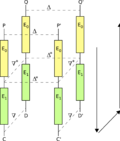
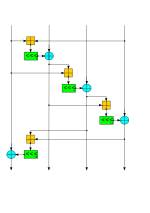
Differential cryptanalysis is a general form of cryptanalysis applicable primarily to block ciphers, but also to stream ciphers and cryptographic hash...
13 KB (1,688 words) - 22:44, 29 October 2023
impossible differential cryptanalysis is a form of differential cryptanalysis for block ciphers. While ordinary differential cryptanalysis tracks differences...
10 KB (850 words) - 11:20, 13 February 2024
higher-order differential cryptanalysis is a generalization of differential cryptanalysis, an attack used against block ciphers. While in standard differential cryptanalysis...
5 KB (783 words) - 05:19, 26 August 2023
In cryptography, truncated differential cryptanalysis is a generalization of differential cryptanalysis, an attack against block ciphers. Lars Knudsen...
4 KB (318 words) - 04:35, 17 October 2023
In cryptography, linear cryptanalysis is a general form of cryptanalysis based on finding affine approximations to the action of a cipher. Attacks have...
6 KB (812 words) - 13:20, 1 November 2023
with less complexity than a brute-force search: differential cryptanalysis (DC), linear cryptanalysis (LC), and Davies' attack. However, the attacks are...
59 KB (6,541 words) - 19:15, 14 April 2024
1994, the differential-linear attack is a mix of both linear cryptanalysis and differential cryptanalysis. The attack utilises a differential characteristic...
4 KB (385 words) - 03:30, 1 February 2024
differential cryptanalysis Integral cryptanalysis Linear cryptanalysis Meet-in-the-middle attack Mod-n cryptanalysis Related-key attack Sandwich attack...
44 KB (5,176 words) - 14:55, 27 April 2024
Block cipher (section Differential cryptanalysis)
growing catalog of attacks: truncated differential cryptanalysis, partial differential cryptanalysis, integral cryptanalysis, which encompasses square and integral...
50 KB (6,475 words) - 22:23, 3 May 2024
Boomerang attack (redirect from Amplified boomerang cryptanalysis)
the boomerang attack is a method for the cryptanalysis of block ciphers based on differential cryptanalysis. The attack was published in 1999 by David...
9 KB (864 words) - 04:16, 17 October 2023
DES-X also increases the strength of DES against differential cryptanalysis and linear cryptanalysis, although the improvement is much smaller than in...
4 KB (532 words) - 15:06, 26 January 2024
Eli Biham (section Contributions to cryptanalysis)
years as chief of CS graduate school. Biham invented (publicly) differential cryptanalysis, for which he received his Ph.D., while working under Adi Shamir...
4 KB (348 words) - 05:39, 14 May 2024
2013-02-19. Eli Biham, Adi Shamir: Differential Cryptanalysis of Feal and N-Hash. EUROCRYPT 1991: 1–16 Bert den Boer, Cryptanalysis of F.E.A.L., EUROCRYPT 1988:...
5 KB (551 words) - 01:40, 17 October 2023
(along with Uriel Feige and Amos Fiat), one of the inventors of differential cryptanalysis and has made numerous contributions to the fields of cryptography...
11 KB (772 words) - 22:30, 30 April 2024
Following the publication of LOKI89, information on the new differential cryptanalysis became available, as well as some early analysis results by (Knudsen...
6 KB (723 words) - 23:05, 27 March 2024
Salsa20 (section Cryptanalysis of Salsa20)
against differential cryptanalysis. (Specifically, it has no differential characteristic with higher probability than 2−130, so differential cryptanalysis would...
31 KB (3,568 words) - 16:32, 15 May 2024
Skipjack (cipher) (section Cryptanalysis)
exhaustive search) within months using impossible differential cryptanalysis. A truncated differential attack was also published against 28 rounds of Skipjack...
12 KB (1,080 words) - 19:11, 13 January 2024
break the cipher in a way that is similar to differential cryptanalysis. The term "rotational cryptanalysis" was coined by Dmitry Khovratovich and Ivica...
3 KB (309 words) - 01:31, 3 May 2024
found an attack on one round, and Biham and Shamir (1991) used differential cryptanalysis to attack one round with 2300 encryptions. Biham and Shamir also...
2 KB (301 words) - 21:55, 5 March 2024
KN-Cipher (section Cryptanalysis)
secure against ordinary differential cryptanalysis, KN-Cipher was later broken using higher order differential cryptanalysis. Presented as "a prototype...
3 KB (200 words) - 13:59, 21 April 2023
Eli Biham and Adi Shamir showed that GDES was vulnerable to differential cryptanalysis, and that any GDES variant faster than DES is also less secure...
2 KB (193 words) - 07:21, 27 April 2022
128-bit blocks and 128-bit keys. This version is susceptible to differential cryptanalysis; for about half the keys, the cipher can be broken with 236 chosen...
6 KB (749 words) - 15:35, 22 November 2023
Cryptography (section Cryptanalysis)
Standard for cryptography. DES was designed to be resistant to differential cryptanalysis, a powerful and general cryptanalytic technique known to the NSA...
98 KB (10,726 words) - 22:12, 12 May 2024
manifold Differential (coboundary), in homological algebra and algebraic topology, one of the maps of a cochain complex Differential cryptanalysis, a pair...
3 KB (398 words) - 04:19, 24 February 2024
perfect S-box. S-boxes can be analyzed using linear cryptanalysis and differential cryptanalysis in the form of a Linear approximation table (LAT) or...
10 KB (929 words) - 18:15, 28 October 2023
introduced by SHARK. Zodiac is theoretically vulnerable to impossible differential cryptanalysis, which can recover a 128-bit key in 2119 encryptions. Zodiac Technical...
3 KB (238 words) - 04:25, 18 March 2024
Madryga (section Cryptanalysis)
non-linear component, and flaws in them are what both differential cryptanalysis and linear cryptanalysis seek to exploit. While Madryga's rotations are data-dependent...
5 KB (717 words) - 21:33, 16 March 2024
Prince (cipher) (section Cryptanalysis)
cipher cryptanalysis" (PDF). {{cite journal}}: Cite journal requires |journal= (help) Posteuca, R.; Negara, G. (2015). "Integral cryptanalysis of round-reduced...
13 KB (1,376 words) - 13:37, 2 May 2024
Twofish (section Cryptanalysis)
is a truncated differential cryptanalysis of the full 16-round version. The paper claims that the probability of truncated differentials is 2−57.3 per...
9 KB (841 words) - 08:30, 25 April 2024
rounds is susceptible to linear cryptanalysis, and a reduced version of 5 rounds is susceptible to differential cryptanalysis. In 2014, Alex Biryukov and...
3 KB (344 words) - 11:33, 10 April 2023