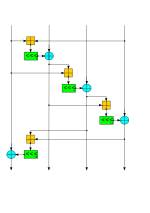
Panama is a cryptographic primitive which can be used both as a hash function and a stream cipher, but its hash function mode of operation has been broken...
4 KB (350 words) - 00:49, 27 September 2023
Cryptography, or cryptology (from Ancient Greek: κρυπτός, romanized: kryptós "hidden, secret"; and γράφειν graphein, "to write", or -λογία -logia, "study"...
98 KB (10,714 words) - 21:22, 25 May 2024
and topical guide to cryptography: Cryptography (or cryptology) – practice and study of hiding information. Modern cryptography intersects the disciplines...
20 KB (1,876 words) - 10:47, 24 February 2024
Articles related to cryptography include: A5/1 • A5/2 • ABA digital signature guidelines • ABC (stream cipher) • Abraham Sinkov • Acoustic cryptanalysis...
67 KB (2,943 words) - 23:51, 25 November 2023
Symmetric-key algorithm (redirect from Symmetric key cryptography)
Symmetric-key algorithms are algorithms for cryptography that use the same cryptographic keys for both the encryption of plaintext and the decryption of...
15 KB (1,544 words) - 16:02, 13 May 2024
The tables below compare cryptography libraries that deal with cryptography algorithms and have application programming interface (API) function calls...
42 KB (1,389 words) - 11:12, 20 May 2024
Look up Panama, Panamá, Panamà, or panama in Wiktionary, the free dictionary. Panama (or Panamá) is a republic in Central America. Panama may also refer...
3 KB (398 words) - 01:02, 10 November 2023
SEAL (cipher) (redirect from SEAL (cryptography))
In cryptography, SEAL (Software-Optimized Encryption Algorithm) is a stream cipher optimised for machines with a 32-bit word size and plenty of RAM with...
1 KB (140 words) - 01:11, 14 November 2023
ISAAC (cipher) (redirect from ISAAC (cryptography))
ISAAC (indirection, shift, accumulate, add, and count) is a cryptographically secure pseudorandom number generator and a stream cipher designed by Robert...
5 KB (546 words) - 02:33, 17 October 2023
following tables compare general and technical information for a number of cryptographic hash functions. See the individual functions' articles for further information...
16 KB (785 words) - 15:03, 26 January 2024
Pike (cipher) (redirect from Pike (cryptography))
v t e Cryptography General History of cryptography Outline of cryptography Cryptographic protocol Authentication protocol Cryptographic primitive Cryptanalysis...
923 bytes (100 words) - 12:41, 15 May 2022
In cryptographic protocol design, cryptographic agility or crypto-agility is the ability to switch between multiple cryptographic primitives. Then the...
9 KB (909 words) - 12:35, 30 December 2023
A5/1 (redirect from A5 (cryptography))
"Conditional Estimators: An Effective Attack on A5/1". Selected Areas in Cryptography 2005: 1–19. Barkan, Elad; Eli Biham; Nathan Keller (2003). "Instant Ciphertext-Only...
23 KB (2,676 words) - 12:41, 21 January 2024
In cryptography, RC4 (Rivest Cipher 4, also known as ARC4 or ARCFOUR, meaning Alleged RC4, see below) is a stream cipher. While it is remarkable for its...
44 KB (5,058 words) - 05:30, 15 April 2024
(TLS) RFC 8103: Using ChaCha20-Poly1305 Authenticated Encryption in the Cryptographic Message Syntax (CMS) Nir, Yoav; Langley, Adam (June 2018). ChaCha20...
14 KB (1,425 words) - 04:21, 21 May 2024
Block cipher mode of operation (category Cryptographic algorithms)
In cryptography, a block cipher mode of operation is an algorithm that uses a block cipher to provide information security such as confidentiality or authenticity...
52 KB (5,906 words) - 08:12, 7 April 2024
implementation is still feasible. MULTI-S01 with the PRNG Panama was among the cryptographic techniques recommended for Japanese government use by CRYPTREC...
3 KB (341 words) - 15:28, 20 August 2022
Initialization vector (category Cryptography)
In cryptography, an initialization vector (IV) or starting variable is an input to a cryptographic primitive being used to provide the initial state....
14 KB (1,779 words) - 08:47, 29 April 2024
Stream cipher (category Cryptographic primitives)
seed value using digital shift registers. The seed value serves as the cryptographic key for decrypting the ciphertext stream. Stream ciphers represent a...
23 KB (2,217 words) - 13:45, 7 May 2024
Salsa20 (category Cryptographically secure pseudorandom number generators)
designed in 2005, then later submitted to the eSTREAM European Union cryptographic validation process by Bernstein. ChaCha is a modification of Salsa20...
31 KB (3,563 words) - 13:19, 22 May 2024
In cryptography, a keystream is a stream of random or pseudorandom characters that are combined with a plaintext message to produce an encrypted message...
3 KB (259 words) - 08:45, 30 January 2023
In cryptography, MUGI is a pseudorandom number generator (PRNG) designed for use as a stream cipher. It was among the cryptographic techniques recommended...
5 KB (588 words) - 08:56, 27 April 2022
Turing (cipher) (category Cryptography stubs)
ISBN 3540204490. Matsui, Mitsuru; Zuccherato, Robert (2004). Selected Areas in Cryptography: 10th Annual International Workshop, SAC 2003, Ottawa, Canada, August...
3 KB (328 words) - 04:03, 10 April 2024
Naval Base Panama Canal Zone refers to a number of United States Navy bases used during World War II to both protect the Panama Canal and the key shipping...
40 KB (4,744 words) - 07:47, 19 May 2024
Hash function security summary (category Cryptography lists and comparisons)
This article summarizes publicly known attacks against cryptographic hash functions. Note that not all entries may be up to date. For a summary of other...
17 KB (1,055 words) - 12:18, 2 March 2023
Stream cipher attacks (category Cryptographic attacks)
v t e Cryptography General History of cryptography Outline of cryptography Cryptographic protocol Authentication protocol Cryptographic primitive Cryptanalysis...
7 KB (1,029 words) - 04:31, 17 October 2023
SHA-3 (category Cryptographic hash functions)
MD5-like structure of SHA-1 and SHA-2. SHA-3 is a subset of the broader cryptographic primitive family Keccak (/ˈkɛtʃæk/ or /ˈkɛtʃɑːk/), designed by Guido...
51 KB (5,620 words) - 14:24, 19 April 2024
Crypto++ (category Cryptographic software)
libcrypto++, and libcryptopp) is a free and open-source C++ class library of cryptographic algorithms and schemes written by Wei Dai. Crypto++ has been widely...
19 KB (1,314 words) - 19:15, 16 February 2024
RadioGatún (category Cryptographic hash functions)
RadioGatún is a cryptographic hash primitive created by Guido Bertoni, Joan Daemen, Michaël Peeters, and Gilles Van Assche. It was first publicly presented...
12 KB (1,551 words) - 17:40, 29 October 2023
CryptMT (category Cryptography stubs)
In cryptography, CryptMT is a stream cipher algorithm which internally uses the Mersenne twister. It was developed by Makoto Matsumoto, Mariko Hagita,...
917 bytes (79 words) - 18:17, 29 April 2024