computer slang, J. Random Hacker is an arbitrary programmer (hacker). A mythical figure like the Unknown Soldier; the archetypal hacker nerd. This term...
2 KB (269 words) - 02:40, 9 October 2024
"555-1212"; // Not allowed in C#. // dictionary.Item("J. Random Hacker") = "553-1337"; dictionary["J. Random Hacker"] = "553-1337"; The dictionary can also be initialized...
87 KB (10,793 words) - 02:54, 22 August 2024
Jargon File (redirect from Hacker slang)
essay "A Portrait of J. Random Hacker" as "a wonderfully accurate pseudo-demographic description of the people who make up the hacker culture". He was nevertheless...
31 KB (3,536 words) - 14:09, 11 May 2025
book Mostly Harmless Random Hajile, also known as Randam, a character in the Snatcher video game J. Random Hacker Lobster Random Random House, a book publisher...
2 KB (248 words) - 03:25, 8 January 2024
up Dick, Tom, and Harry. Average Joe Joe Bloggs John Doe Joe Shmoe J. Random Hacker Alice and Bob Shakespeare, William; Bevington, David (1998). Henry...
7 KB (782 words) - 12:00, 4 May 2025
electronics (see life hack). Reflecting the two types of hackers, there are two definitions of the word "hacker": Originally, hacker simply meant advanced...
39 KB (4,243 words) - 17:45, 28 March 2025
eavesdropper) is also added. J. Random X (e.g. J. Random Hacker, J. Random User) is a term used in computer jargon for a randomly selected member of a set...
24 KB (2,940 words) - 14:43, 8 May 2025
or nonsense input data produces nonsense output J. Random Hacker, an arbitrary programmer (hacker) Halt and Catch Fire (HCF), an idiom referring to...
6 KB (771 words) - 02:39, 9 October 2024
completely ignore it. </p> =end =begin = COPYRIGHT Copyright 2005 J. Random Hacker <[email protected]>. Permission is granted to copy, distribute and/or modify...
5 KB (185 words) - 21:53, 28 April 2024
Random number generation is a process by which, often by means of a random number generator (RNG), a sequence of numbers or symbols is generated that cannot...
36 KB (4,422 words) - 19:27, 29 March 2025
would be put straight through to voicemail without the need of a PIN. A hacker could use caller ID spoofing to impersonate a target's handset caller ID...
16 KB (1,552 words) - 04:45, 6 May 2025
Government of India. The hacker group Lulz Security is formed. April 9: Bank of America website got hacked by a Turkish hacker named JeOPaRDY. An estimated...
142 KB (14,616 words) - 05:11, 15 May 2025
from the hacker ethics that originated at MIT and at the Homebrew Computer Club. The hacker ethics were chronicled by Steven Levy in Hackers: Heroes of...
48 KB (5,555 words) - 07:43, 6 March 2025
Isocket, Twilio, AMS Dataserfs, and Palantir Technologies. Hacker Dojo in California The Hacker Dojo was originally located at 140 South Whisman Road in...
15 KB (1,283 words) - 02:07, 19 December 2023
Procedural generation (redirect from Random dungeon)
human-generated content and algorithms coupled with computer-generated randomness and processing power. In computer graphics, it is commonly used to create...
21 KB (2,275 words) - 05:32, 30 April 2025
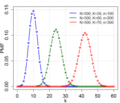
Hypergeometric distribution (redirect from Hypergeometric random variable)
present in K precincts, such as a hack or bug? This is the probability that k = 0 . Bugs are often obscure, and a hacker can minimize detection by affecting...
29 KB (4,095 words) - 17:58, 13 May 2025
roguelikes and the Eye of the Beholder series. Dungeon Hack features a three-dimensional, randomly generated dungeon; SSI claimed that "over 4 billion"...
8 KB (864 words) - 02:50, 15 March 2025
In epidemiology, Mendelian randomization (commonly abbreviated to MR) is a method using measured variation in genes to examine the causal effect of an...
24 KB (3,016 words) - 18:06, 13 May 2025
Jude Milhon (category Hackers)
Boing. The Joy of Hacker Sex (proposed) How to Mutate & Take Over the World: an Exploded Post-Novel (1997) (with R. U. Sirius) Random House ISBN 0-517-19832-0...
10 KB (894 words) - 02:09, 27 January 2025
passwords will map to identical hash values, which could make it easier for a hacker to guess the passwords from their hash value. Instead, a salt is generated...
13 KB (1,533 words) - 12:18, 19 January 2025
100–105) Hacker (1991, pp. 187–189, 191) Crews (1977, pp. 107–108) Hacker (1991, pp. 166–172) Lamb (2008, pp. 225–226) Crews (1977, pp. 108–109) Hacker (1991...
18 KB (2,173 words) - 16:26, 23 March 2025
Data dredging (redirect from P-hacking)
tests are performed, some produce false results of this type; hence 5% of randomly chosen hypotheses might be (erroneously) reported to be statistically significant...
26 KB (3,330 words) - 04:58, 31 March 2025
Roguelike (section Hack-based)
computer hacker. Calling themselves the DevTeam, they began to make major modifications to Hack's code. They named their new version NetHack, in part...
108 KB (10,991 words) - 15:06, 3 May 2025
A randomized controlled trial (or randomized control trial; RCT) is a form of scientific experiment used to control factors not under direct experimental...
88 KB (10,106 words) - 14:20, 30 March 2025
is implemented in Java Apache Commons Math library., and in NetHack for its RNG. Robert J. Jenkins Jr., ISAAC. Fast Software Encryption 1996, pp. 41–49...
5 KB (567 words) - 09:26, 15 May 2025
about the existence or not of long-run growth (or shrinkage) in y. Hacker and Hatemi-J (2010) provide simulation results on these matters, including simulations...
9 KB (1,349 words) - 07:32, 22 February 2024
Cult of the Dead Cow (category Hacker groups)
of the Dead Cow, also known as cDc or cDc Communications, is a computer hacker and DIY media organization founded in 1984 in Lubbock, Texas. The group...
43 KB (4,152 words) - 00:03, 9 May 2025
Cough (redirect from Random spontaneous coughing)
(March 2010). "Cough in the pediatric population". J. Pediatr. 156 (3): 352–358.e1. doi:10.1016/j.jpeds.2009.12.004. PMID 20176183. Nadia, Yousaf; Monteiro...
28 KB (3,154 words) - 14:35, 10 April 2025
and January 26, 2009 the Turkish hacker group "m0sted" used SQL injection to exploit Microsoft's SQL Server to hack web servers belonging to McAlester...
47 KB (4,983 words) - 10:03, 1 May 2025