computer networking, IP address spoofing or IP spoofing is the creation of Internet Protocol (IP) packets with a false source IP address, for the purpose...
9 KB (1,161 words) - 03:41, 13 May 2025
networking, ARP spoofing (also ARP cache poisoning or ARP poison routing) is a technique by which an attacker sends (spoofed) Address Resolution Protocol...
19 KB (1,558 words) - 09:03, 24 May 2025
NIC has the MAC address of a user's choosing. The process of masking a MAC address is known as MAC spoofing. Essentially, MAC spoofing entails changing...
11 KB (1,345 words) - 03:43, 14 April 2025
host. IP spoofing and ARP spoofing in particular may be used to leverage man-in-the-middle attacks against hosts on a computer network. Spoofing attacks...
32 KB (3,674 words) - 16:39, 25 May 2025
Address spoofing may refer to: IP address spoofing MAC spoofing This disambiguation page lists articles associated with the title Address spoofing. If...
102 bytes (42 words) - 16:23, 11 December 2019
the MAC address associated with an IP address. The host broadcasts a request containing the node's IP address, and the node with that IP address replies...
20 KB (2,966 words) - 04:27, 29 April 2025
causing the name server to return an incorrect result record, e.g. an IP address. This results in traffic being diverted to any computer that the attacker...
13 KB (1,517 words) - 21:37, 25 May 2025
packets in multicast routing and to help prevent IP address spoofing in unicast routing. In standard unicast IP routing, the router forwards the packet away...
8 KB (1,248 words) - 02:30, 23 October 2024
Martian packet (category IP addresses)
in RFC 1812, Section 5.3.7 (Martian Address Filtering). Martian packets commonly arise from IP address spoofing in denial-of-service attacks, but can...
5 KB (531 words) - 20:25, 19 December 2024
Domain name (redirect from Fake IP address)
for malicious purposes. The term Domain name spoofing (or simply though less accurately, Domain spoofing) is used generically to describe one or more...
54 KB (6,230 words) - 14:53, 25 May 2025
authentication of the source IP address of an IP packet, enabling the source address to be falsified in a strategy called IP address spoofing, and creating potential...
17 KB (2,496 words) - 15:18, 13 September 2024
a countermeasure against various spoofing attacks where the attacker's packets contain fake IP addresses. Spoofing is often used in denial-of-service...
7 KB (858 words) - 12:19, 22 July 2023
network ARP spoofing Caller ID spoofing E-mail spoofing IP address spoofing MAC spoofing Referrer spoofing SMS spoofing Spoofed URL Website spoofing Meaconing...
1 KB (198 words) - 20:52, 8 November 2022
Caller ID spoofing is a spoofing attack which causes the telephone network's Caller ID to indicate to the receiver of a call that the originator of the...
32 KB (3,593 words) - 02:58, 26 May 2025
the server to obtain an IP address and Default Gateway address. DHCP Servers are normally provided by Internet Service Providers (ISPs). ARP spoofing...
3 KB (354 words) - 01:07, 29 November 2024
Denial-of-service attack (section ARP spoofing)
augmentation of a DDoS, attacks may involve forging of IP sender addresses (IP address spoofing) further complicating identifying and defeating the attack...
99 KB (11,454 words) - 14:51, 22 May 2025
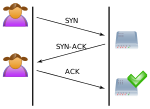
the expected ACK, or by spoofing the source IP address in the SYN, cause the server to send the SYN-ACK to a falsified IP address – which will not send...
4 KB (430 words) - 16:43, 9 February 2025
Email spoofing is the creation of email messages with a forged sender address. The term applies to email purporting to be from an address which is not...
22 KB (2,407 words) - 15:58, 26 May 2025
code injection, SQL injections, cross-site scripting, exploits, IP address spoofing, forensics, and other hacking techniques. Wargames are also used...
4 KB (326 words) - 12:13, 2 June 2024
Computer security (section Spoofing)
parties by spoofing one or both party's identities and injecting themselves in-between. Types of MITM attacks include: IP address spoofing is where the...
220 KB (22,314 words) - 20:25, 29 May 2025
IPv4 (redirect from IPv4 address)
about IP address assignments. The Internet Engineering Task Force (IETF) and IANA have restricted from general use various reserved IP addresses for special...
42 KB (5,618 words) - 02:28, 21 May 2025
Private network (redirect from Private IP address)
private network is a computer network that uses a private address space of IP addresses. These addresses are commonly used for local area networks (LANs) in...
11 KB (1,572 words) - 18:50, 25 May 2025
Geotargeting (redirect from IP targeting)
"Cloaking" via IP delivery is different from cloaking via "user agent". While IP address spoofing is harder and more reliable than user-agent spoofing, it is...
12 KB (1,258 words) - 00:10, 31 May 2024
massive quantities of messages at devices owned by others using IP address spoofing. Devices exploited in the attack may be as simple as a cable converter...
41 KB (4,024 words) - 01:59, 10 May 2025
establishing a network connection. Changing MAC addresses is necessary in network virtualization. In MAC spoofing, this is practiced in exploiting security...
32 KB (3,810 words) - 02:07, 22 May 2025
Bogon filtering (redirect from Bogon (address))
Reverse-path forwarding IP hijacking IP address spoofing Ingress filtering Internet background noise "What is a bogon address?". APNIC. Retrieved 1 November...
6 KB (663 words) - 00:06, 1 November 2024
Hostname IP address blocking IP address spoofing IP aliasing IP multicast List of assigned /8 IPv4 address blocks Reverse DNS lookup Virtual IP address WHOIS...
32 KB (4,384 words) - 04:29, 26 May 2025
it runs over TCP or UDP, SNMPv1 and v2 are vulnerable to IP spoofing attacks. With spoofing, attackers may bypass device access lists in agents that are...
40 KB (5,090 words) - 15:40, 22 May 2025
email address, such as [email protected], is made up from a local-part, the symbol @, and a domain, which may be a domain name or an IP address enclosed...
35 KB (4,166 words) - 05:22, 24 May 2025
to obtain many at low cost through techniques such as SMS spoofing or IP address spoofing. Use of such identity proxies can also exclude those without...
22 KB (2,492 words) - 20:57, 21 October 2024