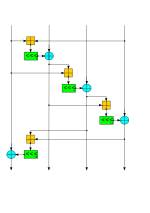
In cryptography, the simple XOR cipher is a type of additive cipher, an encryption algorithm that operates according to the principles: A ⊕ {\displaystyle...
9 KB (1,033 words) - 16:06, 30 December 2023
Exclusive or (redirect from Xor)
value Propositional calculus Rule 90 XOR cipher XOR gate XOR linked list Germundsson, Roger; Weisstein, Eric. "XOR". MathWorld. Wolfram Research. Retrieved...
31 KB (3,347 words) - 08:25, 1 May 2024
The xor–encrypt–xor (XEX) is a (tweakable) mode of operation of a block cipher. In tweaked-codebook mode with ciphertext stealing (XTS mode), it is one...
4 KB (454 words) - 16:16, 28 December 2023
of the cipher, it is also known as state cipher. In practice, a digit is typically a bit and the combining operation is an exclusive-or (XOR). The pseudorandom...
23 KB (2,217 words) - 13:45, 7 May 2024
because the plaintext or ciphertext is only used for the final XOR, the block cipher operations may be performed in advance, allowing the final step...
52 KB (5,906 words) - 08:12, 7 April 2024
used to build block ciphers. Examples of such block ciphers are BEAR and LION. Cipher security summary Topics in cryptography XOR cipher Cusick, Thomas W...
50 KB (6,475 words) - 22:23, 3 May 2024
also refer to: XOR cipher, an encryption algorithm XOR gate, a digital logic gate bitwise XOR, an operator used in computer programming XOR (video game)...
612 bytes (113 words) - 14:42, 23 February 2024
Symmetric-key algorithm (redirect from Symmetric cipher)
Porta polyalphabetic cipher is self-reciprocal. Purple cipher RC4 ROT13 XOR cipher Vatsyayana cipher The majority of all modern ciphers can be classified...
15 KB (1,544 words) - 16:02, 13 May 2024
Stream ciphers, where plaintext bits are combined with a cipher bit stream by an exclusive-or operation (xor), can be very secure if used properly[citation...
7 KB (1,029 words) - 04:31, 17 October 2023
result in X Y := X XOR Y; // XOR the values and store the result in Y X := Y XOR X; // XOR the values and store the result in X Since XOR is a commutative...
16 KB (1,978 words) - 14:04, 22 March 2024
One-time pad (redirect from Vernam cipher)
Gilbert Vernam for the XOR operation used for the encryption of a one-time pad. Derived from his Vernam cipher, the system was a cipher that combined a message...
58 KB (7,728 words) - 12:24, 17 May 2024
implementations. Speck is an add–rotate–xor (ARX) cipher. The NSA began working on the Simon and Speck ciphers in 2011. The agency anticipated some agencies...
23 KB (2,411 words) - 04:35, 11 December 2023
Salsa20 (redirect from ChaCha (cipher))
architectures. Both ciphers are built on a pseudorandom function based on add–rotate–XOR (ARX) operations — 32-bit addition, bitwise addition (XOR) and rotation...
31 KB (3,568 words) - 16:32, 15 May 2024
Labs research engineer who, in 1917, invented a cipher system that used the Boolean "exclusive or" (XOR) function, symbolised by ⊕. This is represented...
34 KB (3,764 words) - 18:39, 13 April 2024
Advanced Encryption Standard (redirect from AES (cipher))
of the subkey using bitwise XOR. On systems with 32-bit or larger words, it is possible to speed up execution of this cipher by combining the SubBytes and...
49 KB (5,609 words) - 15:54, 18 May 2024
Cryptography (redirect from Codes and ciphers)
plaintext. A cipher (or cypher) is a pair of algorithms that carry out the encryption and the reversing decryption. The detailed operation of a cipher is controlled...
98 KB (10,726 words) - 17:23, 17 May 2024
Blowfish is a symmetric-key block cipher, designed in 1993 by Bruce Schneier and included in many cipher suites and encryption products. Blowfish provides...
16 KB (1,783 words) - 19:05, 14 April 2024
International Data Encryption Algorithm (redirect from IDEA (cipher))
Improved Proposed Encryption Standard (IPES), is a symmetric-key block cipher designed by James Massey of ETH Zurich and Xuejia Lai and was first described...
12 KB (1,499 words) - 19:07, 14 April 2024
the T52 is not just a pseudorandom number generator-and-XOR cipher. For example, if a cipher clerk erred and sent two different messages using exactly...
7 KB (920 words) - 18:19, 21 April 2024
cryptography, a Feistel cipher (also known as Luby–Rackoff block cipher) is a symmetric structure used in the construction of block ciphers, named after the...
10 KB (1,316 words) - 05:28, 15 May 2024
Lucifer was the name given to several of the earliest civilian block ciphers, developed by Horst Feistel and his colleagues at IBM. Lucifer was a direct...
6 KB (749 words) - 15:35, 22 November 2023
binaries are used, the encryption between both endpoints is only a simple XOR cipher, which is completely trivial to decode. This type of build is not supported...
3 KB (261 words) - 18:57, 11 July 2023
In classical cryptography, the running key cipher is a type of polyalphabetic substitution cipher in which a text, typically from a book, is used to provide...
9 KB (1,279 words) - 09:47, 19 January 2024
Serpent is a symmetric key block cipher that was a finalist in the Advanced Encryption Standard (AES) contest, in which it ranked second to Rijndael. Serpent...
16 KB (1,912 words) - 17:43, 27 March 2024
Ascon is a family of lightweight authenticated ciphers that had been selected by US National Institute of Standards and Technology (NIST) for future standardization...
8 KB (848 words) - 03:29, 28 April 2024
substitution cipher only from an unusual perspective; typically, the plaintext letter is combined (not substituted) in some manner (e.g., XOR) with the key...
29 KB (3,985 words) - 09:07, 20 February 2024
The Tor traffic is wrapped in a WebSocket format and disguised with an XOR cipher. A free software implementation of flash proxies is available. It uses...
3 KB (297 words) - 12:24, 9 May 2024
ROT13 (category Classical ciphers)
pattern 00101010 (42) using the exclusive or (XOR) operation. This effects a simple XOR cipher. Like ROT13, XOR (and therefore memfrob()) is self-reciprocal...
19 KB (2,025 words) - 11:43, 14 March 2024
Initialization vector (category Block cipher modes of operation)
either P1 or P2 reveals the other plaintext since C1 xor C2 = (P1 xor K) xor (P2 xor K) = P1 xor P2. Many schemes require the IV to be unpredictable by...
14 KB (1,779 words) - 08:47, 29 April 2024
function—memfrob()—which performs an XOR combination of a given variable and the binary pattern 00101010 (42) as an XOR cipher. Tiling a plane using regular...
58 KB (7,080 words) - 14:33, 12 May 2024