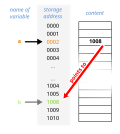
In computer science, a lookup table (LUT) is an array that replaces runtime computation of a mathematical function with a simpler array indexing operation...
22 KB (3,068 words) - 09:43, 18 May 2025
In the film and graphics industries, 3D lookup tables (3D LUTs) are used for color grading and for mapping one color space to another. They are commonly...
4 KB (319 words) - 19:58, 19 March 2025
Wavetable synthesis (redirect from Table-lookup synthesis)
Table-lookup synthesis (or Wavetable-lookup synthesis) (Roads 1996) is a class of sound synthesis methods using the waveform tables by table-lookup,...
28 KB (2,689 words) - 22:11, 6 March 2025
standard table-based approach would require an inconveniently large 65536-entry table. As mentioned in § Generating the lookup table, CRC tables have the...
58 KB (5,698 words) - 12:51, 26 May 2025
well-dimensioned hash table, the average time complexity for each lookup is independent of the number of elements stored in the table. Many hash table designs also...
53 KB (5,966 words) - 16:19, 24 May 2025
Palette (computing) (redirect from Color lookup table)
others it is dynamic, typically implemented via a color lookup table (CLUT), a correspondence table in which selected colors from a certain color space's...
14 KB (1,821 words) - 18:21, 19 March 2025
Halftone (section Lookup table)
halftone image. The lookup table provides a continuous-tone value for a given pixel and its distribution. The corresponding lookup table is obtained before...
26 KB (3,180 words) - 17:13, 27 May 2025
Hexagram (I Ching) (section Lookup table)
The I Ching book consists of 64 hexagrams. A hexagram in this context is a figure composed of six stacked horizontal lines (爻 yáo), where each line is...
35 KB (333 words) - 17:04, 7 April 2025
Bagua (section Hexagram lookup table)
The bagua (Chinese: 八卦; pinyin: bāguà; lit. 'eight trigrams') is a set of symbols from China intended to illustrate the nature of reality as being composed...
63 KB (2,743 words) - 08:34, 9 June 2025
CUSIP (section Check digit lookup table)
A CUSIP (/ˈkjuːsɪp/) is a nine-character numeric or alphanumeric code that uniquely identifies a North American financial security for the purposes of...
14 KB (1,651 words) - 13:49, 7 May 2025
implement a lookup table with constant worst-case access time. A perfect hash function can, as any hash function, be used to implement hash tables, with the...
23 KB (2,904 words) - 08:37, 11 June 2025
common situation is an algorithm involving a lookup table: an implementation can include the entire table, which reduces computing time, but increases...
6 KB (748 words) - 18:42, 7 June 2025
though it is never used in queries or reports; it is done by creating a lookup table that contains the warehouse surrogate key and the originating key. This...
28 KB (3,898 words) - 13:08, 4 June 2025
Pointer (computer programming) (redirect from Indirection lookup)
operations, like traversing iterable data structures (e.g. strings, lookup tables, control tables, linked lists, and tree structures). In particular, it is often...
72 KB (9,678 words) - 04:54, 20 March 2025
256-entry lookup table most closely match the two representative colors for each block. The two 8-bit indices pointing to colors in the lookup table are now...
11 KB (1,293 words) - 09:09, 26 August 2023
against their corresponding denoted sequence, using a lookup table. In the original paper, this lookup table is encoded and stored alongside the compressed text...
9 KB (1,223 words) - 11:59, 24 May 2025
block and its associated four color lookup table. A 2-bit index is used to determine which color from the lookup table will be used for each texel in the...
7 KB (830 words) - 06:45, 13 April 2025
may manage such a table instead of programmers. Transformation of input values to: an index, for later branching or pointer lookup a program name, relative...
53 KB (6,351 words) - 23:17, 19 April 2025
return 1 [by the convention that 0! = 1] else if n is in lookup-table then return lookup-table-value-for-n else let x = factorial(n – 1) times n [recursively...
30 KB (3,741 words) - 09:02, 17 January 2025
{\displaystyle c_{0}} and c 1 {\displaystyle c_{1}} , and a 4×4 two-bit lookup table. If c 0 > c 1 {\displaystyle c_{0}>c_{1}} (compare these colors by interpreting...
16 KB (2,003 words) - 08:22, 4 June 2025
used to "drive" the logic of the program. A simple example might be a lookup table containing a range of possible input values and a function pointer to...
13 KB (1,169 words) - 03:59, 6 June 2025
looked up in a predefined table which contains the necessary interpolation patterns. The interpolation data in the lookup tables are constrained by the requirement...
7 KB (758 words) - 17:57, 7 June 2025
maintain multiple tables, and each lookup must search through each table. Rainbow tables can achieve similar performance with tables that are k times larger...
24 KB (3,485 words) - 14:46, 6 June 2025
11.2 and GNU use a variant lookup table. Instead of 32-bit integers, 64-bit integers are used in the symbol lookup tables. The string "/SYM64/" instead...
15 KB (1,543 words) - 23:13, 6 June 2025
The Rijndael S-box is a substitution box (lookup table) used in the Rijndael cipher, on which the Advanced Encryption Standard (AES) cryptographic algorithm...
11 KB (1,256 words) - 18:12, 5 November 2024
obstacles are overcome. A simple stemmer looks up the inflected form in a lookup table. The advantages of this approach are that it is simple, fast, and easily...
31 KB (3,907 words) - 19:08, 19 November 2024
and specifically in compiler and assembler design, a literal pool is a lookup table used to hold literals during assembly and execution. Multiple (local)...
6 KB (550 words) - 13:55, 3 April 2025
Its implementation requires only a few instructions, plus a 256-byte lookup table containing a permutation of the values 0 through 255. This hash function...
4 KB (511 words) - 17:23, 17 December 2024
result is stored in a lookup table that is indexed by the values of those parameters; the next time the function is called, the table is consulted to determine...
30 KB (3,549 words) - 22:32, 24 May 2025