A virtual security switch is a software Ethernet switch with embedded security controls within it that runs within virtual environments such as VMware...
7 KB (850 words) - 20:04, 26 April 2024
access or operation, distinct from a virtual security switch which offers software protection. Security switches should be operated by an authorized user...
5 KB (636 words) - 15:51, 25 April 2025
VXLAN endpoints, which terminate VXLAN tunnels and may be either virtual or physical switch ports, are known as VXLAN tunnel endpoints (VTEPs). VXLAN is an...
7 KB (722 words) - 11:54, 12 July 2025
vSwitch (OVS) is an open-source implementation of a distributed virtual multilayer switch. The main purpose of Open vSwitch is to provide a switching stack...
14 KB (1,152 words) - 16:06, 1 July 2025
guest virtual machine already running, a purpose-built virtual security appliance designed with virtual network security in mind, a virtual switch with...
17 KB (2,108 words) - 02:07, 26 March 2023
VLAN (redirect from Virtual LAN)
logic, within the local area network. Basically, a VLAN behaves like a virtual switch or network link that can share the same physical structure with other...
20 KB (2,720 words) - 07:23, 19 July 2025
Nintendo Switch 2 is a hybrid video game console developed by Nintendo, released in most regions on June 5, 2025. Like the original Switch, it can be...
132 KB (12,682 words) - 00:25, 6 August 2025
VPN (EVPN) is a technology for carrying layer 2 Ethernet traffic as a virtual private network using wide area network protocols. EVPN technologies include...
2 KB (457 words) - 03:35, 18 July 2025
Virtual Cluster Switching (VCS) fabric technology is a Layer 2 proprietary Ethernet technology from Brocade Communications Systems, later acquired by...
4 KB (562 words) - 22:55, 3 September 2024
Network Virtualization using Generic Routing Encapsulation (NVGRE) is a network virtualization technology that attempts to alleviate the scalability problems...
1 KB (132 words) - 11:37, 18 October 2022
Virtual private network (VPN) is a network architecture for virtually extending a private network (i.e. any computer network which is not the public Internet)...
32 KB (3,539 words) - 13:13, 7 August 2025
VLAN hopping (redirect from Switch spoofing)
VLAN hopping is a computer security exploit, a method of attacking networked resources on a virtual LAN (VLAN). The basic concept behind all VLAN hopping...
5 KB (683 words) - 23:24, 23 July 2025
2025, Nintendo announced that the Switch consoles — including the original Switch and its successor – will support Virtual Game Cards. With this feature,...
390 KB (31,128 words) - 05:49, 6 August 2025
Network functions virtualization (NFV) is a network architecture concept that leverages IT virtualization technologies to virtualize entire classes of...
36 KB (3,733 words) - 21:37, 16 July 2025
OVN (Open Virtual Network) is a system to support virtual network abstraction. OVN complements the existing capabilities of Open vSwitch to add native...
4 KB (316 words) - 17:09, 12 July 2024
functions such as Nintendo Switch Online, GameChat (on Nintendo Switch 2), the News, eShop, Album, GameShare, Controller settings, Virtual Game Cards, System...
30 KB (2,953 words) - 05:24, 9 August 2025
including one wherein a computer-animated Scully fights nurses in a virtual hospital. "Kill Switch" deals with various "Gibsonian" themes, including alienation...
21 KB (2,533 words) - 04:57, 16 July 2025
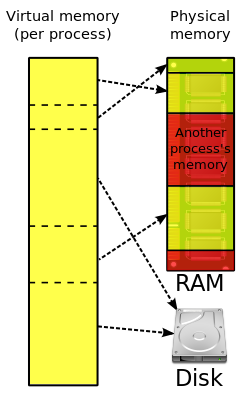
incentive to switch to virtual memory for all systems. The additional capability of providing virtual address spaces added another level of security and reliability...
43 KB (5,351 words) - 14:51, 13 July 2025
packets. Label-switched paths (LSPs) are established by the network operator for a variety of purposes, such as to create network-based IP virtual private networks...
33 KB (4,724 words) - 17:56, 21 July 2025
Nintendo Switch, Xbox One, and Xbox Series X/S released at later dates. In July 2023, free downloadable content titled Ruin was released. Security Breach...
32 KB (3,152 words) - 19:27, 8 August 2025
NordVPN (redirect from Nord Security)
a Lithuanian VPN service founded in 2012. NordVPN is developed by Nord Security (formerly Nordsec Ltd), a cybersecurity software company that was initially...
39 KB (3,632 words) - 00:28, 1 August 2025
OpenFlow (redirect from Openflow Switching Protocol)
controller, and virtual switching and tap monitoring applications. In February 2012, HP said it is supporting the standard on 16 of its Ethernet switch products...
13 KB (1,310 words) - 03:10, 22 July 2025
In computing, a virtual address space (VAS) or address space is the set of ranges of virtual addresses that an operating system makes available to a process...
7 KB (739 words) - 00:25, 12 May 2025
from meeting the performance, availability, security, and mobility requirements of server virtualization. VAL is a product strategy that delivers features...
3 KB (433 words) - 20:22, 10 May 2025
80386 with its virtual 8086 mode became available (as samples since October 1985 and in quantities since June 1986), Digital Research switched to use this...
32 KB (3,263 words) - 05:29, 9 August 2025
MAC flooding (category Computer network security)
employed to compromise the security of network switches. The attack works by forcing legitimate MAC table contents out of the switch and forcing a unicast...
5 KB (622 words) - 06:46, 6 February 2024
VMware (redirect from Virtual Machine Disk Format)
Cisco Systems. One result was the Cisco Nexus 1000V, a distributed virtual software switch, an integrated option in the VMware infrastructure. In April 2011...
99 KB (6,795 words) - 17:04, 25 July 2025
Protection ring (redirect from Ring 0 (computer security))
breaches of security. In addition, the most privileged ring may be given special capabilities (such as real memory addressing that bypasses the virtual memory...
31 KB (3,870 words) - 05:53, 6 August 2025
Operating system (section Virtual memory)
systems, isolating security domains—in the case of operating systems, the kernel, processes, and virtual machines—is key to achieving security. Other ways to...
70 KB (8,177 words) - 07:24, 23 July 2025
Arista Networks (section Ethernet switches)
scripts or send alerts when state changes occur in the switch, such as an interface going down or a virtual machine migrating to another host. Event Monitor...
29 KB (2,580 words) - 14:52, 1 August 2025