In computing, a denial-of-service attack (DoS attack) is a cyberattack in which the perpetrator seeks to make a machine or network resource unavailable...
99 KB (11,454 words) - 14:51, 22 May 2025
The Bluetooth Low Energy denial of service attacks are a series of denial-of-service attacks against mobile phones and iPads via Bluetooth Low Energy...
4 KB (413 words) - 13:04, 23 May 2024
Distributed denial-of-service attacks on root nameservers are Internet events in which distributed denial-of-service attacks target one or more of the thirteen...
8 KB (911 words) - 11:37, 1 July 2024
ReDoS (redirect from Regular expression Denial of Service - ReDoS)
A regular expression denial of service (ReDoS) is an algorithmic complexity attack that produces a denial-of-service by providing a regular expression...
16 KB (1,749 words) - 14:26, 22 February 2025
A Smurf attack is a distributed denial-of-service attack in which large numbers of Internet Control Message Protocol (ICMP) packets with the intended victim's...
9 KB (1,273 words) - 17:18, 24 May 2025
computer security, a billion laughs attack is a type of denial-of-service (DoS) attack which is aimed at parsers of XML documents. It is also referred...
7 KB (865 words) - 15:21, 26 May 2025
Spybot worm (section Denial of service attack)
antispyware software. Early detection of the Spybot worm usually comes from network engineers detecting the Denial of Service attack generated when the worm tried...
2 KB (313 words) - 22:22, 22 January 2024
Cyberwarfare (redirect from Cyber security attack)
consequences. In computing, a denial-of-service attack (DoS attack) or distributed denial-of-service attack (DDoS attack) is an attempt to make a machine...
151 KB (16,064 words) - 21:10, 25 May 2025
Forensic Research Lab at the Atlantic Council compared denial of the 7 October attacks to Holocaust denial. Brooking also stated that extremists will work to...
21 KB (2,003 words) - 21:48, 28 May 2025
(CVE-2002-20001) disclosed a denial-of-service attack (DoS) against the protocol variants use ephemeral keys, called D(HE)at attack. The attack exploits that the...
48 KB (5,437 words) - 22:41, 31 May 2025
held that the sole purpose of the worm was to perpetrate a distributed denial-of-service attack against SCO Group. 25 percent of Mydoom.A-infected hosts...
15 KB (1,627 words) - 14:58, 16 April 2025
A Wi-Fi deauthentication attack is a type of denial-of-service attack that targets communication between a user and a Wi-Fi wireless access point. Unlike...
8 KB (781 words) - 16:08, 1 June 2025
system. They are a form of denial-of-service attack but are different from distributed denial-of-service attacks, which involve overwhelming a network...
2 KB (231 words) - 15:18, 7 January 2024
unintentional distributed denial-of-service (DDOS) attacks on other websites and servers, due to the decentralized nature of the network.[citation needed]...
38 KB (2,574 words) - 17:17, 30 May 2025
Slowloris is a type of denial of service attack tool which allows a single machine to take down another machine's web server with minimal bandwidth and...
18 KB (1,521 words) - 06:29, 26 April 2025
Computer security (redirect from Car cyber attack)
firewall rule, many forms of distributed denial-of-service (DDoS) attacks are possible, where the attack comes from a large number of points. In this case...
220 KB (22,314 words) - 07:16, 2 June 2025
LAND (redirect from Local Area Network Denial)
A LAND (local area network denial) is a denial-of-service attack that consists of sending a special poison spoofed packet to a computer, causing it to...
3 KB (350 words) - 18:40, 2 November 2024
Zombie (computing) (category Denial-of-service attacks)
such as spreading e-mail spam and launching distributed denial-of-service attacks (DDoS attacks) against web servers. Most victims are unaware that their...
8 KB (922 words) - 17:17, 21 May 2025
Gen Digital (category Software companies of the United States)
vulnerabilities in Symantec products that could be exploited by a denial-of-service attack, and thereby compromise a system, were reported. The products involved...
86 KB (8,471 words) - 12:16, 18 May 2025
United States diplomatic cables leak (category Foreign relations of the United States)
denial-of-service attacks launched by Anonymous. Anonymous's role in the DDoS attacks on the Tunisian government's websites has led to an upsurge of internet...
123 KB (11,037 words) - 06:34, 2 June 2025
Evernote (section Denial-of-service attacks)
The service has experienced several cases of losing customer data. On June 11, 2014, Evernote suffered a distributed denial-of-service attack that prevented...
35 KB (2,783 words) - 12:37, 1 March 2025
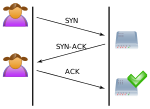
SYN flood (redirect from SYN attack)
A SYN flood is a form of denial-of-service attack on data communications in which an attacker rapidly initiates a connection to a server without finalizing...
4 KB (430 words) - 16:43, 9 February 2025
Freedom Hosting (category Defunct Tor hidden services)
activities on the dark web. One of the largest sites, Lolita City, hosted by Freedom Hosting, was subject to a denial-of-service attack (DDoS), and later had its...
15 KB (1,295 words) - 12:06, 14 May 2025
distributed denial-of-service attacks were launched against the Domain Name System (DNS) provider Dyn. The attack caused major Internet platforms and services to...
23 KB (1,617 words) - 16:28, 10 May 2025
FIB of the source address of the packet. If the interface has no route to the source address, the packet is assumed to be part of a denial of service attack...
9 KB (1,287 words) - 19:41, 3 April 2025
of messages. In the extreme, this could become a Denial of service attack against all messages on a particular channel using that cipher. The attack is...
3 KB (325 words) - 21:43, 21 June 2024
A UDP flood attack is a volumetric denial-of-service (DoS) attack using the User Datagram Protocol (UDP), a sessionless/connectionless computer networking...
3 KB (383 words) - 17:19, 3 May 2025
Web traffic (section Denial of service attacks)
also been used to coordinate large-scale distributed denial-of-service attacks. A sudden burst of publicity may accidentally cause a web traffic overload...
10 KB (1,165 words) - 09:59, 25 March 2025
High Orbit Ion Cannon (category Denial-of-service attacks)
(HOIC) is an open-source network stress testing and denial-of-service attack application designed to attack as many as 256 URLs at the same time. It was designed...
17 KB (1,755 words) - 17:57, 12 November 2024
Feedly (section Denial-of-service attacks)
11–13, 2014, Feedly suffered denial-of-service attacks that prevented users from accessing their information. The attackers demanded ransom from Feedly...
9 KB (510 words) - 10:21, 26 May 2025