Control-flow integrity (CFI) is a general term for computer security techniques that prevent a wide variety of malware attacks from redirecting the flow...
19 KB (1,834 words) - 11:42, 25 March 2025
In computer science, control flow (or flow of control) is the order in which individual statements, instructions or function calls of an imperative program...
61 KB (6,038 words) - 00:41, 1 April 2025
signing. In this technique, an attacker gains control of the call stack to hijack program control flow and then executes carefully chosen machine instruction...
31 KB (3,848 words) - 04:24, 21 April 2025
Shadow stack (category Control flow integrity)
similar to stack canaries in that both mechanisms aim to maintain the control-flow integrity of the protected program by detecting attacks that tamper the stored...
6 KB (590 words) - 16:22, 3 May 2025
by compilers under -fsanitize or a similar flag) include: LLVM control-flow integrity and its kernel counterpart, which checks virtual tables and type...
15 KB (1,483 words) - 08:55, 19 February 2025
Indirect branch tracking (category Control flow integrity)
tracking (IBT), also known as branch target identification (BTI), is a control flow integrity mechanism implemented on some Intel x86-64 and ARM-64 processors...
3 KB (268 words) - 23:20, 2 April 2025
reduce vulnerabilities, e.g. address space layout randomization, control-flow integrity, access restrictions, and other techniques. There are no restrictions...
70 KB (8,176 words) - 17:11, 7 May 2025
David; Gross, Thomas R. (August 2015). "Control-flow bending: on the effectiveness of control-flow integrity". Proceedings of the 24th USENIX Conference...
32 KB (3,448 words) - 22:13, 10 March 2025
(UndefinedBehaviorSanitizer), to detect memory leaks (LeakSanitizer), or to check control-flow integrity (CFISanitizer). Fuzzing can also be used to detect "differential"...
46 KB (4,901 words) - 19:05, 3 May 2025
(and optimized) into OpenBSD/SPARC. Computer programming portal Control-flow integrity Address space layout randomization Executable space protection Memory...
25 KB (2,836 words) - 13:59, 27 April 2025
Software flow control is a method of flow control used in computer data links, especially RS-232 serial. It uses special codes, transmitted in-band, over...
8 KB (926 words) - 17:53, 22 November 2024
noises and electromagnetic fields. There are ideas stemmed from control-flow integrity (CFI) to prevent fault injection attacks and system recovery to...
189 KB (20,212 words) - 03:28, 7 May 2025
exploitable bugs.[citation needed] Over the years, a number of control-flow integrity schemes have been developed to inhibit malicious stack buffer overflow...
22 KB (2,668 words) - 05:08, 7 March 2025
low variables should not be allowed. On the other hand, to ensure integrity, flows to high variables should be restricted. More generally, the security...
15 KB (2,376 words) - 07:14, 19 April 2024
blocking all flows of information, minimizing data flow, or by stopping information leakage. The fourth essential claim comprising contextual integrity gives...
13 KB (1,799 words) - 21:12, 25 February 2025
exploitable vulnerabilities, such as control-flow integrity making use of specific language semantics, requiring type integrity, and safeguarding selective data...
18 KB (1,590 words) - 01:24, 9 May 2025
this the conventional protection against ROP style control flow hijacking attacks, Control Flow Integrity also can provide provable prevention but at a significant...
8 KB (1,112 words) - 15:55, 4 May 2025
open standard jointly developed by AMD, Intel, Sharp and Fujitsu Control-flow integrity, a general term for computer security techniques that prevent a...
2 KB (312 words) - 08:34, 8 April 2025
antibodies Indirect Branch Tracking, an Intel technology for enforcing control-flow integrity Inference-based therapy, a psychotherapy for treating obsessive-compulsive...
1 KB (170 words) - 03:38, 3 December 2024
sublayer and the logical link control (LLC) sublayer together make up the data link layer. The LLC provides flow control and multiplexing for the logical...
10 KB (1,265 words) - 08:34, 10 February 2025
Signal integrity or SI is a set of measures of the quality of an electrical signal. In digital electronics, a stream of binary values is represented by...
30 KB (3,904 words) - 13:30, 27 April 2025
Kernel Via Static Binary Rewriting, Program Shepherding and Partial Control Flow Integrity (PDF) Interpreter Exploitation: Pointer Inference and JIT Spraying...
37 KB (3,398 words) - 11:55, 5 May 2025
LOMAC (category Computer access control)
Access Control (LOMAC) is a Mandatory Access Control model which protects the integrity of system objects and subjects by means of an information flow policy...
2 KB (163 words) - 00:17, 26 January 2024
quality control documents, and production records. Oil and gas: Manage technical documentation, safety records, and compliance reports to ensure integrity and...
4 KB (336 words) - 16:05, 6 April 2025
and expedite the flow of traffic in the air, and provide information and other support for pilots. Personnel of air traffic control monitor aircraft location...
35 KB (3,780 words) - 16:30, 6 May 2025
requirements (Confidentiality, Integrity, Availability). Examples of security services are key management, access control, and authentication. Another authoritative...
14 KB (1,536 words) - 04:12, 5 May 2025
setpoint control to control the flow of material through the plant. A typical application is a PID controller fed by a flow meter and using a control valve...
25 KB (3,243 words) - 15:10, 11 April 2025
Acknowledgement (data networks) (redirect from Control-U)
time slot for an acknowledgment bit after each byte. C0 and C1 control codes Flow control (data) NACK-Oriented Reliable Multicast Negative-Acknowledgment...
6 KB (710 words) - 14:41, 4 April 2025
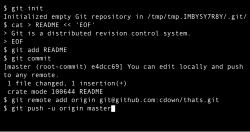
Git (redirect from Git (version control))
developing software collaboratively. Design goals of Git include speed, data integrity, and support for distributed, non-linear workflows — thousands of parallel...
71 KB (7,265 words) - 20:25, 3 May 2025
The Old River Control Structure is a floodgate system in a branch of the Mississippi River in central Louisiana. It regulates the flow of water from the...
14 KB (1,608 words) - 17:50, 5 March 2025