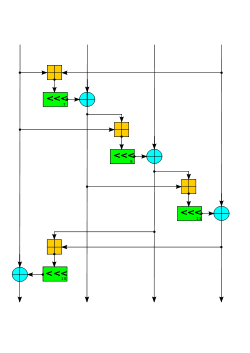
Stream ciphers, where plaintext bits are combined with a cipher bit stream by an exclusive-or operation (xor), can be very secure if used properly.[citation...
7 KB (1,028 words) - 12:52, 6 August 2025
stream cipher is a symmetric key cipher where plaintext digits are combined with a pseudorandom cipher digit stream (keystream). In a stream cipher,...
23 KB (2,231 words) - 21:32, 1 July 2025
cryptography, WAKE is a stream cipher designed by David Wheeler in 1993. WAKE stands for Word Auto Key Encryption. The cipher works in cipher feedback mode, generating...
2 KB (253 words) - 06:30, 19 July 2024
are experts who found that the Turing stream cipher has a number of weaknesses when faced with chosen IV attacks. For instance, its key scheduling algorithm...
3 KB (328 words) - 01:12, 15 June 2024
The Pike stream cipher was invented by Ross Anderson to be a "leaner and meaner" version of FISH after he broke FISH in 1994. Its name is supposed to...
1 KB (235 words) - 07:29, 19 June 2025
SHrinking) stream cipher is a fast software based stream cipher using Lagged Fibonacci generators, plus a concept from the shrinking generator cipher. It was...
1 KB (150 words) - 01:41, 28 June 2025
that do not require padding because they effectively use a block cipher as a stream cipher. Historically, encryption modes have been studied extensively...
52 KB (5,830 words) - 02:15, 29 July 2025
Symmetric-key algorithm (redirect from Symmetric cipher)
can use either stream ciphers or block ciphers. Stream ciphers encrypt the digits (typically bytes), or letters (in substitution ciphers) of a message...
15 KB (1,540 words) - 21:14, 19 June 2025
RC4 (redirect from RC4 Cipher)
In cryptography, RC4 (Rivest Cipher 4, also known as ARC4 or ARCFOUR, meaning Alleged RC4, see below) is a stream cipher. While it is remarkable for its...
45 KB (5,091 words) - 05:33, 18 July 2025
count) is a cryptographically secure pseudorandom number generator and a stream cipher designed by Robert J. Jenkins Jr. in 1993. The reference implementation...
5 KB (567 words) - 09:26, 15 May 2025
Trivium is a synchronous stream cipher designed to provide a flexible trade-off between speed and gate count in hardware, and reasonably efficient software...
10 KB (1,129 words) - 03:18, 17 October 2023
Rabbit is a high-speed stream cipher from 2003. The algorithm and source code was released in 2008 as public domain software. Rabbit was first presented...
5 KB (672 words) - 02:14, 20 July 2025
Phelix (redirect from Helix (cipher))
Attacks against the Helix Stream Cipher" "eSTREAM Short Report on the End of the Second Phase" "Differential-Linear Attacks against the Stream Cipher...
8 KB (789 words) - 08:24, 28 November 2023
Shamir attack is a stream cipher attack on the widely used RC4 stream cipher. The attack allows an attacker to recover the key in an RC4 encrypted stream from...
5 KB (843 words) - 19:54, 19 February 2024
Keystream (redirect from Key stream)
is a block mode that makes a block cipher produce a keystream and thus turns the block cipher into a stream cipher. In this simple example we use the...
3 KB (259 words) - 08:45, 30 January 2023
engineering (most often by telephone or email). Stream cipher attacks – Methods to break a stream cipher Protocol spoofing – Benign simulation of a protocol...
13 KB (2,672 words) - 18:27, 21 July 2025
Py is a stream cipher submitted to eSTREAM by Eli Biham and Jennifer Seberry. It is one of the fastest eSTREAM candidates at around 2.6 cycles per byte...
9 KB (1,235 words) - 23:12, 27 January 2024
Cryptography (redirect from Codes and ciphers)
symmetric-key ciphers typically involves looking for attacks against the block ciphers or stream ciphers that are more efficient than any attack that could...
101 KB (11,138 words) - 15:26, 1 August 2025
2006-10-11. Retrieved 26 January 2015. "A new distinguish attack against ABC stream cipher". IEEE Xplore. May 7, 2007. Retrieved June 12, 2025. v t e...
1 KB (116 words) - 11:22, 12 June 2025
cryptography, a related-key attack is any form of cryptanalysis where the attacker can observe the operation of a cipher under several different keys...
5 KB (688 words) - 10:33, 3 January 2025
In cryptography, SEAL (Software-Optimized Encryption Algorithm) is a stream cipher optimised for machines with a 32-bit word size and plenty of RAM with...
1 KB (140 words) - 17:55, 21 February 2025
Grain is a stream cipher submitted to eSTREAM in 2004 by Martin Hell, Thomas Johansson and Willi Meier. It has been selected for the final eSTREAM portfolio...
8 KB (1,069 words) - 23:23, 16 June 2024
000". Stream ciphers, such as RC4, are vulnerable to a bit-flipping attack, as are some block cipher modes of operation. See stream cipher attack. A keyed...
3 KB (325 words) - 21:43, 21 June 2024
is a synchronous stream cipher algorithm submitted to the eSTREAM Project of the eCRYPT network. In the final specification the cipher is called ACHTERBAHN-128/80...
5 KB (532 words) - 21:28, 12 December 2024
Salsa20 (redirect from ChaCha (cipher))
ChaCha are stream ciphers developed by Daniel J. Bernstein. Salsa20, the original cipher, was designed in 2005, then later submitted to the eSTREAM European...
33 KB (3,690 words) - 23:52, 4 August 2025
Correlation attacks are a class of cryptographic known-plaintext attacks for breaking stream ciphers whose keystreams are generated by combining the output...
15 KB (2,299 words) - 20:31, 29 July 2025
Crypto-1 (category Stream ciphers)
Crypto1 is a proprietary encryption algorithm (stream cipher) and authentication protocol created by NXP Semiconductors for its MIFARE Classic RFID contactless...
6 KB (536 words) - 15:43, 12 January 2025
SOBER (redirect from SOBER (cipher))
In cryptography, SOBER is a family of stream ciphers initially designed by Greg Rose of QUALCOMM Australia starting in 1997. The name is a contrived acronym...
4 KB (525 words) - 19:03, 19 July 2025
A5/1 (category Stream ciphers)
A5/1 is a stream cipher used to provide over-the-air communication privacy in the GSM cellular telephone standard. It is one of several implementations...
23 KB (2,725 words) - 00:35, 9 August 2024
ChaCha20-Poly1305 (category Stream ciphers)
encryption with associated data (AEAD) algorithm, that combines the ChaCha20 stream cipher with the Poly1305 message authentication code. It has fast software...
13 KB (1,509 words) - 15:01, 13 June 2025