A software-defined perimeter (SDP), sometimes referred to as a black cloud, is a method of enhancing computer security. The SDP framework was developed...
4 KB (518 words) - 22:20, 18 January 2025
network Software-defined networking Software-defined perimeter Software-defined protection Software-defined radio List of software-defined radios Software-defined...
405 bytes (72 words) - 13:30, 23 June 2024
added in 2019. In July, 2020, a new release of the software added the term software-defined perimeter (SDP). In late 2020, NetMotion’s products were marketed...
8 KB (585 words) - 06:06, 15 August 2024
Computer security (redirect from Software security)
obscurity – Reliance on design or implementation secrecy for security Software-defined perimeter – Method of enhancing computer security Schatz, Daniel; Bashroush...
220 KB (22,314 words) - 10:38, 16 June 2025
Zero trust architecture (redirect from Perimeter-less security)
controls. Using micro-segmentation Using overlay networks or software-defined perimeters In 2019 the United Kingdom National Cyber Security Centre (NCSC)...
11 KB (1,171 words) - 15:09, 9 June 2025
item". Tech Radar. Lewis, Achi (October 27, 2020). "Why Does the Software Defined Perimeter (SDP) Matter?". Info Security Magazine. Lemos, Robert (July 13...
20 KB (1,653 words) - 18:21, 13 February 2025
manager software". "Home Page". Advanced Clustering Technologies. "DxEnterprise". DH2I. "SQL Server HA Clustering & Software-Defined Perimeter". DH2I....
3 KB (210 words) - 07:18, 9 March 2025
Single-dealer platform, software used in financial trading Sockets Direct Protocol, a low-level remote-computing protocol Software Defined Perimeter, also called...
4 KB (461 words) - 14:21, 2 April 2025
processes to perform consistent measurements of cloud providers. Software Defined Perimeter. A proposed security framework that can be deployed to protect...
15 KB (1,381 words) - 02:32, 8 June 2025
exception to this rule and is not authorized for temporary wear. Software Defined Perimeter Joint Directorate of Infrastructure Networks and Information Systems...
45 KB (3,924 words) - 11:10, 12 May 2025
Assurance Vulnerability Alert Joint Battlespace Infosphere JTF-GNO Software Defined Perimeter Skynet (Terminator) "Global Information Grid - Glossary | CSRC"...
9 KB (1,004 words) - 07:17, 1 December 2024
Archived from the original on November 6, 2018. "Symantec Acquires Software Defined Perimeter and Zero Trust Innovator Luminate Security to Extend the Power...
83 KB (3,699 words) - 15:41, 21 August 2024
Juniper Networks (category Software companies established in 1996)
including routers, switches, network management software, network security products, and software-defined networking technology. The company was founded...
77 KB (7,048 words) - 04:07, 23 March 2025
organization in the animated television series MetaJets Black Cloud, or Software Defined Perimeter (SDP), an approach to computer security Karabulut, Turkish proper...
4 KB (584 words) - 13:25, 13 December 2023
Unit testing (redirect from Software test engineering)
of the software being tested. Formally defined test cases allow the same tests to be run repeatedly against successive versions of the software, allowing...
35 KB (4,272 words) - 23:09, 1 June 2025
nccoe.nist.gov. Huang, Dijiang; Chowdhary, Ankur; Pisharody, Sandeep. Software-Defined Networking and Security. doi:10.1201/9781351210768-8. Edwards, John...
6 KB (589 words) - 07:53, 9 October 2024
Physical security (category Perimeter security)
topped with razor wire); in this case, the outer security perimeter will be generally defined as the walls, windows and doors of the structure itself....
24 KB (2,265 words) - 11:30, 17 June 2025
Log management (redirect from Log management software)
the logs in the devices on the security perimeter. They aim to identify the patterns of attack on the perimeter infrastructure of the organization. with...
7 KB (808 words) - 21:05, 12 February 2025
Bastion host (category Internet Protocol based network software)
firewall or filtering router. Firewalls and routers, anything that provides perimeter access control security can be considered bastion hosts. Other types of...
4 KB (511 words) - 11:59, 24 November 2024
network perimeter. and a developer of software-defined network controllers, Contrail Systems. In 2014 Juniper acquired the software-defined networking...
23 KB (1,275 words) - 21:03, 20 November 2024
Personal firewall (category Firewall software)
with was the installation of special software (firewall software) on every BudNET server, workstation, and perimeter security device. Indeed, every single...
7 KB (998 words) - 08:14, 15 June 2025
or brand names such as the Humphrey Field Analyzer, Octopus Perimeter, Optopol perimeter, Olleyes VisuALL, etc.[citation needed] Techniques used to perform...
13 KB (1,472 words) - 08:40, 9 June 2025
SARL (programming language) (category Agent-based software)
architecture according to their current needs and goals. A Context defines the perimeter/boundary of a sub-system, and gathers a collection of Spaces. In...
12 KB (1,565 words) - 22:28, 24 August 2024
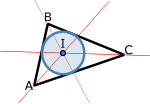
Incenter (section Area and perimeter splitters)
a point defined for any triangle in a way that is independent of the triangle's placement or scale. The incenter may be equivalently defined as the point...
15 KB (2,225 words) - 00:59, 18 February 2025
Web application firewall (category Firewall software)
solution, rather they are meant to be used in conjunction with other network perimeter security solutions such as network firewalls and intrusion prevention...
13 KB (1,327 words) - 17:10, 4 June 2025
dots with relatively small perimeter (in the shadows) exhibiting greater gain than dots with relatively larger perimeter (in the midtones). Karl Haller...
12 KB (1,674 words) - 23:59, 20 December 2024
taken into consideration when measuring, and hence no single well-defined perimeter to the landmass. Various approximations exist when specific assumptions...
25 KB (2,911 words) - 15:17, 31 May 2025
List of acquisitions by Cisco (redirect from TGV Software)
Identity as the New Perimeter: Cisco Announces Intent to Acquire Oort". Cisco. July 13, 2023. "Cisco to Acquire Isovalent to Define the Future of Multicloud...
115 KB (5,229 words) - 23:16, 24 May 2025
SSH File Transfer Protocol (section Software)
difficult to control SFTP transfers on security devices at the network perimeter. There are standard tools for logging FTP transactions, like TIS gdev...
14 KB (1,534 words) - 18:07, 11 May 2025
level inside a structure to the light level outside the structure. It is defined as: DF = (Ei / Eo) x 100% where, Ei = illuminance due to daylight at a...
5 KB (611 words) - 18:35, 27 December 2023