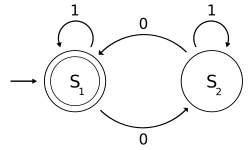
Neural cryptography is a branch of cryptography dedicated to analyzing the application of stochastic algorithms, especially artificial neural network...
15 KB (2,224 words) - 13:07, 12 May 2025
Articles related to cryptography include: A5/1 • A5/2 • ABA digital signature guidelines • ABC (stream cipher) • Abraham Sinkov • Acoustic cryptanalysis...
66 KB (2,911 words) - 02:58, 27 July 2025
Quantum cryptography is the science of exploiting quantum mechanical properties to perform cryptographic tasks. The best known example of quantum cryptography...
82 KB (9,126 words) - 16:08, 3 June 2025
Post-quantum cryptography (PQC), sometimes referred to as quantum-proof, quantum-safe, or quantum-resistant, is the development of cryptographic algorithms...
67 KB (6,893 words) - 20:11, 29 July 2025
Zhu Y, Vargas DV, Sakurai K (November 2018). "Neural Cryptography Based on the Topology Evolving Neural Networks". 2018 Sixth International Symposium...
46 KB (4,240 words) - 19:41, 4 August 2025
Key-agreement protocol (category Cryptography)
In cryptography, a key-agreement protocol is a protocol whereby two (or more) parties generate a cryptographic key as a function of information provided...
12 KB (1,473 words) - 16:52, 18 June 2025
excellence (cum laude) in 2016 and 2017. She plans to pursue a career in neural cryptography.[citation needed] Cheruvu graduated from the Harvard University Extension...
4 KB (448 words) - 19:07, 5 July 2025
Coding theory (section Cryptographic coding)
fitness for specific applications. Codes are used for data compression, cryptography, error detection and correction, data transmission and data storage....
27 KB (3,712 words) - 08:44, 19 June 2025
Quantum neural networks are computational neural network models which are based on the principles of quantum mechanics. The first ideas on quantum neural computation...
21 KB (2,552 words) - 14:29, 18 July 2025
ultrafast physical random number generators, theory of neural networks, neural cryptography, deep learning and synchronization among neurons and lasers...
10 KB (765 words) - 22:20, 7 May 2025
Homomorphic encryption (redirect from Homomorphic cryptography)
Enables Efficient Homomorphic Inference of Deep Neural Networks" (PDF). Cyber Security Cryptography and Machine Learning. Lecture Notes in Computer Science...
42 KB (4,692 words) - 23:00, 1 April 2025
Ron Rivest (section Cryptography)
scientist whose work has spanned the fields of algorithms and combinatorics, cryptography, machine learning, and election integrity. He is an Institute Professor...
27 KB (1,545 words) - 19:15, 28 July 2025
authenticated public classical channel. E91 protocol (1991) is a quantum cryptography method that uses entangled pairs of photons to generate keys for secure...
5 KB (720 words) - 06:35, 18 August 2024
Chaos communications (category Theory of cryptography)
Synchronizing these oscillators is similar to synchronizing random neural nets in neural cryptography. When chaos synchronization is used, a basic scheme of a communications...
3 KB (412 words) - 18:59, 5 September 2024
Obfuscation (software) (redirect from Cryptographic obfuscation)
reverse-engineering the code is cryptographically hard. This is formalized in the many proposals for indistinguishability obfuscation, a cryptographic primitive that,...
18 KB (1,668 words) - 18:48, 29 May 2025
AVX-512 (redirect from Vector Neural Network Instructions)
examples of AVX-512 applications, including media processing, cryptography, video games, neural networks, and even OpenJDK, which employs AVX-512 for sorting...
86 KB (4,691 words) - 05:30, 6 August 2025
Branch predictor (redirect from Neural branch prediction)
Branch predication Branch prediction analysis attacks – on RSA public-key cryptography Instruction unit Cache prefetching Indirect branch control (IBC) Indirect...
40 KB (4,770 words) - 05:30, 6 August 2025
ensemble (cryptography) Ensemble Kalman filter Ensemble learning (statistics and machine learning) Ensembl genome database project Neural ensemble, a...
2 KB (250 words) - 16:33, 6 January 2025
Quantum computing (category Quantum cryptography)
applications during World War II; computers played a major role in wartime cryptography, and quantum physics was essential for nuclear physics used in the Manhattan...
114 KB (12,541 words) - 06:48, 6 August 2025
Theoretical computer science (section Cryptography)
computation, quantum computation, automata theory, information theory, cryptography, program semantics and verification, algorithmic game theory, machine...
42 KB (4,803 words) - 23:57, 1 June 2025
cryptography, with his work described as "a turning point, and marked the closure of classical cryptography and the beginning of modern cryptography"...
82 KB (8,334 words) - 12:08, 31 July 2025
Echo state network (category Neural network architectures)
state network (ESN) is a type of reservoir computer that uses a recurrent neural network with a sparsely connected hidden layer (with typically 1% connectivity)...
13 KB (1,748 words) - 21:08, 2 August 2025
Johnny Mnemonic (film) (redirect from Neural Attenuation Syndrome)
Johnny Mnemonic is a 1995 cyberpunk action film directed by Robert Longo in his feature directorial debut. William Gibson, who wrote the 1981 short story...
49 KB (5,098 words) - 09:45, 1 August 2025
Entanglement swapping (section Quantum cryptography)
projects a quantum state onto this basis set.: 813 In the field of quantum cryptography, it helps secure communication channels better. By utilizing swapped...
11 KB (1,108 words) - 00:34, 26 May 2025
2025-02-24. Goldreich, Oded, ed. (2019). Providing Sound Foundations for Cryptography: On the Work of Shafi Goldwasser and Silvio Micali. Association for Computing...
5 KB (386 words) - 06:16, 21 July 2025
Authentication Code, a cryptographic algorithm. CMAC may also refer to: Cerebellar model articulation controller, type of neural network Continuous monitoring...
763 bytes (117 words) - 00:19, 17 October 2023
foundations of computational complexity theory and its application to cryptography and program checking". Blum was born to a Jewish family in Venezuela...
10 KB (740 words) - 13:23, 24 July 2025
usually referred to with a more specific term, such as 3D accelerator, or cryptographic accelerator. Traditionally, processors were sequential (instructions...
21 KB (1,876 words) - 12:58, 30 July 2025
Decorrelation (section Cryptography)
temporal (handling of movement in the lateral geniculate nucleus). In cryptography, decorrelation is used in cipher design (see Decorrelation theory) and...
4 KB (457 words) - 06:59, 30 July 2025
Quantum key distribution (category Quantum cryptography)
distribution (QKD) is a secure communication method that implements a cryptographic protocol involving components of quantum mechanics. It enables two parties...
104 KB (11,929 words) - 03:48, 2 August 2025