information security, a buffer overflow or buffer overrun is an anomaly whereby a program writes data to a buffer beyond the buffer's allocated memory, overwriting...
46 KB (5,132 words) - 06:40, 27 April 2025
Buffer overflow protection is any of various techniques used during software development to enhance the security of executable programs by detecting buffer...
25 KB (2,836 words) - 13:59, 27 April 2025
In software, a stack buffer overflow or stack buffer overrun occurs when a program writes to a memory address on the program's call stack outside of the...
22 KB (2,668 words) - 05:08, 7 March 2025
represent Buffer overflow, a situation whereby the incoming data size exceeds that which can be accommodated by a buffer. Heap overflow, a type of buffer overflow...
1 KB (239 words) - 22:44, 1 April 2025
Secure coding (section Buffer-overflow prevention)
security. Buffer overflows, a common software security vulnerability, happen when a process tries to store data beyond a fixed-length buffer. For example...
8 KB (988 words) - 17:30, 1 September 2024
essentially a buffer overflow), the stack is said to overflow, typically resulting in a program crash. The most-common cause of stack overflow is excessively...
11 KB (961 words) - 00:07, 27 June 2024
Segmentation fault (section Buffer overflow)
points to memory that has been freed/deallocated/deleted) A buffer overflow A stack overflow Attempting to execute a program that does not compile correctly...
19 KB (2,431 words) - 08:02, 13 April 2025
Code sanitizer (section ASan: Heap-buffer-overflow)
directly mapped shadow memory to detect memory corruption such as buffer overflows or accesses to a dangling pointer (use-after-free). Google's ASan,...
15 KB (1,483 words) - 08:55, 19 February 2025
unexpectedly small, potentially leading to a buffer overflow which, depending on the use of the buffer, might in turn cause arbitrary code execution...
28 KB (3,206 words) - 15:35, 14 April 2025
possible buffer overflows if the bounds are not checked manually; string routines in general, for side-effects, encouraging irresponsible buffer usage,...
37 KB (3,694 words) - 11:18, 26 January 2025
Corporation, Buffer overflow in crypto.signText() Archived 2014-06-04 at the Wayback Machine Festa, Paul (19 August 1998). "Buffer-overflow bug in IE"....
84 KB (7,921 words) - 13:24, 2 May 2025
security, safety, catching all attempts at out-of-bounds access and buffer overflow. Descriptors are a form of capability system. The development of the...
22 KB (2,385 words) - 07:05, 20 April 2025
A heap overflow, heap overrun, or heap smashing is a type of buffer overflow that occurs in the heap data area. Heap overflows are exploitable in a different...
6 KB (679 words) - 21:24, 1 May 2025
computer. Buffer overflow Buffer underrun Circular buffer Disk buffer Streaming media Frame buffer for use in graphical display Double buffering and Triple...
7 KB (1,018 words) - 08:46, 13 April 2025
before the buffer overflows. A larger buffer size simply means that the decoder will tolerate high bitrates for longer periods of time, but no buffer is infinite...
2 KB (259 words) - 18:39, 7 February 2022
term as defined above is distinct from buffer overflow, a condition where a portion of memory forms a buffer of a fixed size yet is filled with more...
5 KB (767 words) - 17:49, 22 August 2024
such as the stack and heap, as non-executable, helping to prevent buffer overflow exploits. These attacks rely on some part of memory, usually the stack...
20 KB (2,759 words) - 09:06, 4 May 2025
vulnerability known as a buffer overflow. It did this by using a long string of the repeated letter 'N' to overflow a buffer, allowing the worm to execute...
7 KB (709 words) - 02:07, 15 April 2025
item) { if ((writeIndx + 1) % N == readIndx) { // buffer is full, avoid overflow return 0; } buffer[writeIndx] = item; writeIndx = (writeIndx + 1) % N;...
13 KB (1,436 words) - 06:43, 10 April 2025
via YouTube. Michal Zalewski (August 19, 1999). "[RHSA-1999:028-01] Buffer overflow in libtermcap tgetent()". Newsgroup: muc.lists.bugtraq. Retrieved December...
8 KB (810 words) - 09:20, 2 May 2025
Windows provided no buffer-overrun protections until 2004. Eventually, operating systems began to combat the exploitation of buffer overflow bugs by marking...
31 KB (3,848 words) - 04:24, 21 April 2025
New Standard". Dr. Dobb's Journal. Safe C API—Concise solution of buffer overflow, The OWASP Foundation, OWASP AppSec, Beijing 2011 C Language Working...
12 KB (1,049 words) - 03:56, 16 February 2025
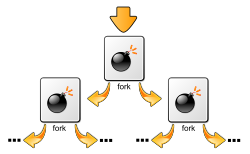
allowed for execution of the attack. The worm spreads by exploiting a buffer overflow discovered by the Polish security research group Last Stage of Delirium...
18 KB (1,744 words) - 16:18, 29 December 2024
stack overflow is a programming error when too much memory is used on the call stack. Stack overflow may also refer to: Stack buffer overflow, when a...
417 bytes (95 words) - 17:16, 25 March 2025
access to a machine but can exploit a vulnerability, for example a buffer overflow, in a higher-privileged process on that machine. If successfully executed...
25 KB (2,909 words) - 23:12, 13 February 2025
"return-to-libc" attack is a computer security attack usually starting with a buffer overflow in which a subroutine return address on a call stack is replaced by...
5 KB (587 words) - 01:42, 8 November 2024
memory addresses, incorrect address values in the program counter, buffer overflow, overwriting a portion of the affected program code due to an earlier...
13 KB (1,424 words) - 06:49, 10 April 2025
US-CERT Alerts. Archived from the original on 2006-04-08. "CA-2003-25 Buffer Overflow in Sendmail". CERT Advisories. 31 December 2003. Archived from the...
11 KB (974 words) - 14:47, 11 August 2024
feature for VMware CVE-2008-1943 Xen Para Virtualized Frame Buffer backend buffer overflow. CVE-2009-1244 Cloudburst: VM display function in VMware CVE-2011-1751...
11 KB (1,141 words) - 19:43, 5 March 2025
into another program’s data storage area and execute it, such as in a buffer overflow attack. The term "NX bit" was introduced by Advanced Micro Devices...
10 KB (1,167 words) - 12:37, 3 May 2025