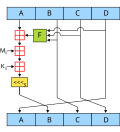
MD5 (redirect from Message Digest Algorithm 5)
Wikifunctions has a function related to this topic. The MD5 message-digest algorithm is a widely used hash function producing a 128-bit hash value. MD5...
47 KB (4,724 words) - 18:22, 28 April 2025
MD2 (hash function) (redirect from Message Digest Algorithm 2)
The MD2 Message-Digest Algorithm is a cryptographic hash function developed by Ronald Rivest in 1989. The algorithm is optimized for 8-bit computers....
9 KB (1,053 words) - 04:19, 31 December 2024
Cryptographic hash function (redirect from Message-digest algorithm)
the other Secure Hash Algorithms such as SHA-0, SHA-2, and SHA-3. RIPEMD (RACE Integrity Primitives Evaluation Message Digest) is a family of cryptographic...
49 KB (6,299 words) - 20:13, 4 May 2025
generation algorithm selects a key from the key space uniformly at random. A MAC generation algorithm efficiently returns a tag given the key and the message. A...
16 KB (1,918 words) - 17:55, 22 January 2025
The MD4 Message-Digest Algorithm is a cryptographic hash function developed by Ronald Rivest in 1990. The digest length is 128 bits. The algorithm has influenced...
8 KB (871 words) - 18:48, 12 January 2025
"SHA-256" and "SHA-256-sess" algorithms for digest authentication. However, support for "SHA-512-256", "SHA-512-256-sess" algorithms and username hashing is...
25 KB (2,879 words) - 05:47, 26 April 2025
SHA-1 (category Checksum algorithms)
(Secure Hash Algorithm 1) is a hash function which takes an input and produces a 160-bit (20-byte) hash value known as a message digest – typically rendered...
50 KB (5,744 words) - 14:18, 17 March 2025
Hash function (redirect from Message digest)
returned by a hash function are called hash values, hash codes, (hash/message) digests, or simply hashes. The values are usually used to index a fixed-size...
50 KB (7,467 words) - 03:03, 8 May 2025
BLAKE (hash function) (category Checksum algorithms)
with 16 message words, truncating the ChaCha result to obtain the next hash value. BLAKE-256 and BLAKE-224 use 32-bit words and produce digest sizes of...
30 KB (2,855 words) - 02:58, 11 January 2025
SHA-2 (category Checksum algorithms)
the hash algorithms and recommendations for their use to Special Publications 800-107 and 800-57. Detailed test data and example message digests were also...
51 KB (4,982 words) - 00:42, 8 May 2025
The algorithm uses a key pair consisting of a public key and a private key. The private key is used to generate a digital signature for a message, and...
16 KB (2,229 words) - 16:39, 21 April 2025
Cipher suite (section Supported algorithms)
The set of algorithms that cipher suites usually contain include: a key exchange algorithm, a bulk encryption algorithm, and a message authentication...
19 KB (2,358 words) - 16:00, 5 September 2024
Digital signature (redirect from Adaptive chosen-message attack)
A signing algorithm that, given a message and a private key, produces a signature. A signature verifying algorithm that, given the message, public key...
45 KB (5,315 words) - 16:52, 11 April 2025
SHA-3 (Secure Hash Algorithm 3) is the latest member of the Secure Hash Algorithm family of standards, released by NIST on August 5, 2015. Although part...
52 KB (5,727 words) - 18:01, 16 April 2025
Wireless Transport Layer Security (section Algorithms)
compression; removes reliance on DNS; enables a walled garden Digest truncation – HMAC message digests are truncated to reduce transmission overhead, this reduces...
5 KB (629 words) - 05:05, 16 February 2025
HTTP 404 (redirect from 404 (error message))
404 not found, 404, 404 error, page not found, or file not found error message is a hypertext transfer protocol (HTTP) standard response code, to indicate...
16 KB (1,945 words) - 08:23, 23 December 2024
Whirlpool (hash function) (redirect from Whirlpool (algorithm))
Encryption Standard (AES). Whirlpool takes a message of any length less than 2256 bits and returns a 512-bit message digest. The authors have declared that "WHIRLPOOL...
11 KB (1,054 words) - 03:57, 19 March 2024
17 input bytes. The round function of the cipher is the SHA-1 message digest algorithm keyed with a four-byte sequence. Let + denote the concatenation...
18 KB (2,284 words) - 09:18, 2 May 2025
and SHA-512) digests, SHA-3 (a subset of the Keccak digest family), the TWOFISH block cipher, RSA, DSA and ECDSA public-key algorithms, the Yarrow pRNG...
6 KB (517 words) - 07:13, 8 January 2025
Tiger (hash function) (section Algorithm)
addition/subtraction, rotates, and S-box lookups, and a fairly intricate key scheduling algorithm for deriving 24 round keys from the 8 input words. Although fast in software...
9 KB (910 words) - 14:47, 30 September 2023
(see , Section 7.5). Key Identifier: 32 bits Unsigned integer designating an MD5 key shared by the client and server. Message Digest (MD5): 128 bits MD5...
62 KB (6,428 words) - 17:05, 7 April 2025
authentication (ESMTPA) is CRAM-MD5, and uses of the MD5 algorithm in HMACs (hash-based message authentication codes) are still considered sound. The Internet...
10 KB (1,229 words) - 16:16, 6 December 2024
RC4 (redirect from RC4 decryption algorithm)
S[j] := S[i]; S[i] := b;) c := S[i<<5 ⊕ j>>3] + S[j<<5 ⊕ i>>3] output (S[a+b] + S[c⊕0xAA]) ⊕ S[j+b] endwhile This algorithm has not been analyzed significantly...
44 KB (5,081 words) - 14:07, 26 April 2025
Elliptic curve only hash (section The algorithm)
The elliptic curve only hash (ECOH) algorithm was submitted as a candidate for SHA-3 in the NIST hash function competition. However, it was rejected in...
11 KB (1,846 words) - 17:39, 7 January 2025
operations and lookup tables only, the endianness is irrelevant. The size of message digest equals to the size of chaining values usually. In truncated versions...
16 KB (806 words) - 20:08, 6 August 2024
GOST (hash function) (section Algorithm)
a 256-bit integer representing the length of the original message, in bits. The algorithm descriptions uses the following notation: f 0 g j {\displaystyle...
16 KB (2,206 words) - 02:44, 11 July 2024
against bare digest algorithms, and so has been thought worth the effort. Cryptographic hash functions are a third type of cryptographic algorithm. They take...
99 KB (10,975 words) - 20:28, 3 April 2025