 | A cryptographic hash function (CHF) is a hash algorithm (a map of an arbitrary binary string to a binary string with a fixed size of n {\displaystyle... 45 KB (6,067 words) - 11:48, 27 April 2024 |
checksum. Hash function security summary Secure Hash Algorithms NIST hash function competition Key derivation functions (category) "Hash functions". www.azillionmonkeys... 10 KB (280 words) - 06:15, 7 February 2024 |
cryptography, Whirlpool (sometimes styled WHIRLPOOL) is a cryptographic hash function. It was designed by Vincent Rijmen (co-creator of the Advanced Encryption... 11 KB (1,054 words) - 03:57, 19 March 2024 |
BLAKE is a cryptographic hash function based on Daniel J. Bernstein's ChaCha stream cipher, but a permuted copy of the input block, XORed with round constants... 30 KB (2,814 words) - 09:48, 25 April 2024 |
The Secure Hash Algorithms are a family of cryptographic hash functions published by the National Institute of Standards and Technology (NIST) as a U.S... 3 KB (464 words) - 03:57, 19 March 2024 |
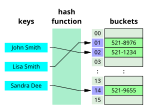 | data type that maps keys to values. A hash table uses a hash function to compute an index, also called a hash code, into an array of buckets or slots... 54 KB (5,928 words) - 09:52, 17 April 2024 |
hash >> 6; } hash += hash << 3; hash ^= hash >> 11; hash += hash << 15; return hash; } Sample hash values for one_at_a_time hash function. one_at_a_time("a"... 7 KB (852 words) - 03:34, 19 July 2023 |
is a non-cryptographic hash function created by Glenn Fowler, Landon Curt Noll, and Kiem-Phong Vo. The basis of the FNV hash algorithm was taken from... 14 KB (1,410 words) - 09:11, 25 March 2024 |
The MD2 Message-Digest Algorithm is a cryptographic hash function developed by Ronald Rivest in 1989. The algorithm is optimized for 8-bit computers.... 9 KB (1,051 words) - 18:55, 14 April 2024 |
 | HMAC (redirect from Keyed-Hashing Message Authentication) type of message authentication code (MAC) involving a cryptographic hash function and a secret cryptographic key. As with any MAC, it may be used to simultaneously... 19 KB (2,305 words) - 16:54, 4 April 2024 |
 | password, or a passphrase using a pseudorandom function (which typically uses a cryptographic hash function or block cipher). KDFs can be used to stretch... 13 KB (1,625 words) - 17:56, 8 March 2024 |
hash function security/cryptanalysis can be found at hash function security summary. Basic general information about the cryptographic hash functions:... 16 KB (785 words) - 15:03, 26 January 2024 |
cryptographic hash function designed by Ross Anderson and Eli Biham in 1995 for efficiency on 64-bit platforms. The size of a Tiger hash value is 192 bits... 9 KB (910 words) - 14:47, 30 September 2023 |
The GOST hash function, defined in the standards GOST R 34.11-94 and GOST 34.311-95 is a 256-bit cryptographic hash function. It was initially defined... 16 KB (2,206 words) - 01:50, 17 October 2023 |
JH is a cryptographic hash function submitted to the NIST hash function competition by Hongjun Wu. Though chosen as one of the five finalists of the competition... 4 KB (355 words) - 02:36, 11 January 2024 |
universal hashing (in a randomized algorithm or data structure) refers to selecting a hash function at random from a family of hash functions with a certain... 29 KB (4,886 words) - 10:36, 18 April 2024 |
non-cryptographic hash functions (NCHFs) are hash functions intended for applications that do not need the rigorous security requirements of the cryptographic hash functions... 6 KB (728 words) - 00:40, 29 April 2024 |
ShangMi 3 (SM3) is a cryptographic hash function used in the Chinese National Standard. It was published by the National Cryptography Administration (Chinese:... 3 KB (287 words) - 17:06, 16 November 2023 |
widely used hash function producing a 128-bit hash value. MD5 was designed by Ronald Rivest in 1991 to replace an earlier hash function MD4, and was... 41 KB (4,405 words) - 16:27, 16 March 2024 |
SHA-1 (redirect from SHA-1 hash) cryptography, SHA-1 (Secure Hash Algorithm 1) is a hash function which takes an input and produces a 160-bit (20-byte) hash value known as a message digest... 51 KB (5,763 words) - 18:12, 24 April 2024 |
Rainbow table (redirect from Reduction function) cryptographic hash function, usually for cracking password hashes. Passwords are typically stored not in plain text form, but as hash values. If such... 24 KB (3,456 words) - 20:43, 21 April 2024 |
cryptographic hash functions. Note that not all entries may be up to date. For a summary of other hash function parameters, see comparison of cryptographic hash functions... 17 KB (1,055 words) - 12:18, 2 March 2023 |
to compute multiple hash functions, but a related version of MinHash scheme avoids this penalty by using only a single hash function and uses it to select... 25 KB (3,184 words) - 23:20, 4 December 2023 |
Preimage attack (redirect from Hash function preimage) attack on cryptographic hash functions tries to find a message that has a specific hash value. A cryptographic hash function should resist attacks on... 7 KB (895 words) - 15:44, 13 April 2024 |
 | Merkle tree (redirect from Tiger-Tree Hash) the above picture hash 0 is the result of hashing the concatenation of hash 0-0 and hash 0-1. That is, hash 0 = hash( hash 0-0 + hash 0-1 ) where "+" denotes... 15 KB (1,787 words) - 22:42, 29 April 2024 |
SIMD is a cryptographic hash function based on the Merkle–Damgård construction submitted to the NIST hash function competition by Gaëtan Leurent. It is... 1 KB (127 words) - 13:39, 9 February 2023 |



