == -1) { perror("Error while opening socket"); return -1; } strcpy(ifr.ifr_name, ifname); ioctl(s, SIOCGIFINDEX, &ifr); addr.can_family = AF_CAN;...
6 KB (798 words) - 07:17, 12 December 2024
values into the parameter field 'value' break; // case DATE: extract (sdx); strcpy (invdate, sdx.data); // sdx.data is a pointer to the extracted character...
8 KB (994 words) - 23:03, 27 February 2024
exploit affecting multiple consoles and generations called TonyHawksProStrcpy was released, which is present in multiple Tony Hawk's titles for the PlayStation...
41 KB (5,572 words) - 10:50, 29 June 2025
caused by programmer error. A common source of error is the misuse of the strcpy and strcat string functions in the C programming language. There are two...
30 KB (3,213 words) - 16:56, 19 May 2025
VB RIGHT$(string,n) BASIC right(string,n) FreeBASIC, Ingres, Pick Basic strcpy(string2, string+n) (n must not be greater than the length of string) C string...
125 KB (4,077 words) - 12:50, 22 February 2025
vulnerabilities may exist due to the use of: Non-bounds-checking functions (e.g., strcpy, sprintf, vsprintf, and sscanf) that could lead to a buffer overflow vulnerability...
6 KB (697 words) - 07:01, 12 June 2024
standard C string handling and I/O functions including printf, strlen, strcpy and strcat. The strsafe functions require the length of the string in either...
2 KB (235 words) - 21:23, 20 November 2024
(CVE-2025-21782), triggered by syzbot, preventing crashes or corruption. Replaced strcpy with strscpy in orangefs_inode_getxattr(), further improving string safety...
18 KB (2,040 words) - 09:01, 25 June 2025