The Password Hashing Competition was an open competition announced in 2013 to select one or more password hash functions that can be recognized as a recommended...
3 KB (256 words) - 18:15, 31 March 2025
Key derivation function (redirect from Password hashing)
In 2013 a Password Hashing Competition was announced to choose a new, standard algorithm for password hashing. On 20 July 2015 the competition ended and...
13 KB (1,640 words) - 18:48, 30 April 2025
circuits. In 2013 a long-term Password Hashing Competition was announced to choose a new, standard algorithm for password hashing, with Argon2 chosen as the...
27 KB (3,100 words) - 19:17, 20 May 2025
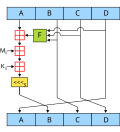
Argon2 (category Cryptographic hash functions)
derivation function that was selected as the winner of the 2015 Password Hashing Competition. It was designed by Alex Biryukov, Daniel Dinu, and Dmitry Khovratovich...
14 KB (1,491 words) - 04:51, 31 March 2025
the Secure Hash Standard. The NIST competition has inspired other competitions such as the Password Hashing Competition. Submissions were due October 31...
27 KB (2,244 words) - 20:34, 28 February 2024
PBKDF2 (category Password authentication)
other password hashing schemes: Catena, Lyra2, yescrypt and Makwa. Another alternative is Balloon hashing, which is recommended in NIST password guidelines...
13 KB (1,337 words) - 15:52, 25 May 2025
Salt (cryptography) (redirect from Password salting)
random data fed as an additional input to a one-way function that hashes data, a password or passphrase. Salting helps defend against attacks that use precomputed...
13 KB (1,533 words) - 12:18, 19 January 2025
Bcrypt (category Cryptographic hash functions)
bcrypt is a password-hashing function designed by Niels Provos and David Mazières. It is based on the Blowfish cipher and presented at USENIX in 1999....
27 KB (2,863 words) - 11:19, 24 May 2025
Yescrypt (category Cryptographic hash functions)
based on Scrypt. crypt (C) Lyra2 Password hashing Password Hashing Competition "Changes/yescrypt as default hashing method for shadow". Retrieved 2023-10-10...
2 KB (106 words) - 18:17, 31 March 2025
Key stretching (redirect from Password strengthening)
highly parallel hardware to speed up key testing. In 2013, a Password Hashing Competition was held to select an improved key stretching standard that would...
14 KB (1,816 words) - 19:22, 1 May 2025
HMAC (redirect from Keyed-Hashing Message Authentication)
of HMAC in password-hashing scenarios: it has been demonstrated that it's possible to find a long ASCII string and a random value whose hash will be also...
18 KB (2,316 words) - 18:51, 16 April 2025
Scrypt (category Cryptographic hash functions)
software portal Argon2 – winner of the Password Hashing Competition in 2015 bcrypt – blowfish-based password-hashing function bcrypt – blowfish-based cross-platform...
17 KB (1,659 words) - 00:33, 20 May 2025
user is hashed and compared with the stored hash. A password reset method is required when password hashing is performed; original passwords cannot be...
49 KB (6,299 words) - 15:10, 30 May 2025
Crypt (C) (category Password authentication)
created during the Password Hashing Competition. The format is defined as: $<id>[$<param>=<value>(,<param>=<value>)*][$<salt>[$<hash>]] where id: an identifier...
28 KB (3,039 words) - 17:30, 30 March 2025
Preimage attack (redirect from Hash preimage)
plaintext of user passwords, an access control system stores a hash of the password. When a user requests access, the password they submit is hashed and compared...
7 KB (895 words) - 15:44, 13 April 2024
Rainbow table (category Cryptographic hash functions)
to compute the hashes using a key derivation function that adds a "salt" to each password before hashing it, with different passwords receiving different...
24 KB (3,485 words) - 02:42, 26 May 2025
Message authentication code (redirect from Keyed hash function)
universal hashing. Intrinsically keyed hash algorithms such as SipHash are also by definition MACs; they can be even faster than universal-hashing based MACs...
16 KB (1,918 words) - 17:55, 22 January 2025
Balloon hashing is a key derivation function presenting proven memory-hard password-hashing and modern design. It was created by Dan Boneh, Henry Corrigan-Gibbs...
3 KB (271 words) - 07:14, 28 May 2025
cryptographic hash function designed by Ross Anderson and Eli Biham in 1995 for efficiency on 64-bit platforms. The size of a Tiger hash value is 192 bits...
9 KB (910 words) - 14:47, 30 September 2023
is a password hashing scheme (PHS) that can also function as a key derivation function (KDF). It gained recognition during the Password Hashing Competition...
18 KB (2,351 words) - 05:31, 1 April 2025
SHA-3: A hash function formerly called Keccak, chosen in 2012 after a public competition among non-NSA designers. It supports the same hash lengths as...
3 KB (464 words) - 07:05, 4 October 2024
Length extension attack (redirect from Hash length extension attack)
means they know the internal state of the hashing function at that point. It is then trivial to initialize a hashing algorithm at that point, input the last...
8 KB (1,082 words) - 12:51, 23 April 2025
9844053f456b4b41e8aa78bbe5c12957bb Argon2, the winner of the Password Hashing Competition, uses BLAKE2b Chef's Habitat deployment system uses BLAKE2b for...
31 KB (2,888 words) - 17:05, 21 May 2025
negligible. When cracking passwords, this method is very fast when used to check all short passwords, but for longer passwords other methods such as the...
21 KB (2,168 words) - 17:09, 27 May 2025
Pepper (cryptography) (category Password authentication)
as a password during hashing with a cryptographic hash function. This value differs from a salt in that it is not stored alongside a password hash, but...
9 KB (1,161 words) - 20:47, 25 May 2025
"signs of weakness". It is deprecated in favor of SHA-256 and other strong hashing algorithms. Nevertheless, as of 2014[update], it remained in use in public...
9 KB (1,053 words) - 04:19, 31 December 2024
Cryptography (section Cryptographic hash functions)
plaintext passwords, computer systems store hashes thereof; then, when a user logs in, the system passes the given password through a cryptographic hash function...
99 KB (10,975 words) - 18:31, 26 May 2025
suggestions, including using Chacha20 instead of Salsa20 and using a universal hashing based MAC for performance. The outcome of this process was the adoption...
13 KB (1,509 words) - 12:59, 26 May 2025