Extendible hashing is a type of hash system which treats a hash as a bit string and uses a trie for bucket lookup. Because of the hierarchical nature... 11 KB (1,728 words) - 03:17, 24 March 2024 |
range. In Linear Hashing there are two types of buckets, those that are to be split and those already split. While extendible hashing splits only overflowing... 13 KB (1,732 words) - 16:10, 12 December 2023 |
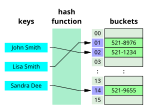 | Bloom filter Consistent hashing Distributed hash table Extendible hashing Hash array mapped trie Lazy deletion Pearson hashing PhotoDNA Rabin–Karp string... 54 KB (5,928 words) - 09:52, 17 April 2024 |
 | dynamic perfect hashing; cuckoo hashing; hopscotch hashing; and extendible hashing.: 42–69 A simple alternative to perfect hashing, which also allows... 24 KB (2,956 words) - 07:36, 14 December 2023 |
families are known (for hashing integers, vectors, strings), and their evaluation is often very efficient. Universal hashing has numerous uses in computer... 29 KB (4,886 words) - 10:36, 18 April 2024 |
In machine learning, feature hashing, also known as the hashing trick (by analogy to the kernel trick), is a fast and space-efficient way of vectorizing... 20 KB (3,118 words) - 13:13, 22 March 2024 |
 | SQL extended for graph traversal. OrientDB uses several indexing mechanisms based on B-tree and Extendible hashing, the last one is known as "hash index"... 11 KB (990 words) - 22:58, 7 March 2024 |
uses hashing techniques to enable fast retrieval of the data by key. The hashing scheme used is a form of extendible hashing, so that the hashing scheme... 13 KB (1,607 words) - 16:13, 8 May 2024 |
of work, for hashing digital signatures and as a key derivation function Polkadot, a multi-chain blockchain uses BLAKE2b as its hashing algorithm. PCI... 30 KB (2,814 words) - 09:48, 25 April 2024 |
computer science and data mining, MinHash (or the min-wise independent permutations locality sensitive hashing scheme) is a technique for quickly estimating... 25 KB (3,184 words) - 23:20, 4 December 2023 |
methods that require a high-quality hash function, including hopscotch hashing, cuckoo hashing, and the MinHash technique for estimating the size of... 19 KB (2,762 words) - 10:08, 24 September 2023 |
 | Key derivation function (redirect from Password hashing) this context. In 2013 a Password Hashing Competition was announced to choose a new, standard algorithm for password hashing. On 20 July 2015 the competition... 13 KB (1,625 words) - 17:56, 8 March 2024 |
state expandable hashing expander graph exponential extended binary tree extended Euclidean algorithm extended k-d tree extendible hashing external index... 35 KB (3,134 words) - 05:03, 28 January 2024 |
Spiral hashing, also known as Spiral Storage is an extensible hashing algorithm. As in all hashing schemes, spiral hashing stores records in a varying... 4 KB (461 words) - 11:49, 13 August 2023 |
 | search tries Hash trie Deterministic finite automata Judy array Search algorithm Extendible hashing Hash array mapped trie Prefix hash tree Burstsort... 18 KB (2,339 words) - 01:05, 27 April 2024 |
 | Java collections framework (section HashSet class) class include ConcurrentSkipListMap, EnumMap, HashMap, IdentityHashMap, TreeMap and WeakHashMap. EnumMap extends AbstractMap. EnumMap has comparable speed... 43 KB (4,279 words) - 10:21, 25 February 2024 |
 | HMAC (redirect from Keyed-Hashing Message Authentication) the hash function (e.g. 64 bytes for SHA-1) // Keys longer than blockSize are shortened by hashing them if (length(key) > blockSize) then key = hash(key)... 19 KB (2,305 words) - 09:57, 7 May 2024 |
 | Merkle tree (redirect from Tiger-Tree Hash) the above picture hash 0 is the result of hashing the concatenation of hash 0-0 and hash 0-1. That is, hash 0 = hash( hash 0-0 + hash 0-1 ) where "+" denotes... 15 KB (1,787 words) - 22:42, 29 April 2024 |
Pearson hashing is a non-cryptographic hash function designed for fast execution on processors with 8-bit registers. Given an input consisting of any... 4 KB (511 words) - 21:38, 4 May 2024 |
a checksum. Hash function security summary Secure Hash Algorithms NIST hash function competition Key derivation functions (category) "Hash functions".... 10 KB (280 words) - 06:15, 7 February 2024 |
Rainbow table (category Cryptographic hash functions) this attack is to compute the hashes using a key derivation function that adds a "salt" to each password before hashing it, with different passwords receiving... 24 KB (3,456 words) - 20:43, 21 April 2024 |
SHA-3 (category Cryptographic hash functions) stream cipher, an authenticated encryption system, a "tree" hashing scheme for faster hashing on certain architectures, and AEAD ciphers Keyak and Ketje... 51 KB (5,620 words) - 14:24, 19 April 2024 |
Number sign (redirect from Hash sign) symbol # is known variously in English-speaking regions as the number sign, hash, or pound sign. The symbol has historically been used for a wide range of... 43 KB (4,420 words) - 14:04, 9 May 2024 |
"signs of weakness". It is deprecated in favor of SHA-256 and other strong hashing algorithms. Nevertheless, as of 2014[update], it remained in use in public... 9 KB (1,051 words) - 18:55, 14 April 2024 |
suffixes of words. The suffix tree is a type of trie. Tries support extendible hashing, which is important for search engine indexing. Used for searching... 35 KB (4,766 words) - 21:56, 13 April 2024 |
Torrent file (section Distributed hash tables) merkle root hashes for each piece. The new format uses SHA-256 in both the piece-hashing and the infohash, replacing the broken SHA-1 hash. The "btmh"... 18 KB (2,303 words) - 03:22, 13 April 2024 |




