older tunneling protocols for point-to-point communication: Cisco's Layer 2 Forwarding Protocol (L2F) and Microsoft's Point-to-Point Tunneling Protocol (PPTP)...
15 KB (1,825 words) - 13:49, 8 September 2024
Socket Tunneling Protocol IPSec (IP protocols 50 and 51): Internet Protocol Security L2TP (UDP port 1701): Layer 2 Tunneling Protocol L2TPv3 (IP protocol 115):...
15 KB (1,956 words) - 06:58, 12 June 2025
L2F, or Layer 2 Forwarding, is a tunneling protocol developed by Cisco Systems, Inc. to establish virtual private network connections over the Internet...
2 KB (132 words) - 08:29, 31 October 2023
The Point-to-Point Tunneling Protocol (PPTP) is an obsolete method for implementing virtual private networks. PPTP has many well known security issues...
8 KB (847 words) - 10:37, 22 April 2025
L2F, Layer 2 Forwarding Protocol L2TP, Layer 2 Tunneling Protocol NetBIOS, Network Basic Input Output System PAP, Password Authentication Protocol PPTP...
7 KB (974 words) - 03:05, 9 April 2025
Protocol LattisNet LocalTalk L2F Layer 2 Forwarding Protocol L2TP Layer 2 Tunneling Protocol LLDP Link Layer Discovery Protocol LLDP-MED Link Layer Discovery...
11 KB (970 words) - 22:41, 17 February 2025
Datagram Transport Layer Security (DTLS) is a communications protocol providing security to datagram-based applications by allowing them to communicate...
16 KB (1,472 words) - 16:06, 28 January 2025
Virtual private network (section Protocols)
Socket Tunneling Protocol (SSTP) tunnels Point-to-Point Protocol (PPP) or Layer 2 Tunneling Protocol traffic through an SSL/TLS channel (SSTP was introduced...
32 KB (3,542 words) - 08:07, 13 June 2025
L2TPv3 (category Tunneling protocols)
April 24, 2021. IETF L2TPEXT working group RFC 3931 - Layer Two Tunneling Protocol - Version 3 (L2TPv3) RFC 2661 - Layer Two Tunneling Protocol "L2TP"...
2 KB (186 words) - 14:02, 15 June 2024
(Amtrak station), Amtrak station code L2TP Network Server in Layer 2 Tunneling Protocol VPNs Lancaster Airport (Pennsylvania), US, IATA code Lesch–Nyhan...
664 bytes (110 words) - 11:38, 27 December 2022
Provider-provisioned VPN (section OSI Layer 2 services)
plaintext tunneling protocols include Layer 2 Tunneling Protocol (L2TP) when it is set up without IPsec and Point-to-Point Tunneling Protocol (PPTP) or...
13 KB (1,472 words) - 19:19, 11 June 2025
Outline of the Internet (section Link layer)
Shortest Path First (OSPF) – Tunneling protocol (Tunnels) – Layer 2 Tunneling Protocol (L2TP) – Point-to-Point Protocol (PPP) – Medium access control...
14 KB (1,379 words) - 17:49, 2 June 2025
Pseudowire (category Tunneling protocols)
Multiprotocol Label Switching (MPLS), Internet Protocol (IPv4 or IPv6), or Layer 2 Tunneling Protocol Version 3 (L2TPv3). The first pseudowire specifications...
6 KB (612 words) - 22:31, 16 February 2025
The Link Layer Discovery Protocol (LLDP) is a vendor-neutral link layer protocol used by network devices for advertising their identity, capabilities...
8 KB (718 words) - 10:37, 1 June 2025
The data link layer, or layer 2, is the second layer of the seven-layer OSI model of computer networking. This layer is the protocol layer that transfers...
16 KB (2,170 words) - 17:08, 29 March 2025
In computer networking, Point-to-Point Protocol (PPP) is a data link layer (layer 2) communication protocol between two routers directly without any host...
21 KB (2,284 words) - 09:40, 21 April 2025
Method for Transmitting PPP Over Ethernet (PPPoE) RFC 3817 - Layer 2 Tunneling Protocol (L2TP) Active Discovery Relay for PPP over Ethernet (PPPoE) RFC 4638...
44 KB (5,528 words) - 16:38, 6 June 2025
Voice over IP (redirect from Voice over internet protocol)
and tunneling. The common tunneling protocol used is Layer 2 Tunneling Protocol and the common encryption mechanism used is Secure Sockets Layer (SSL)...
88 KB (10,327 words) - 17:34, 21 May 2025
networking, the link layer is the lowest layer in the Internet protocol suite, the networking architecture of the Internet. The link layer is the group of...
6 KB (1,061 words) - 20:14, 27 August 2024
List of TCP and UDP port numbers (category Transmission Control Protocol)
underlying protocol layers which meet the requirements described in the specification are possible. Comparison of file transfer protocols Internet protocol suite...
320 KB (13,096 words) - 15:43, 20 June 2025
preventing tuberculosis L2TP Access Concentrator, endpoint of a Layer 2 Tunneling Protocol tunnel Laboratoire Aimé-Cotton, French research laboratory Linear...
3 KB (419 words) - 11:09, 26 April 2025
Socket Tunneling Protocol (SSTP) is a form of virtual private network (VPN) tunnel that provides a mechanism to transport Point-to-Point Protocol (PPP)...
9 KB (773 words) - 09:48, 3 May 2025
Virtual Extensible LAN (redirect from VXLAN tunnel endpoint)
VxLAN. Overlay Transport Virtualization (OTV) Virtual LAN (VLAN) Layer 2 Tunneling Protocol (L2TP) Herrod, Steve (August 30, 2011). "Towards Virtualized Networking...
7 KB (722 words) - 09:06, 13 June 2025
transport layer is a conceptual division of methods in the layered architecture of protocols in the network stack in the Internet protocol suite and the...
17 KB (1,646 words) - 00:00, 15 June 2025
Multiprotocol Label Switching (redirect from Multi-protocol label switching)
transport medium, using any protocol. The primary benefit is to eliminate dependence on a particular OSI model data link layer (layer 2) technology, and eliminate...
33 KB (4,709 words) - 14:34, 21 May 2025
Resolution Protocol (ARP) is a communication protocol for discovering the link layer address, such as a MAC address, associated with a internet layer address...
20 KB (2,966 words) - 04:27, 29 April 2025
An application layer is an abstraction layer that specifies the shared communication protocols and interface methods used by hosts in a communications...
11 KB (1,109 words) - 09:47, 24 May 2025
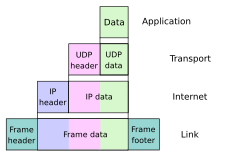
Encapsulation (networking) (redirect from Upper layer protocol)
processes can also serve as malicious features like in the tunneling protocols. The physical layer is responsible for physical transmission of the data, link...
6 KB (564 words) - 09:35, 12 April 2025
Authentication via Secure Tunneling (EAP-FAST; RFC 4851) is a protocol proposal by Cisco Systems as a replacement for LEAP. The protocol was designed to address...
34 KB (4,172 words) - 20:50, 1 May 2025