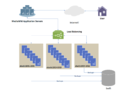
In computing, a firewall is a network security system that monitors and controls incoming and outgoing network traffic based on configurable security...
29 KB (3,142 words) - 03:18, 19 April 2025
In computing, a stateful firewall is a network-based firewall that individually tracks sessions of network connections traversing it. Stateful packet inspection...
6 KB (614 words) - 15:30, 13 April 2024
Look up firewall in Wiktionary, the free dictionary. Firewall may refer to: Firewall (computing), a technological barrier designed to prevent unauthorized...
2 KB (326 words) - 14:48, 4 November 2024
DMZ, while the rest of the organization's network is protected behind a firewall. The DMZ functions as a small, isolated network positioned between the...
13 KB (1,700 words) - 18:21, 3 March 2025
A firewall is a fire-resistant barrier used to prevent the spread of fire. Firewalls are built between or through buildings, structures, or electrical...
9 KB (1,139 words) - 03:42, 29 April 2025
NetLimiter is a client-side traffic shaping, monitoring and firewall (computing) software for the Windows operating system. Unlike most traffic-shaping...
4 KB (396 words) - 09:08, 4 July 2023
Dual-homed (section In firewalls)
network-layer firewall types screening router, screened-host, and screened subnet. Multihoming Firewall (computing) Router (computing) "Dual-homing:...
4 KB (370 words) - 15:21, 28 February 2025
An application firewall is a form of firewall that controls input/output or system calls of an application or service. It operates by monitoring and blocking...
10 KB (1,059 words) - 10:18, 14 February 2025
Screened subnet (redirect from Screened-subnet firewall)
hosts. DMZ (computing) Firewall (computing) Multitier architecture Wack, John; Carnahan, Lisa (December 1994). "3.4 Screened Subnet Firewall". Keeping Your...
7 KB (812 words) - 12:00, 24 November 2024
concert to perform very large tasks. Fog computing – Distributed computing paradigm that provides data, compute, storage and application services closer...
77 KB (7,983 words) - 13:12, 6 May 2025
Access Control List Firewall (computing) Traceroute Irby, David (c. 2000). "Firewalk : Can Attackers See Through Your Firewall?". GIAC Certifications...
2 KB (199 words) - 15:10, 17 May 2024
Air gap (networking) (redirect from Air gap (computing))
updates cannot be centrally managed. Air-gap malware Airplane mode Firewall (computing) Near sound data transfer NIPRNet SIPRNet Sneakernet Tempest (codename)...
19 KB (2,270 words) - 14:24, 19 February 2025
The Great Firewall (GFW; simplified Chinese: 防火长城; traditional Chinese: 防火長城; pinyin: Fánghuǒ Chángchéng) is the combination of legislative actions and...
91 KB (7,723 words) - 14:14, 20 April 2025
Management Protocol Kerberized Internet Negotiation of Keys Firewall (computing) Stateful firewall HTTPS HTTP Public Key Pinning Transport Layer Security TLS...
18 KB (1,725 words) - 19:07, 26 March 2025
Webster/SmartFilter product, Secure Computing merged with Border Network Technologies, a Canadian company selling the Borderware firewall. Border Network Technologies...
15 KB (1,776 words) - 22:05, 20 February 2024
paradigm Anti-spam appliances, detect and eliminate e-mail spam Firewall (computing), a computer appliance designed to protect computer networks from...
2 KB (313 words) - 20:41, 31 March 2025
Defensive computing is a form of practice for computer users to help reduce the risk of computing problems, by avoiding dangerous computing practices...
8 KB (1,078 words) - 15:07, 25 January 2024
an application layer firewall. A personal firewall differs from a conventional firewall in terms of scale. A personal firewall will usually protect only...
8 KB (1,001 words) - 14:43, 26 January 2024
FW (section In computing)
e-commerce company FatWire, a vendor of content management system Firewall (computing), a security device in computer networks FireWire, a high speed serial...
2 KB (315 words) - 23:50, 28 April 2025
concrete mechanism. Anti-virus Information Assurance - CIA Triad Firewall (computing) Protection mechanisms "What is a Security Policy? - Definition from...
3 KB (305 words) - 13:55, 27 January 2025
List of TCP and UDP port numbers (redirect from List of well known ports (computing))
connection to port 388 on the localhost. If the localhost is behind a firewall, the firewall must allow TCP access to port 388. ...[self-published source] "Active...
320 KB (13,110 words) - 23:14, 4 May 2025
open-source software portal Comparison of antivirus software Firewall (computing) Comparison of firewalls Comparison of computer viruses List of computer worms...
23 KB (2,193 words) - 13:17, 4 May 2025
servers, gateways, firewalls, new subnets, proxies, and so on. Also, distributed systems are prone to fallacies of distributed computing. On the other hand...
57 KB (6,666 words) - 18:52, 16 April 2025
Home network (category Personal computing)
Access control Computer security software Data backup Encryption Firewall (computing) Home automation Home server Indoor positioning system (IPS) Matter...
10 KB (1,265 words) - 04:38, 7 February 2025
firewall. A digital identity may be attached to anything from a person to a device, cloud service, application software, IoT system, or any computing...
19 KB (2,170 words) - 10:56, 6 May 2025
In computing, a trojan horse (or simply trojan; often capitalized, but see below) is a kind of malware that misleads users as to its true intent by disguising...
19 KB (1,858 words) - 14:43, 18 April 2025
In computing, load balancing is the process of distributing a set of tasks over a set of resources (computing units), with the aim of making their overall...
49 KB (6,559 words) - 12:53, 23 April 2025
a fleet of VM instances. Google Compute Engine Unit (GCEU), which is pronounced as GQ, is an abstraction of computing resources. According to Google,...
21 KB (2,328 words) - 22:37, 19 July 2024
scalability using service cards. 3GPP Long Term Evolution (LTE) Firewall (computing) H.323 Gatekeeper IP Multimedia Subsystem (IMS) Session Initiation...
20 KB (2,874 words) - 11:27, 19 October 2024
circuits (ASICs) to increase performance or add advanced filtering and firewall functionality. The concepts of a switching node using software and an interface...
43 KB (4,748 words) - 23:43, 3 May 2025