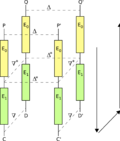
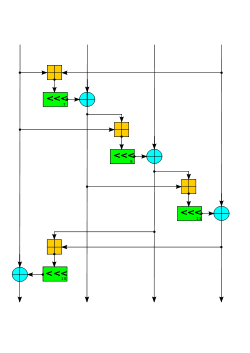
Differential cryptanalysis is a general form of cryptanalysis applicable primarily to block ciphers, but also to stream ciphers and cryptographic hash...
13 KB (1,677 words) - 11:30, 9 March 2025
impossible differential cryptanalysis is a form of differential cryptanalysis for block ciphers. While ordinary differential cryptanalysis tracks differences...
10 KB (850 words) - 15:40, 7 December 2024
In cryptography, linear cryptanalysis is a general form of cryptanalysis based on finding affine approximations to the action of a cipher. Attacks have...
6 KB (812 words) - 13:20, 1 November 2023
higher-order differential cryptanalysis is a generalization of differential cryptanalysis, an attack used against block ciphers. While in standard differential cryptanalysis...
5 KB (783 words) - 05:19, 26 August 2023
Block cipher (section Differential cryptanalysis)
growing catalog of attacks: truncated differential cryptanalysis, partial differential cryptanalysis, integral cryptanalysis, which encompasses square and integral...
51 KB (6,569 words) - 08:42, 11 April 2025
with less complexity than a brute-force search: differential cryptanalysis (DC), linear cryptanalysis (LC), and Davies' attack. However, the attacks are...
60 KB (6,717 words) - 17:36, 25 May 2025
differential cryptanalysis Integral cryptanalysis Linear cryptanalysis Meet-in-the-middle attack Mod-n cryptanalysis Related-key attack Sandwich attack...
44 KB (5,215 words) - 21:55, 19 June 2025
In cryptography, truncated differential cryptanalysis is a generalization of differential cryptanalysis, an attack against block ciphers. Lars Knudsen...
4 KB (318 words) - 10:15, 4 January 2025
Boomerang attack (redirect from Amplified boomerang cryptanalysis)
the boomerang attack is a method for the cryptanalysis of block ciphers based on differential cryptanalysis. The attack was published in 1999 by David...
9 KB (864 words) - 04:16, 17 October 2023
2013-02-19. Eli Biham, Adi Shamir: Differential Cryptanalysis of Feal and N-Hash. EUROCRYPT 1991: 1–16 Bert den Boer, Cryptanalysis of F.E.A.L., EUROCRYPT 1988:...
5 KB (551 words) - 01:40, 17 October 2023
Eli Biham (section Contributions to cryptanalysis)
invented (publicly) differential cryptanalysis, for which he received his Ph.D., while working under Adi Shamir. Differential cryptanalysis - publicly invented...
4 KB (319 words) - 11:00, 3 April 2025
DES-X also increases the strength of DES against differential cryptanalysis and linear cryptanalysis, although the improvement is much smaller than in...
4 KB (533 words) - 09:53, 31 October 2024
IDEA NXT). Unlike differential cryptanalysis, which uses pairs of chosen plaintexts with a fixed XOR difference, integral cryptanalysis uses sets or even...
8 KB (716 words) - 10:14, 4 January 2025
Following the publication of LOKI89, information on the new differential cryptanalysis became available, as well as some early analysis results by (Knudsen...
6 KB (723 words) - 23:05, 27 March 2024
perfect S-box. S-boxes can be analyzed using linear cryptanalysis and differential cryptanalysis in the form of a Linear approximation table (LAT) or...
10 KB (929 words) - 20:28, 24 May 2025
Skipjack (cipher) (section Cryptanalysis)
exhaustive search) within months using impossible differential cryptanalysis. A truncated differential attack was also published against 28 rounds of Skipjack...
12 KB (1,134 words) - 16:36, 18 June 2025
(along with Uriel Feige and Amos Fiat), one of the inventors of differential cryptanalysis and has made numerous contributions to the fields of cryptography...
11 KB (808 words) - 13:17, 17 June 2025
be insecure by Eli Biham and Adi Shamir who were able to use differential cryptanalysis to find hash collisions. The design was then modified by increasing...
2 KB (241 words) - 12:27, 1 October 2024
128-bit blocks and 128-bit keys. This version is susceptible to differential cryptanalysis; for about half the keys, the cipher can be broken with 236 chosen...
6 KB (749 words) - 15:35, 22 November 2023
cryptography, mod n cryptanalysis is an attack applicable to block and stream ciphers. It is a form of partitioning cryptanalysis that exploits unevenness...
3 KB (412 words) - 17:18, 19 December 2024
Salsa20 (section Cryptanalysis of Salsa20)
against differential cryptanalysis. (Specifically, it has no differential characteristic with higher probability than 2−130, so differential cryptanalysis would...
31 KB (3,577 words) - 20:06, 24 October 2024
1994, the differential-linear attack is a mix of both linear cryptanalysis and differential cryptanalysis. The attack utilises a differential characteristic...
4 KB (385 words) - 03:30, 1 February 2024
XTEA (section Cryptanalysis)
Youngdai; Chang, Donghoon; Lee, Wonil; Lee, Sangjin (2004). "Differential Cryptanalysis of TEA and XTEA". In Lim, JI.; Lee, DH. (eds.). Information Security...
9 KB (969 words) - 14:09, 19 April 2025
Twofish (section Cryptanalysis)
is a truncated differential cryptanalysis of the full 16-round version. The paper claims that the probability of truncated differentials is 2−57.3 per...
9 KB (827 words) - 14:21, 3 April 2025
break the cipher in a way that is similar to differential cryptanalysis. The term "rotational cryptanalysis" was coined by Dmitry Khovratovich and Ivica...
3 KB (315 words) - 05:31, 19 February 2025
Cryptography (section Cryptanalysis)
Standard for cryptography. DES was designed to be resistant to differential cryptanalysis, a powerful and general cryptanalytic technique known to the NSA...
99 KB (11,007 words) - 11:28, 7 June 2025
found an attack on one round, and Biham and Shamir (1991) used differential cryptanalysis to attack one round with 2300 encryptions. Biham and Shamir also...
2 KB (301 words) - 21:55, 5 March 2024
are not key-dependent, Khafre XORs subkeys every eight rounds. Differential cryptanalysis is effective against Khafre: 16 rounds can be broken using either...
9 KB (839 words) - 12:48, 9 June 2024
known plaintexts to perform; previous methods of cryptanalysis, such as linear and differential cryptanalysis, often require unrealistically large numbers...
15 KB (1,834 words) - 05:42, 19 February 2025
Madryga (section Cryptanalysis)
non-linear component, and flaws in them are what both differential cryptanalysis and linear cryptanalysis seek to exploit. While Madryga's rotations are data-dependent...
5 KB (717 words) - 21:33, 16 March 2024