directly associated with blocking. Concurrent computing Data dependency Non-blocking algorithm Race condition Scheduling (computing) Stallings, William (2004)...
3 KB (315 words) - 21:26, 20 August 2024
Look up blocking in Wiktionary, the free dictionary. Blocking may refer to: Blacklist (computing) Blocking (computing), holding up a task until an event...
2 KB (307 words) - 14:06, 11 May 2025
abbreviation EVM (ЭВМ), present in some of the names below, means "electronic computing machine" (Russian: электронная вычислительная машина). The Russian abbreviation...
9 KB (710 words) - 22:38, 19 April 2025
concert to perform very large tasks. Fog computing – Distributed computing paradigm that provides data, compute, storage and application services closer...
71 KB (7,496 words) - 21:28, 27 July 2025
geo-blocking. This technology has become widely used in fraud prevention, advertising, and content localization, which are integral to geo-blocking applications...
33 KB (3,312 words) - 05:01, 15 July 2025
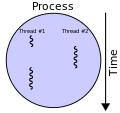
algorithms provide a useful alternative to traditional blocking implementations. A non-blocking algorithm is lock-free if there is guaranteed system-wide...
19 KB (2,392 words) - 03:11, 22 June 2025
Symbols for Legacy Computing is a Unicode block containing graphic characters that were used for various home computers from the 1970s and 1980s and in...
10 KB (286 words) - 18:49, 17 June 2025
Head-of-line blocking (HOL blocking) in computer networking is a performance-limiting phenomenon that occurs when a queue of packets is held up by the...
11 KB (1,113 words) - 06:19, 29 July 2025
A non-blocking linked list is an example of non-blocking data structures designed to implement a linked list in shared memory using synchronization primitives:...
7 KB (826 words) - 07:38, 7 May 2024
Pop-up ad (redirect from Pop-up ads blocking)
Smart Computing. September 2004. Archived from the original on 2010-05-22. Naraine, Ryan (March 18, 2004). "Windows XP SP2 Turns 'On' Pop-up Blocking". Retrieved...
13 KB (1,633 words) - 05:57, 29 July 2025
Betty Blocks Weigh the Options". October 10, 2019. "Nominatie voor Chris Obdam (Betty Blocks)". Computable. "Betty Blocks BV". Drimble.nl. "Betty Blocks verhuist...
7 KB (532 words) - 10:47, 5 March 2025
Computer (redirect from Computing device)
of the analytical engine's computing unit (the mill) in 1888. He gave a successful demonstration of its use in computing tables in 1906. In his work...
140 KB (14,116 words) - 06:41, 28 July 2025
Box-drawing characters (redirect from Block-drawing characters)
Semigraphics Unicode blocks Box Drawing Block Elements Geometric Shapes Symbols for Legacy Computing Symbols for Legacy Computing Supplement Box Drawing...
21 KB (1,322 words) - 03:00, 26 June 2025
Concurrent computing is a form of computing in which several computations are executed concurrently—during overlapping time periods—instead of sequentially—with...
29 KB (3,009 words) - 06:48, 3 August 2025
CUDA (redirect from Compute Unified Device Architecture)
general-purpose parallel computing. To that end, Buck developed Brook, a programming language designed to enable general-purpose computing on GPUs. His work...
85 KB (4,327 words) - 20:36, 3 August 2025
parallel computing: bit-level, instruction-level, data, and task parallelism. Parallelism has long been employed in high-performance computing, but has...
74 KB (8,380 words) - 19:27, 4 June 2025
RFID skimming (redirect from RFID Blocking Credit Card Holder)
electromagnetic fields interacting with the cards. An RFID blocking card is an RFID-blocking device that operates without a battery by receiving the RFID...
6 KB (720 words) - 16:18, 31 July 2025
Grid computing is the use of widely distributed computer resources to reach a common goal. A computing grid can be thought of as a distributed system...
45 KB (4,756 words) - 17:14, 28 May 2025
Confidential computing is a security and privacy-enhancing computational technique focused on protecting data in use. Confidential computing can be used...
47 KB (4,453 words) - 16:19, 8 June 2025
(typography) other Unicode blocks Box Drawing Geometric Shapes Halfwidth and Fullwidth Forms Symbols for Legacy Computing "Unicode character database"...
6 KB (327 words) - 06:28, 28 May 2025
syndrome. High-Performance Reconfigurable Computing (HPRC) is a computer architecture combining reconfigurable computing-based accelerators like field-programmable...
28 KB (3,437 words) - 21:10, 27 April 2025
provided for other blocking system calls. Alternatively, the program can be written to avoid the use of synchronous I/O or other blocking system calls (in...
33 KB (4,052 words) - 10:50, 19 July 2025
Symbols for Legacy Computing Supplement is a Unicode block containing additional graphic characters that were used for various home computers from the...
9 KB (306 words) - 19:27, 2 April 2025
Blockchain (redirect from Block chain)
blockchains may be considered secure by design and exemplify a distributed computing system with high Byzantine fault tolerance. A blockchain was created by...
136 KB (13,228 words) - 21:03, 12 July 2025
Computer cluster (redirect from Cluster computing)
and scheduled by software. The newest manifestation of cluster computing is cloud computing. The components of a cluster are usually connected to each other...
34 KB (3,744 words) - 00:28, 3 May 2025
In computing, a firewall is a network security system that monitors and controls incoming and outgoing network traffic based on configurable security...
29 KB (3,129 words) - 07:37, 14 June 2025
This is a list of computing and IT acronyms, initialisms and abbreviations. 0–9 A B C D E F G H I J K L M N O P Q R S T U V W X Y Z See also References...
118 KB (8,321 words) - 02:28, 4 August 2025
example, but not URLs. A firewall is well-suited for blocking IP addresses, but less so for blocking malicious files or passwords. Example uses include...
14 KB (1,554 words) - 01:56, 18 February 2025
In computing, logging is the act of keeping a log of events that occur in a computer system, such as problems, errors or broad information on current...
11 KB (1,284 words) - 11:05, 8 July 2025
In computing, tar is a shell command for combining multiple computer files into a single archive file. It was originally developed for magnetic tape storage...
36 KB (4,037 words) - 22:06, 2 April 2025