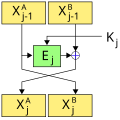
Advanced Encryption Standard uses a key schedule to expand a short key into a number of separate round keys. The three AES variants have a different number...
6 KB (974 words) - 11:24, 26 May 2025
Advanced Encryption Standard (redirect from AES Key)
KeyExpansion – round keys are derived from the cipher key using the AES key schedule. AES requires a separate 128-bit round key block for each round plus...
50 KB (5,678 words) - 12:38, 4 June 2025
cipher key called a round key. A key schedule is an algorithm that calculates all the round keys from the key. Some ciphers have simple key schedules. For...
3 KB (402 words) - 08:19, 29 May 2025
(Pentium+) System 22–29 0x3FC0 0000 — Reserved — 30 0x4000 0000 (none) AES key schedule loaded flag (CPUs with VIA PadLock only) System 31 0x8000 0000 AI Alternate...
9 KB (805 words) - 01:16, 14 April 2025
AES-128 and AES-256 GPG, GPL-licensed, includes AES, AES-192, and AES-256 as options. IPsec IronKey Uses AES 128-bit and 256-bit CBC-mode hardware encryption...
12 KB (1,295 words) - 05:00, 19 May 2025
identified by the group order of the authentication key H (for AES-GCM, H is derived from the encryption key by encrypting the zero block). RSA and DSA. August...
9 KB (1,302 words) - 16:51, 26 March 2025
related-key attacks altogether, usually by incorporating a strong key schedule. A newer version of Wi-Fi Protected Access, WPA2, uses the AES block cipher...
5 KB (688 words) - 10:33, 3 January 2025
number of rounds and the key schedule. More recent versions – SAFER+ and SAFER++ – were submitted as candidates to the AES process in 1998 and the NESSIE...
7 KB (842 words) - 16:23, 27 May 2025
time to decode a 256 bit AES cipher as it would a conventional computer to decode a 128 bit AES cipher. For this reason, AES-256 is believed to be "quantum...
15 KB (1,540 words) - 19:12, 22 April 2025
Advanced Encryption Standard process (redirect from AES process)
Nominations for AES". csrc.nist.gov. September 12, 1997. Retrieved October 9, 2018. Georgoudis, Dianelos. "Live from the Second AES Conference, day 1"...
10 KB (1,040 words) - 10:14, 4 January 2025
into a symmetric key for use with AES. Keyed cryptographic hash functions are popular examples of pseudorandom functions used for key derivation. The first[citation...
13 KB (1,640 words) - 18:48, 30 April 2025
security, roughly a DES equivalent. This is one of the reasons why AES supports key lengths of 256 bits and longer. IBM's Lucifer cipher was selected in...
29 KB (3,222 words) - 03:31, 9 April 2025
cipher "Webpage for the AES-GCM-SIV Mode of Operation". 31 May 2023. Gueron, S.; Langley, A.; Lindell, Y. (April 2019). AES-GCM-SIV: Nonce Misuse-Resistant...
4 KB (398 words) - 12:58, 8 January 2025
Galois/Counter Mode (redirect from AES-GCM)
Schwabe described a "Faster and Timing-Attack Resistant AES-GCM" that achieves 10.68 cycles per byte AES-GCM authenticated encryption on 64-bit Intel processors...
23 KB (3,051 words) - 20:21, 24 March 2025
Serpent (cipher) (section Key schedule)
Serpent-1, was submitted to the AES competition. The AES submission paper discusses the changes, which include key-scheduling differences. The XSL attack...
16 KB (1,962 words) - 07:47, 17 April 2025
prepare for the completion of the AES process. UES was designed with the same interface as AES: a block size of 128 bits and key size of 128, 192, or 256 bits...
2 KB (128 words) - 11:25, 22 May 2025
AES; however, this attack does not threaten the security of IDEA in practice. The very simple key schedule makes IDEA subject to a class of weak keys;...
12 KB (1,499 words) - 19:07, 14 April 2024
Block cipher mode of operation (redirect from AES-CBC)
encryption for 1/256 of keys. OFB-8 encryption returns the plaintext unencrypted for affected keys. Some modes (such as AES-SIV and AES-GCM-SIV) are built...
52 KB (5,828 words) - 20:04, 23 May 2025
Authenticated encryption (redirect from Key commitment)
"oracle", a key-committing AEAD that does not allow this type of crafted messages to exist can be used. AEGIS is an example of fast (if the AES instruction...
19 KB (2,104 words) - 02:40, 30 May 2025
SM4 (cipher) (section Keys and key parameters)
Standard (AES), the S-box is based on the multiplicative inverse over GF(28). The affine transforms and polynomial bases are different from that of AES, but...
9 KB (958 words) - 16:44, 2 February 2025
example, AES-128 (key size 128 bits) is designed to offer a 128-bit security level, which is considered roughly equivalent to a RSA using 3072-bit key. In...
13 KB (1,332 words) - 01:56, 12 March 2025
Whiting (2000-04-07). "A Performance Comparison of the Five AES Finalists" (PDF/PostScript). Third AES Candidate Conference. Retrieved 2013-01-14. Schneier,...
9 KB (827 words) - 14:21, 3 April 2025
InvMixColumns and AddRoundKey steps in the opposite order of what the AES specification (FIPS 197) indicates. As a result of this, the AES round key provided as the...
35 KB (1,750 words) - 00:50, 3 March 2025
substitution–permutation network structure based on AES. The interface is the same as AES: 128-bit block size with key size of 128, 192, or 256 bits. The number...
5 KB (380 words) - 18:00, 4 December 2024
Vaudenay) and submitted to the AES competition. Like other AES candidates, DFC operates on blocks of 128 bits, using a key of 128, 192, or 256 bits. It...
4 KB (397 words) - 07:03, 27 April 2022
relatively slow among AES candidates. Ladder-DES Luby–Rackoff block cipher John Kelsey, Bruce Schneier (August 1999). Key-Schedule Cryptanalysis of DEAL...
2 KB (185 words) - 07:36, 29 April 2025
company, to the AES competition as a candidate to become the Advanced Encryption Standard. Wagner et al. (1999) found a number of weak key classes for FROG...
5 KB (609 words) - 07:46, 24 June 2023
Differential cryptanalysis (redirect from Degenerate Key)
differential attack requires as much work to determine the key as simply brute forcing the key. The AES non-linear function has a maximum differential probability...
13 KB (1,677 words) - 11:30, 9 March 2025
Hasty Pudding cipher (section Key expansion)
Advanced Encryption Standard (AES). It has a number of unusual properties for a block cipher: its input block size and key length are variable, and it includes...
11 KB (1,315 words) - 04:17, 28 November 2024
appropriately, and that they targeted AES's security margin.: 17 Simon includes a round counter in the key schedule. The designers state this was included...
18 KB (1,841 words) - 00:06, 14 November 2024