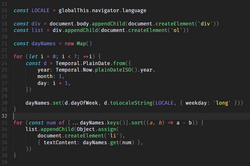
A number of computer operating systems employ security features to help prevent malicious software from gaining sufficient privileges to compromise the...
24 KB (2,340 words) - 15:11, 30 March 2024
roughshod over ordinary users. Unix security List of Unix commands Comparison of privilege authorization features "From Novice to Master, and Back Again". D-Mac's...
7 KB (655 words) - 00:08, 21 May 2025
software portal chroot doas runas Comparison of privilege authorization features Miller, Todd C. "A Brief History of Sudo". Archived from the original...
21 KB (1,766 words) - 19:47, 25 May 2025
User Account Control (section Features)
article as "...one of the worst pieces of technical advice ever issued." Comparison of privilege authorization features Features new to Windows Vista...
31 KB (3,569 words) - 13:33, 14 April 2025
invoked if setting of the username succeeds. Comparison of privilege authorization features sudo doas Principle of least privilege User Account Control...
6 KB (559 words) - 12:24, 4 July 2024
tables provide a comparison of operating systems, of computer devices, as listing general and technical information for a number of widely used and currently...
80 KB (1,736 words) - 19:15, 24 May 2025
E-commerce identification and identification types (section Identification, authentication and authorization)
three-step process of identification, authentication and authorization. Today, a high level of trust is as critical to eCommerce transactions as it is...
15 KB (1,974 words) - 20:24, 12 January 2025
Internet Information Services (section Features)
additional or enhanced security features: Client certificate mapping IP security Request filtering URL authorization Authentication changed slightly between...
35 KB (3,633 words) - 13:12, 31 March 2025
Windows Vista (section New or changed features)
and program incompatibility; digital rights management; excessive authorization from the new User Account Control; inordinately high system requirements...
172 KB (16,919 words) - 22:13, 12 June 2025
modification, or denial of a computer network and network-accessible resources. Network security involves the authorization of access to data in a network...
49 KB (5,235 words) - 08:16, 15 June 2025
JavaScript (redirect from Features of JavaScript)
application with the privileges of the victim, potentially disclosing secret information or transferring money without the victim's authorization. One important...
84 KB (7,900 words) - 22:09, 11 June 2025
Dormant Commerce Clause (category Legal history of the United States)
business privilege tax imposed on the privilege of doing business in interstate commerce. But then, in the second, Virginia revised the wording of its statute...
49 KB (7,148 words) - 18:04, 25 May 2025
Dementia with Lewy bodies (redirect from Dementia of the Lewy body type)
device' authorization for CSF testing, these tests are not widely available and their role in clinical practice has not been established as of 2022. Other...
135 KB (14,436 words) - 12:01, 25 May 2025
MediaWiki (redirect from History of MediaWiki)
of MediaWiki. Installation of MediaWiki requires that the user have administrative privileges on a server running both PHP and a compatible type of SQL...
102 KB (9,752 words) - 20:16, 19 June 2025
allocate private regions of memory, called enclaves, which are designed to be protected from processes running at higher privilege levels. A TEE as an isolated...
34 KB (3,148 words) - 17:02, 16 June 2025
Database (redirect from List of database servers)
alerting, statistics gathering and authorization. Many databases provide active database features in the form of database triggers. A cloud database...
78 KB (9,882 words) - 23:59, 9 June 2025
Rootkit (category Privilege escalation exploits)
direct access to the system with administrative privileges, bypassing standard authentication and authorization mechanisms. Conceal other malware, notably...
69 KB (7,095 words) - 01:49, 26 May 2025
Propaganda (section Comparisons with disinformation)
Foreign Relations Authorization Act of 1987, allowing for materials produced by the State Department and the Broadcasting Board of Governors (BBG) to...
91 KB (10,700 words) - 19:57, 23 June 2025
Intel Active Management Technology (category Out-of-band management)
card and the corporate version of the Intel Management Engine binary. Intel confirmed a Remote Elevation of Privilege bug (CVE-2017-5689, SA-00075) in...
62 KB (6,360 words) - 09:05, 27 May 2025
Multilevel security (redirect from Multiple Levels of Security)
security mechanism, a Biba integrity mechanism, a privilege replacement for superuser, and many other features. PitBull has the security base for General Dynamics'...
31 KB (4,178 words) - 04:23, 8 March 2025
operating system kernel examines these security attributes, examines the authorization rules (aka policy) in place, and decides whether to grant access. A...
23 KB (2,601 words) - 13:55, 24 May 2025
Example: Mechanism: User login attempts are routed to an authorization server Policy: Authorization server requires a password which is verified against stored...
83 KB (10,153 words) - 05:39, 23 June 2025
Sephardic Jews (redirect from History of Sephardic Jews)
1478, the Catholic Monarchs, Ferdinand II of Aragon and Isabella I of Castile, received papal authorization to establish the Spanish Inquisition as a...
179 KB (20,139 words) - 23:22, 17 June 2025
George Floyd protests (redirect from Protests over the death of George Floyd)
Confederate States of America in the National Defense Authorization Act for Fiscal Year 2021. President Trump cited this provision in his veto of the NDAA, resulting...
307 KB (28,260 words) - 16:35, 12 June 2025
Nakba (category History of the Jews in Palestine (region))
steered by these officers, with Ben-Gurion's authorization, through the campaign ... [p. 769] The use of the bacteria was apparently fairly limited in...
355 KB (49,535 words) - 19:42, 21 June 2025
add entries that would then be "fed into the Nupedia process" of authorization. Most of Nupedia's expert volunteers, however, wanted nothing to do with...
222 KB (20,787 words) - 11:09, 3 June 2025
unsigned code. The second requirement is privilege escalation, typically compromising the kernel, unlocking secure parts of the system. Depending on the security...
41 KB (5,511 words) - 03:12, 19 June 2025
Big Brother Brasil 24 (section Expanded HoH privileges)
though she had received prior authorization from the production. In the same intervention, Tadeu pointed out that Davi's ideas of revenge against the participant...
124 KB (6,895 words) - 19:31, 16 June 2025
Guantanamo Bay detention camp (redirect from Gulag of our times)
strengthened the hand of our enemies, and compromised our moral authority. On 14 September 2001, Congress passed the Authorization for Use of Military Force...
293 KB (29,516 words) - 21:53, 23 June 2025