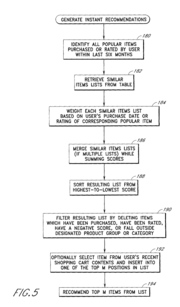
Algorithm characterizations are attempts to formalize the word algorithm. Algorithm does not have a generally accepted formal definition. Researchers... 72 KB (8,851 words) - 10:09, 9 January 2024 |
single loop, thereby reducing the time complexity. Algorithm engineering Algorithm characterizations Theory of computation "technique | Definition of technique... 8 KB (835 words) - 17:13, 23 August 2023 |
In mathematical logic, a Lindström quantifier is a generalized polyadic quantifier. Lindström quantifiers generalize first-order quantifiers, such as the... 7 KB (1,189 words) - 09:35, 8 February 2022 |
Visibility graph (section Characterization) visibility graphs induce a simple polygon. However, an efficient algorithmic characterization of the visibility graphs of simple polygons remains unknown.... 7 KB (883 words) - 06:48, 11 March 2024 |
Selection is the stage of a genetic algorithm or more general evolutionary algorithm in which individual genomes are chosen from a population for later... 10 KB (1,334 words) - 06:17, 8 May 2024 |
system that uses paging for virtual memory management, page replacement algorithms decide which memory pages to page out, sometimes called swap out, or write... 47 KB (6,235 words) - 16:15, 7 January 2024 |
computer science and operations research, approximation algorithms are efficient algorithms that find approximate solutions to optimization problems... 21 KB (2,775 words) - 11:07, 13 August 2023 |
Greedoid (category Greedy algorithms) by greedy algorithms. Around 1980, Korte and Lovász introduced the greedoid to further generalize this characterization of greedy algorithms; hence the... 12 KB (1,721 words) - 04:37, 24 February 2024 |
Newell's Algorithm is a 3D computer graphics procedure for elimination of polygon cycles in the depth sorting required in hidden surface removal. It was... 3 KB (364 words) - 01:20, 8 May 2023 |
science, an enumeration algorithm is an algorithm that enumerates the answers to a computational problem. Formally, such an algorithm applies to problems... 9 KB (1,186 words) - 21:28, 3 January 2023 |
B-machine Post–Turing machine - description plus examples Algorithm Algorithm characterizations Halting problem Busy beaver Stack machine WDR paper computer... 53 KB (5,162 words) - 21:40, 7 May 2024 |
 | Linear programming (redirect from Algorithms for linear programming) affine (linear) function defined on this polytope. A linear programming algorithm finds a point in the polytope where this function has the largest (or... 60 KB (6,567 words) - 00:45, 20 April 2024 |
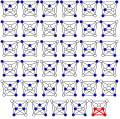 | Clique problem (redirect from Approximation algorithms for the clique problem) time algorithm is known for this problem, more efficient algorithms than the brute-force search are known. For instance, the Bron–Kerbosch algorithm can... 84 KB (9,876 words) - 12:20, 12 February 2024 |
Outline of computer programming (section Algorithms) concerns Threaded coding List of algorithms List of algorithm general topics Algorithm characterizations Introduction to Algorithms Theory of computation Computational... 15 KB (991 words) - 19:23, 4 March 2024 |
Matching (graph theory) (section Characterizations) Hopcroft-Karp algorithm in time O(√VE) time, and there are more efficient randomized algorithms, approximation algorithms, and algorithms for special classes... 23 KB (2,934 words) - 00:14, 30 April 2024 |
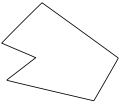 | Point in polygon (redirect from Ray casting algorithm) ray intersection algorithm. This algorithm is sometimes also known as the crossing number algorithm or the even–odd rule algorithm, and was known as... 12 KB (1,518 words) - 17:00, 10 December 2023 |
P versus NP problem (section Logical characterizations) size of the input to the algorithm (as opposed to, say, exponential time). The general class of questions that some algorithm can answer in polynomial... 62 KB (7,720 words) - 03:54, 29 April 2024 |
PCP theorem (redirect from PCP characterization theorem) probabilistically checkable proofs (proofs that can be checked by a randomized algorithm) of constant query complexity and logarithmic randomness complexity (uses... 15 KB (1,751 words) - 05:59, 21 March 2024 |
an obstruction set for that family. Forbidden graph characterizations may be used in algorithms for testing whether a graph belongs to a given family... 17 KB (1,207 words) - 01:23, 14 March 2024 |
Intuitively, an algorithmically random sequence (or random sequence) is a sequence of binary digits that appears random to any algorithm running on a (prefix-free... 33 KB (4,875 words) - 20:29, 20 March 2024 |
Gröbner basis (redirect from Multivariate division algorithm) word" for having two different characterizations of Gröbner bases. All the following assertions are characterizations of Gröbner bases: a polynomial f... 62 KB (9,909 words) - 01:29, 9 May 2024 |
In numerical linear algebra, the tridiagonal matrix algorithm, also known as the Thomas algorithm (named after Llewellyn Thomas), is a simplified form... 20 KB (4,095 words) - 21:00, 8 April 2024 |
The Remez algorithm or Remez exchange algorithm, published by Evgeny Yakovlevich Remez in 1934, is an iterative algorithm used to find simple approximations... 14 KB (2,584 words) - 17:42, 15 January 2024 |
Pi (section Role and characterizations in mathematics) computations. Around 250 BC, the Greek mathematician Archimedes created an algorithm to approximate π with arbitrary accuracy. In the 5th century AD, Chinese... 145 KB (17,361 words) - 13:47, 6 May 2024 |
have a minor in the set {K5, K3,3}. The existence of forbidden minor characterizations for all minor-closed graph families is an equivalent way of stating... 19 KB (2,515 words) - 12:19, 11 September 2023 |
performed using maximum likelihood. For linear chain HMMs, the Baum–Welch algorithm can be used to estimate the parameters. Hidden Markov models are known... 51 KB (6,740 words) - 07:49, 7 April 2024 |
RC4 (redirect from RC4 decryption algorithm) Subhamoy; Paul, Goutam (2008). "A Complete Characterization of the Evolution of RC4 Pseudo Random Generation Algorithm". Journal of Mathematical Cryptology... 44 KB (5,058 words) - 05:30, 15 April 2024 |