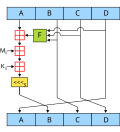
MD5 (redirect from MD5 - A Message Digest Algorithm)
Wikifunctions has a function related to this topic. The MD5 message-digest algorithm is a widely used hash function producing a 128-bit hash value. MD5...
47 KB (4,724 words) - 18:22, 28 April 2025
MD2 (hash function) (redirect from Message Digest Algorithm 2)
The MD2 Message-Digest Algorithm is a cryptographic hash function developed by Ronald Rivest in 1989. The algorithm is optimized for 8-bit computers....
9 KB (1,053 words) - 04:19, 31 December 2024
Cryptographic hash function (redirect from Message-digest algorithm)
the other Secure Hash Algorithms such as SHA-0, SHA-2, and SHA-3. RIPEMD (RACE Integrity Primitives Evaluation Message Digest) is a family of cryptographic...
49 KB (6,299 words) - 20:13, 4 May 2025
generation algorithm selects a key from the key space uniformly at random. A MAC generation algorithm efficiently returns a tag given the key and the message. A...
16 KB (1,918 words) - 17:55, 22 January 2025
"SHA-256" and "SHA-256-sess" algorithms for digest authentication. However, support for "SHA-512-256", "SHA-512-256-sess" algorithms and username hashing is...
25 KB (2,879 words) - 05:47, 26 April 2025
The MD4 Message-Digest Algorithm is a cryptographic hash function developed by Ronald Rivest in 1990. The digest length is 128 bits. The algorithm has influenced...
8 KB (871 words) - 18:48, 12 January 2025
BLAKE (hash function) (category Checksum algorithms)
BLAKE2b algorithm. The BLAKE2b algorithm uses 8-byte (UInt64) words, and 128-byte chunks. Algorithm BLAKE2b Input: M Message to be hashed cbMessageLen: Number...
30 KB (2,855 words) - 02:58, 11 January 2025
The algorithm uses a key pair consisting of a public key and a private key. The private key is used to generate a digital signature for a message, and...
16 KB (2,229 words) - 16:39, 21 April 2025
SHA-1 (category Checksum algorithms)
(Secure Hash Algorithm 1) is a hash function which takes an input and produces a 160-bit (20-byte) hash value known as a message digest – typically rendered...
50 KB (5,744 words) - 14:18, 17 March 2025
Hash function (redirect from Message digest)
returned by a hash function are called hash values, hash codes, (hash/message) digests, or simply hashes. The values are usually used to index a fixed-size...
50 KB (7,467 words) - 03:03, 8 May 2025
SHA-2 (category Checksum algorithms)
the hash algorithms and recommendations for their use to Special Publications 800-107 and 800-57. Detailed test data and example message digests were also...
51 KB (4,982 words) - 00:42, 8 May 2025
Cipher suite (section Supported algorithms)
The set of algorithms that cipher suites usually contain include: a key exchange algorithm, a bulk encryption algorithm, and a message authentication...
19 KB (2,358 words) - 16:00, 5 September 2024
"An Open Digest-based Technique for Spam Detection". The goal of Nilsimsa is to generate a hash digest of an email message such that the digests of two...
4 KB (377 words) - 18:35, 28 August 2024
Basic and Digest Access Authentication RFC 3540 – Robust Explicit Congestion Notification (ECN) Signaling with Nonces RFC 4418 – UMAC: Message Authentication...
7 KB (881 words) - 16:27, 15 April 2025
HMAC (redirect from Keyed-Hashing Message Authentication)
(March 2011). Updated Security Considerations for the MD5 Message-Digest and the HMAC-MD5 Algorithms. Internet Engineering Task Force. doi:10.17487/RFC6151...
18 KB (2,316 words) - 18:51, 16 April 2025
SHA-3 (Secure Hash Algorithm 3) is the latest member of the Secure Hash Algorithm family of standards, released by NIST on August 5, 2015. Although part...
52 KB (5,727 words) - 18:01, 16 April 2025
HTTP 404 (redirect from 404 (error message))
404 not found, 404, 404 error, page not found, or file not found error message is a hypertext transfer protocol (HTTP) standard response code, to indicate...
16 KB (1,945 words) - 08:23, 23 December 2024
Wireless Transport Layer Security (section Algorithms)
compression; removes reliance on DNS; enables a walled garden Digest truncation – HMAC message digests are truncated to reduce transmission overhead, this reduces...
5 KB (629 words) - 05:05, 16 February 2025
Whirlpool (hash function) (redirect from Whirlpool (algorithm))
Encryption Standard (AES). Whirlpool takes a message of any length less than 2256 bits and returns a 512-bit message digest. The authors have declared that "WHIRLPOOL...
11 KB (1,054 words) - 03:57, 19 March 2024
The MD6 Message-Digest Algorithm is a cryptographic hash function. It uses a Merkle tree-like structure to allow for immense parallel computation of hashes...
6 KB (493 words) - 05:35, 22 January 2025
RC4 (redirect from RC4 decryption algorithm)
key-scheduling algorithm (KSA). Once this has been completed, the stream of bits is generated using the pseudo-random generation algorithm (PRGA). The key-scheduling...
44 KB (5,081 words) - 14:07, 26 April 2025
17 input bytes. The round function of the cipher is the SHA-1 message digest algorithm keyed with a four-byte sequence. Let + denote the concatenation...
18 KB (2,284 words) - 09:18, 2 May 2025
GOST (hash function) (section Algorithm)
a 256-bit integer representing the length of the original message, in bits. The algorithm descriptions uses the following notation: f 0 g j {\displaystyle...
16 KB (2,206 words) - 02:44, 11 July 2024
Tiger (hash function) (section Algorithm)
addition/subtraction, rotates, and S-box lookups, and a fairly intricate key scheduling algorithm for deriving 24 round keys from the 8 input words. Although fast in software...
9 KB (910 words) - 14:47, 30 September 2023
Elliptic curve only hash (section The algorithm)
The elliptic curve only hash (ECOH) algorithm was submitted as a candidate for SHA-3 in the NIST hash function competition. However, it was rejected in...
11 KB (1,846 words) - 17:39, 7 January 2025
C).digest() counter += 1 # 4. Output the leading l octets of T as the octet string mask. return T[:length] Example outputs of MGF1: Python 3.10.4 (main...
7 KB (936 words) - 20:03, 8 April 2024
mainly due to security concerns. Although the security of the full hash algorithm was not compromised, the discovery of non-randomness properties with low...
9 KB (1,139 words) - 09:04, 25 April 2024
KCDSA (Korean Certificate-based Digital Signature Algorithm) is a digital signature algorithm created by a team led by the Korea Internet & Security Agency...
4 KB (753 words) - 16:13, 20 October 2023