group theory, the Pohlig–Hellman algorithm, sometimes credited as the Silver–Pohlig–Hellman algorithm, is a special-purpose algorithm for computing discrete...
7 KB (1,035 words) - 18:44, 19 October 2024
order of G should have a large prime factor to prevent use of the Pohlig–Hellman algorithm to obtain a or b. For this reason, a Sophie Germain prime q is...
47 KB (5,306 words) - 20:14, 6 August 2025
his subsequent work in cryptography with Steve Pohlig (the Pohlig–Hellman algorithm) and others. Hellman addresses the National Security Agency’s (NSA)...
17 KB (1,554 words) - 21:08, 25 July 2025
Diffie-Hellman key exchange, including the Pohlig–Hellman exponentiation cipher and the Pohlig–Hellman algorithm for computing discrete logarithms. That cipher...
3 KB (248 words) - 09:37, 31 May 2025
Baby-step giant-step Index calculus algorithm Pohlig–Hellman algorithm Pollard's rho algorithm for logarithms Euclidean algorithm: computes the greatest common...
72 KB (7,951 words) - 17:13, 5 June 2025
Baby-step giant-step (category Number theoretic algorithms)
the Pohlig–Hellman algorithm has a smaller algorithmic complexity, and potentially solves the same problem. The baby-step giant-step algorithm is a generic...
7 KB (1,061 words) - 19:23, 24 January 2025
the Diffie-Hellman cryptosystem which relies on the discrete logarithm. Merkle's Stanford University dissertation (1979) was credited by Pohlig (1977) and...
11 KB (1,763 words) - 17:23, 21 June 2025
Discrete logarithm (section Algorithms)
Index calculus algorithm Number field sieve Pohlig–Hellman algorithm Pollard's rho algorithm for logarithms Pollard's kangaroo algorithm (aka Pollard's...
18 KB (2,690 words) - 20:56, 4 August 2025
{O}}({\sqrt {n}})} . If used together with the Pohlig–Hellman algorithm, the running time of the combined algorithm is O ( p ) {\displaystyle {\mathcal {O}}({\sqrt...
7 KB (1,187 words) - 18:02, 2 August 2024
phenomena, then Shor's algorithm could be used to break public-key cryptography schemes, such as The RSA scheme The finite-field Diffie–Hellman key exchange The...
40 KB (5,809 words) - 20:55, 1 August 2025
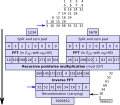
multiplication algorithm is an algorithm (or method) to multiply two numbers. Depending on the size of the numbers, different algorithms are more efficient...
47 KB (6,886 words) - 11:27, 22 July 2025
The Tonelli–Shanks algorithm (referred to by Shanks as the RESSOL algorithm) is used in modular arithmetic to solve for r in a congruence of the form r2...
19 KB (3,751 words) - 01:15, 9 July 2025
his subsequent work in cryptography with Steve Pohlig (the Pohlig–Hellman algorithm) and others. Hellman addresses the National Security Agency's (NSA)...
28 KB (2,912 words) - 23:08, 26 May 2025
The Karatsuba algorithm is a fast multiplication algorithm for integers. It was discovered by Anatoly Karatsuba in 1960 and published in 1962. It is a...
13 KB (2,046 words) - 20:43, 4 May 2025
chip used a data encryption algorithm called Skipjack to transmit information and the Diffie–Hellman key exchange-algorithm to distribute the public keys...
18 KB (1,895 words) - 22:40, 6 August 2025
and computer programming, the extended Euclidean algorithm is an extension to the Euclidean algorithm, and computes, in addition to the greatest common...
28 KB (4,467 words) - 20:39, 9 June 2025
theory, Williams's p + 1 algorithm is an integer factorization algorithm, one of the family of algebraic-group factorisation algorithms. It was invented by...
5 KB (831 words) - 21:06, 30 September 2022
Integer square root (category Number theoretic algorithms)
y {\displaystyle y} and k {\displaystyle k} be non-negative integers. Algorithms that compute (the decimal representation of) y {\displaystyle {\sqrt {y}}}...
26 KB (3,191 words) - 07:11, 19 May 2025
Solovay–Strassen primality test (redirect from Solovay-Strassen algorithm)
composite return probably prime Using fast algorithms for modular exponentiation, the running time of this algorithm is O(k·log3 n), where k is the number...
10 KB (1,518 words) - 08:52, 27 June 2025
The binary GCD algorithm, also known as Stein's algorithm or the binary Euclidean algorithm, is an algorithm that computes the greatest common divisor...
17 KB (1,993 words) - 13:05, 28 January 2025
Pollard's rho algorithm is an algorithm for integer factorization. It was invented by John Pollard in 1975. It uses only a small amount of space, and...
13 KB (1,755 words) - 06:12, 18 April 2025
The Schönhage–Strassen algorithm is an asymptotically fast multiplication algorithm for large integers, published by Arnold Schönhage and Volker Strassen...
26 KB (4,580 words) - 11:43, 4 June 2025
Integer factorization (redirect from Prime factorization algorithm)
efficient non-quantum integer factorization algorithm is known. However, it has not been proven that such an algorithm does not exist. The presumed difficulty...
25 KB (2,977 words) - 21:02, 19 June 2025
Pollard's p − 1 algorithm is a number theoretic integer factorization algorithm, invented by John Pollard in 1974. It is a special-purpose algorithm, meaning...
9 KB (1,251 words) - 18:33, 16 April 2025
Sieve of Eratosthenes (category Algorithms)
In mathematics, the sieve of Eratosthenes is an ancient algorithm for finding all prime numbers up to any given limit. It does so by iteratively marking...
24 KB (3,056 words) - 20:26, 5 July 2025
Modular exponentiation (category Cryptographic algorithms)
the field of public-key cryptography, where it is used in both Diffie–Hellman key exchange and RSA public/private keys. Modular exponentiation is the...
21 KB (2,759 words) - 02:20, 29 June 2025
Primality test (category Asymmetric-key algorithms)
A primality test is an algorithm for determining whether an input number is prime. Among other fields of mathematics, it is used for cryptography. Unlike...
27 KB (3,833 words) - 09:23, 3 May 2025
difficult, but in this case it can be done efficiently using the Pohlig–Hellman algorithm because M {\displaystyle M} is a smooth number. A test site is...
10 KB (1,045 words) - 00:43, 17 March 2025
In computational number theory, Cipolla's algorithm is a technique for solving a congruence of the form x 2 ≡ n ( mod p ) , {\displaystyle x^{2}\equiv...
13 KB (3,042 words) - 05:54, 24 June 2025
AKS primality test (redirect from AKS algorithm)
primality test and cyclotomic AKS test) is a deterministic primality-proving algorithm created and published by Manindra Agrawal, Neeraj Kayal, and Nitin Saxena...
20 KB (2,447 words) - 13:22, 18 June 2025