should resist attacks on its preimage (set of possible inputs). In the context of attack, there are two types of preimage resistance: preimage resistance:...
7 KB (895 words) - 15:44, 13 April 2024
Collision attack Preimage attack Length extension attack Cipher security summary Tao Xie; Fanbao Liu; Dengguo Feng (25 March 2013). "Fast Collision Attack on...
17 KB (1,063 words) - 06:46, 25 May 2025
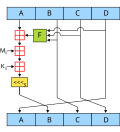
Merkle tree (section Second preimage attack)
root does not indicate the tree depth, enabling a second-preimage attack in which an attacker creates a document other than the original that has the same...
15 KB (1,822 words) - 16:33, 18 June 2025
collision attack on a cryptographic hash tries to find two inputs producing the same hash value, i.e. a hash collision. This is in contrast to a preimage attack...
17 KB (2,047 words) - 14:32, 21 June 2025
MD5 (redirect from MD5 attack)
computing cluster. In April 2009, an attack against MD5 was published that breaks MD5's preimage resistance. This attack is only theoretical, with a computational...
46 KB (4,710 words) - 10:55, 16 June 2025
extend the attack to the full MD2. The described collisions was published in 1997. In 2004, MD2 was shown to be vulnerable to a preimage attack with time...
9 KB (1,053 words) - 04:19, 31 December 2024
under a royalty-free license. As of 2011,[update] the best public attacks break preimage resistance for 52 out of 64 rounds of SHA-256 or 57 out of 80 rounds...
52 KB (4,982 words) - 02:56, 20 June 2025
hash output, and with 2 l − 1 {\textstyle 2^{l-1}} being the classical preimage resistance security with the same probability. There is a general (though...
18 KB (2,307 words) - 12:57, 5 June 2025
SHA-3 (section Security against quantum attacks)
output should have d/2-bit resistance to collision attacks and d-bit resistance to preimage attacks, the maximum achievable for d bits of output. Keccak's...
52 KB (5,726 words) - 19:03, 2 June 2025
MD4 (section Collision attacks)
generate collisions in less than two MD4 hash operations. A theoretical preimage attack also exists. A variant of MD4 is used in the ed2k URI scheme to provide...
9 KB (879 words) - 05:02, 20 June 2025
collision, preventing an attacker from surreptitiously overwriting files. The known attacks (as of 2020) also do not break second preimage resistance. For a...
50 KB (5,744 words) - 14:18, 17 March 2025
In cryptography, a brute-force attack or exhaustive key search is a cryptanalytic attack that consists of an attacker submitting many possible keys or...
21 KB (2,168 words) - 17:09, 27 May 2025
Rainbow table (redirect from Rainbow attack)
the hands of attackers, they can use a precomputed rainbow table to recover the plaintext passwords. A common defense against this attack is to compute...
24 KB (3,485 words) - 14:46, 6 June 2025
In computer security, a side-channel attack is a type of security exploit that leverages information inadvertently leaked by a system—such as timing, power...
31 KB (3,588 words) - 14:14, 13 June 2025
the hash function being exposed to attacks including collision attacks, length extension attacks, and preimage attacks. Constructing a cipher or hash to...
5 KB (568 words) - 14:12, 24 May 2025
Ma, et al, describe a preimage attack that takes 2496 time and 264 memory or 2504 time and 211 memory to find a single preimage of GOST-512 reduced to...
8 KB (854 words) - 13:12, 25 May 2025
a proper compression function. A second preimage attack (given a message m 1 {\displaystyle m_{1}} an attacker finds another message m 2 {\displaystyle...
24 KB (3,977 words) - 11:37, 24 March 2025
allow an attacker to devise a forgery attack on HMAC. Furthermore, differential and rectangle distinguishers can lead to second-preimage attacks. HMAC with...
18 KB (2,316 words) - 18:51, 16 April 2025
defend against attacks that use precomputed tables (e.g. rainbow tables), by vastly growing the size of table needed for a successful attack. It also helps...
13 KB (1,527 words) - 22:35, 14 June 2025
{\displaystyle 2^{n}} (a practical example can be found in § Attacks on hashed passwords); a second preimage resistance strength, with the same expectations, refers...
49 KB (6,299 words) - 15:10, 30 May 2025
bench.cr.yp.to. Tao, Xie; Liu, Fanbao; Feng, Dengguo (2013). Fast Collision Attack on MD5 (PDF). Cryptology ePrint Archive (Technical report). IACR. Stevens...
3 KB (464 words) - 07:05, 4 October 2024
attack is a type of attack where an attacker can use Hash(message1) and the length of message1 to calculate Hash(message1 ‖ message2) for an attacker-controlled...
8 KB (1,082 words) - 12:51, 23 April 2025
(45-bit) pseudo-collision attack on the Shabal compression function with time complexity 284 was presented. A preimage attack with 2497 time and 2400 memory...
9 KB (1,139 words) - 09:04, 25 April 2024
MAC key, stronger guarantees are needed, akin to collision resistance or preimage security in hash functions. For MACs, these concepts are known as commitment...
16 KB (1,918 words) - 17:55, 22 January 2025
cracking attacks. It accesses the memory array in a password dependent order, which reduces the possibility of time–memory trade-off (TMTO) attacks, but introduces...
14 KB (1,491 words) - 04:51, 31 March 2025
this construction also has several undesirable properties: Second preimage attacks against long messages are always much more efficient than brute force...
15 KB (1,904 words) - 15:25, 10 January 2025
sliding computational cost, used to reduce vulnerability to brute-force attacks. PBKDF2 is part of RSA Laboratories' Public-Key Cryptography Standards...
13 KB (1,337 words) - 12:18, 2 June 2025
in 1999. Besides incorporating a salt to protect against rainbow table attacks, bcrypt is an adaptive function: over time, the iteration count can be...
27 KB (2,850 words) - 05:50, 21 June 2025
confusion. To prevent preimage attacks, the cryptographic hash function used for a fingerprint should possess the property of second preimage resistance. If...
9 KB (1,286 words) - 03:43, 19 January 2025
to timing attacks. To be noted, when the SSH protocol uses ChaCha20-Poly1305 as underlying primitive, it is vulnerable to the Terrapin attack. Authenticated...
13 KB (1,509 words) - 15:01, 13 June 2025