Carroll published "The Alphabet-Cipher" in 1868, possibly in a children's magazine. It describes what is known as a Vigenère cipher, a well-known scheme... 3 KB (555 words) - 08:42, 16 June 2023 |
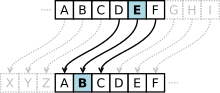 | of substitution cipher in which each letter in the plaintext is replaced by a letter some fixed number of positions down the alphabet. For example, with... 19 KB (2,028 words) - 01:36, 17 April 2024 |
by writing out the alphabet in some order to represent the substitution. This is termed a substitution alphabet. The cipher alphabet may be shifted or... 29 KB (3,985 words) - 09:07, 20 February 2024 |
The affine cipher is a type of monoalphabetic substitution cipher, where each letter in an alphabet is mapped to its numeric equivalent, encrypted using... 10 KB (1,126 words) - 00:41, 23 March 2024 |
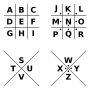 | The pigpen cipher (alternatively referred to as the masonic cipher, Freemason's cipher, Rosicrucian cipher, Napoleon cipher, and tic-tac-toe cipher) is... 10 KB (1,226 words) - 04:22, 25 March 2024 |
Atbash (redirect from Atbash cipher) cipher originally used to encrypt the Hebrew alphabet. It can be modified for use with any known writing system with a standard collating order. The Atbash... 7 KB (645 words) - 11:15, 24 April 2024 |
the encoder then uses as the start of the cipher alphabet. The end of the cipher alphabet is the rest of the alphabet in order without repeating the letters... 15 KB (2,528 words) - 09:42, 23 November 2023 |
 | done according to the alphabet of the Baconian cipher (from the Latin Alphabet), shown below: A second version of Bacon's cipher uses a unique code for... 8 KB (773 words) - 15:51, 6 March 2024 |
polyalphabetic cipher is a substitution, using multiple substitution alphabets. The Vigenère cipher is probably the best-known example of a polyalphabetic cipher, though... 6 KB (683 words) - 07:58, 14 March 2024 |
 | The Theban alphabet, also known as the witches' alphabet, is a writing system, specifically a substitution cipher of the Latin script, that was used by... 9 KB (804 words) - 22:06, 29 September 2023 |
The trifid cipher is a classical cipher invented by Félix Delastelle and described in 1902. Extending the principles of Delastelle's earlier bifid cipher... 5 KB (669 words) - 19:08, 22 February 2024 |
 | Cipher runes, or cryptic runes, are the cryptographical replacement of the letters of the runic alphabet. The knowledge of cipher runes was best preserved... 5 KB (581 words) - 10:33, 3 December 2023 |
 | keys. The Caesar Cipher is one of the earliest known cryptographic systems. Julius Caesar used a cipher that shifts the letters in the alphabet in place... 15 KB (2,044 words) - 15:56, 1 April 2024 |
 | Polybius square (redirect from Greek number cipher) cipher without a key (or, in other words, with a key of plain alphabet): The message is transformed into coordinates on the Polybius square, and the coordinates... 11 KB (1,130 words) - 06:40, 8 February 2024 |
In cryptography, the ADFGVX cipher was a manually applied field cipher used by the Imperial German Army during World War I. It was used to transmit messages... 13 KB (1,696 words) - 18:27, 12 February 2024 |
 | Enigma machine (redirect from Enigma cipher machine) The Enigma machine is a cipher device developed and used in the early- to mid-20th century to protect commercial, diplomatic, and military communication... 92 KB (11,241 words) - 05:23, 19 April 2024 |
The Two-square cipher, also called double Playfair, is a manual symmetric encryption technique. It was developed to ease the cumbersome nature of the... 11 KB (1,673 words) - 23:29, 5 March 2022 |
 | ROT13 (category Classical ciphers) substitution cipher that replaces a letter with the 13th letter after it in the Latin alphabet. ROT13 is a special case of the Caesar cipher which was developed... 19 KB (2,025 words) - 11:43, 14 March 2024 |
 | The Lorenz SZ40, SZ42a and SZ42b were German rotor stream cipher machines used by the German Army during World War II. They were developed by C. Lorenz... 34 KB (3,764 words) - 18:39, 13 April 2024 |
 | Tabula recta (redirect from Trithemius cipher) equivalent to Leon Battista Alberti's cipher disk except that the order of the letters in the target alphabet is not mixed. The tabula recta is often referred... 7 KB (939 words) - 23:25, 2 February 2024 |
 | to the "Q" in the cipher alphabet). The entire message is then encoded according to this key. In addition to simple substitution ciphers, the cipher disk... 5 KB (647 words) - 22:52, 4 September 2021 |
 | determine the next element in the keystream. This cipher was invented in 1586 by Blaise de Vigenère with a reciprocal table of ten alphabets. Vigenère's... 9 KB (1,276 words) - 15:02, 26 January 2024 |
cryptography, a block cipher is a deterministic algorithm that operates on fixed-length groups of bits, called blocks. Block ciphers are the elementary building... 50 KB (6,542 words) - 17:13, 1 April 2024 |