Security level management (SLM) comprises a quality assurance system for information system security. The aim of SLM is to display the information technology...
7 KB (860 words) - 07:53, 21 July 2024
cryptography, security level is a measure of the strength that a cryptographic primitive — such as a cipher or hash function — achieves. Security level is usually...
13 KB (1,332 words) - 16:46, 24 June 2025
ITIL security management describes the structured fitting of security into an organization. ITIL security management is based on the ISO 27001 standard...
23 KB (2,121 words) - 14:10, 21 November 2024
Information security management (ISM) defines and manages controls that an organization needs to implement to ensure that it is sensibly protecting the...
13 KB (1,356 words) - 17:57, 14 June 2024
Information security (infosec) is the practice of protecting information by mitigating information risks. It is part of information risk management. It typically...
161 KB (18,150 words) - 05:01, 12 July 2025
Protection ring (redirect from Privilege level)
computer security). Computer operating systems provide different levels of access to resources. A protection ring is one of two or more hierarchical levels or...
31 KB (3,861 words) - 01:34, 14 April 2025
Security management is the identification of an organization's assets i.e. including people, buildings, machines, systems and information assets, followed...
8 KB (955 words) - 22:09, 10 December 2024
1988, the Special Interest Group for Computer Security (SIG-CS), a member of the Data Processing Management Association (DPMA), brought together several...
21 KB (1,958 words) - 21:27, 26 June 2025
Security (DHS) is the U.S. federal executive department responsible for public security, roughly comparable to the interior, home, or public security...
94 KB (8,885 words) - 17:55, 21 July 2025
risk management program is to reduce risk and obtain and maintain DAA approval. The process facilitates the management of security risks by each level of...
19 KB (1,844 words) - 14:33, 26 December 2024
The security features governing the security of an identity can be divided into three levels of security: Level 1 Security (L1S) (Overt), Level 2 Security...
9 KB (1,070 words) - 10:25, 16 March 2025
clearances is carried out by the US Office of Personnel Management. Security clearance levels often appear in employment postings for Defense related...
15 KB (1,681 words) - 08:19, 2 July 2025
A chief information security officer (CISO) is a senior-level executive within an organization responsible for establishing and maintaining the enterprise...
10 KB (1,150 words) - 20:53, 17 October 2024
unofficial security guides are available. Considering the Case for Security Content in CMMI for Services has one process area, Security Management. Security by...
22 KB (2,519 words) - 04:11, 19 October 2024
National Security Council (NSC) is the national security council used by the president of the United States for consideration of national security, military...
39 KB (3,465 words) - 21:42, 5 July 2025
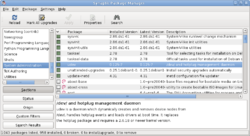
Package manager (redirect from Application-level package managers)
A package manager or package management system is a collection of software tools that automates the process of installing, upgrading, configuring, and...
35 KB (2,920 words) - 06:41, 14 July 2025
The Federal Emergency Management Agency (FEMA) is an agency of the United States Department of Homeland Security (DHS), initially created under President...
112 KB (11,280 words) - 03:17, 20 July 2025
Physical security information management (PSIM) is a category of software that provides a platform and applications created by middleware developers,...
11 KB (1,112 words) - 13:29, 23 June 2025
The Federal Information Security Management Act of 2002 (FISMA, 44 U.S.C. § 3541, et seq.) is a United States federal law enacted in 2002 as Title III...
22 KB (2,196 words) - 08:20, 21 June 2025
are generally executive-level professionals who provide direction to middle management. Compare governance. Middle management roles include branch managers...
63 KB (7,413 words) - 03:42, 22 July 2025
Information Security Management Handbook, Sixth Edition. CRC Press. ISBN 9780849374951. Douglas Mauro; Kevin Schmidt (2005). Information Security Management Handbook...
40 KB (5,090 words) - 16:30, 12 June 2025
140-3). Although the highest level of FIPS 140 security certification attainable is Security Level 4, most of the HSMs have Level 3 certification. In the Common...
14 KB (1,557 words) - 08:50, 19 May 2025
Multilevel security or multiple levels of security (MLS) is the application of a computer system to process information with incompatible classifications...
31 KB (4,178 words) - 04:23, 8 March 2025
of computer security and information technology, computer security incident management involves the monitoring and detection of security events on a computer...
13 KB (1,551 words) - 11:53, 17 July 2025
Homeland Security Investigations), the United States Secret Service, the Transportation Security Administration and the Federal Emergency Management Agency...
41 KB (1,796 words) - 03:51, 13 July 2025
IEC 62443 (category Computer security standards)
so-called Security Levels (SL). The different levels indicate the resistance against different classes of attackers. The standard emphasizes that the levels should...
20 KB (2,121 words) - 07:11, 16 July 2025
Data control language (redirect from Row level security)
permission management for users in the database. With them we can easily allow or deny some actions for users on the tables or records (row level security). DCL...
8 KB (1,011 words) - 16:25, 27 January 2025
FCAPS (redirect from Fault, Configuration, Accounting, Performance and Security)
Telecommunications Management Network model and framework for network management. FCAPS is an acronym for fault, configuration, accounting, performance, security, the...
16 KB (1,863 words) - 11:37, 10 October 2024
than the level at which the data is classified. For this reason, security clearances are required for a wide range of jobs, from senior management to janitorial...
34 KB (3,659 words) - 03:24, 4 June 2025