cryptography, a collision attack on a cryptographic hash tries to find two inputs producing the same hash value, i.e. a hash collision. This is in contrast...
17 KB (2,047 words) - 00:48, 10 June 2025
birthday attack is a bruteforce collision attack that exploits the mathematics behind the birthday problem in probability theory. This attack can be used...
18 KB (2,307 words) - 12:57, 5 June 2025
February 2017, CWI Amsterdam and Google announced they had performed a collision attack against SHA-1, publishing two dissimilar PDF files which produced the...
50 KB (5,744 words) - 14:18, 17 March 2025
the hash function's outputs. Conversely, a second-preimage attack implies a collision attack (trivially, since, in addition to x′, x is already known right...
7 KB (895 words) - 15:44, 13 April 2024
MD5 (redirect from MD5 attack)
collision. (Previous collision discoveries had relied on multi-block attacks.) For "security reasons", Xie and Feng did not disclose the new attack method...
46 KB (4,710 words) - 05:01, 3 June 2025
Instances where bad actors attempt to create or find hash collisions are known as collision attacks. In practice, security-related applications use cryptographic...
9 KB (1,142 words) - 00:48, 10 June 2025
MD4 (section Collision attacks)
first full collision attack against MD4 was published in 1995, and several newer attacks have been published since then. As of 2007, an attack can generate...
8 KB (871 words) - 18:48, 12 January 2025
brute-force attack, it is typically considered a flaw in the hash function. Cryptographic hash functions are usually designed to be collision resistant...
5 KB (661 words) - 06:57, 29 April 2025
an improved collision attack was found based on the technique from the previous best collision attack, this improved collision attack could reach 40...
9 KB (869 words) - 19:27, 21 December 2024
the best public attacks break preimage resistance for 52 out of 64 rounds of SHA-256 or 57 out of 80 rounds of SHA-512, and collision resistance for 46...
52 KB (4,982 words) - 14:44, 24 May 2025
bench.cr.yp.to. Tao, Xie; Liu, Fanbao; Feng, Dengguo (2013). Fast Collision Attack on MD5 (PDF). Cryptology ePrint Archive (Technical report). IACR. Stevens...
3 KB (464 words) - 07:05, 4 October 2024
Collision attack Preimage attack Length extension attack Cipher security summary Tao Xie; Fanbao Liu; Dengguo Feng (25 March 2013). "Fast Collision Attack...
17 KB (1,063 words) - 06:46, 25 May 2025
SHA-3 (section Security against quantum attacks)
d-bit output should have d/2-bit resistance to collision attacks and d-bit resistance to preimage attacks, the maximum achievable for d bits of output....
52 KB (5,726 words) - 19:03, 2 June 2025
attacks by describing a collision attack spanning 19 rounds of Tiger, and a 22-round pseudo-near-collision attack. These attacks require a work effort equivalent...
9 KB (910 words) - 14:47, 30 September 2023
that 384/512 version of NaSHA is susceptible to collision attacks, but the authors disputed those attacks and also included small changes to achieve the...
2 KB (200 words) - 23:44, 15 March 2021
presented in 1995 collisions of MD2's compression function, although they were unable to extend the attack to the full MD2. The described collisions was published...
9 KB (1,053 words) - 04:19, 31 December 2024
describe a collision attack with 2181 time complexity and 264 memory requirement in the same paper. Guo, et al, describe a second preimage attack on full...
8 KB (854 words) - 13:12, 25 May 2025
In cryptography, a brute-force attack or exhaustive key search is a cryptanalytic attack that consists of an attacker submitting many possible keys or...
21 KB (2,168 words) - 17:09, 27 May 2025
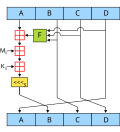
to a length extension attack, but is vulnerable to another attack based on a hash collision. The vulnerable hashing functions work by taking the input...
8 KB (1,082 words) - 12:51, 23 April 2025
("length-extension attack"). The alternative, appending the key using MAC = H(message ∥ key), suffers from the problem that an attacker who can find a collision in the...
18 KB (2,316 words) - 18:51, 16 April 2025
In computer security, a side-channel attack is any attack based on extra information that can be gathered because of the fundamental way a computer protocol...
31 KB (3,618 words) - 16:36, 25 May 2025
Rainbow table (redirect from Rainbow attack)
the hands of attackers, they can use a precomputed rainbow table to recover the plaintext passwords. A common defense against this attack is to compute...
24 KB (3,485 words) - 14:46, 6 June 2025
weight (45-bit) pseudo-collision attack on the Shabal compression function with time complexity 284 was presented. A preimage attack with 2497 time and 2400...
9 KB (1,139 words) - 09:04, 25 April 2024
cryptographic construction that is used is based on the MD5 hash function, collision attacks were in 2004 generally believed to not affect applications where the...
25 KB (2,879 words) - 04:06, 25 May 2025
defend against attacks that use precomputed tables (e.g. rainbow tables), by vastly growing the size of table needed for a successful attack. It also helps...
13 KB (1,533 words) - 12:18, 19 January 2025
Merkle tree (section Second preimage attack)
second-preimage attack in which an attacker creates a document other than the original that has the same Merkle hash root. For the example above, an attacker can...
15 KB (1,804 words) - 11:52, 27 May 2025
2025 Liverpool parade incident (redirect from 2025 Liverpool parade collision)
arrested for attempted murder, dangerous driving and drug offences after collision". Sky News. 27 May 2025. Retrieved 27 May 2025. Gawne, Ewan (29 May 2025)...
15 KB (1,367 words) - 09:47, 10 June 2025
the hash function being exposed to attacks including collision attacks, length extension attacks, and preimage attacks. Constructing a cipher or hash to...
5 KB (568 words) - 14:12, 24 May 2025
PBKDF2 (section HMAC collisions)
possible to trivially construct any number of different password pairs with collisions within each pair. If a supplied password is longer than the block size...
13 KB (1,337 words) - 12:18, 2 June 2025
cryptographic hash functions is used in Bitcoin mining. Collision resistance Collision attack Preimage attack Arvind Narayanan, Joseph Bonneau, Edward Felten...
3 KB (363 words) - 16:24, 10 February 2025