In cryptography, a zero-knowledge password proof (ZKPP) is a type of zero-knowledge proof that allows one party (the prover) to prove to another party... 3 KB (331 words) - 14:44, 1 July 2022 |
In cryptography, a zero-knowledge proof or zero-knowledge protocol is a method by which one party (the prover) can prove to another party (the verifier)... 61 KB (7,928 words) - 05:39, 15 April 2024 |
computational zero-knowledge without requiring interaction Zero-knowledge password proof, an interactive method for one party (the prover) to prove to... 727 bytes (137 words) - 19:37, 12 September 2021 |
Absolute zero 0K, an abbreviation for Zero knowledge in cryptology Zero-knowledge proof Non-interactive zero-knowledge proof Zero-knowledge password proof 0K... 698 bytes (144 words) - 11:23, 12 August 2023 |
Cryptographic protocol Zero-knowledge proof Interactive proof system Topics in cryptography Zero-knowledge password proof Soundness (interactive proof) Shafi Goldwasser... 9 KB (1,635 words) - 14:07, 5 December 2023 |
effectively conveys a zero-knowledge password proof from the user to the server. In revision 6 of the protocol only one password can be guessed per connection... 28 KB (3,404 words) - 15:37, 22 April 2024 |
of cryptography Zero-knowledge password proof Designed to be not encumbered by patents. Hao, Feng; Ryan, Peter Y. A. (2011). "Password Authenticated Key... 17 KB (1,841 words) - 16:06, 12 February 2024 |
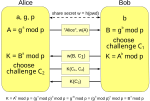 | amplify a shared password into a shared key, where the shared key may subsequently be used to provide a zero-knowledge password proof or other functions... 3 KB (389 words) - 16:17, 17 July 2022 |
eavesdropper's hands. It can be seen as an authentication via a zero-knowledge password proof. Various 'augmented forms' of PAKE incorporate an Oblivious... 28 KB (3,333 words) - 06:28, 8 May 2024 |
Key-agreement protocol (section Passwords) encapsulation mechanism Key management Password-authenticated key agreement Interlock protocol Zero-knowledge password proof Neural cryptography § Neural key... 6 KB (803 words) - 23:22, 5 April 2024 |
computer science concept of zero-knowledge proof. Most[citation needed] cloud storage services keep a copy of the client's password on their servers, allowing... 4 KB (396 words) - 13:21, 23 November 2023 |
 | card and initiates an exchange of messages that constitute a zero-knowledge password proof that the card is Peggy's. The building then allows Peggy to... 3 KB (318 words) - 18:29, 7 February 2024 |
challenge-response algorithms are: Zero-knowledge password proof and key agreement systems (such as Secure Remote Password (SRP)) Challenge-Handshake Authentication... 11 KB (1,560 words) - 04:37, 1 May 2024 |
together with the Zero-knowledge proofs (using for example Schnorr non-interactive zero-knowledge proof as specified in RFC 8235) for the proof of the exponents... 10 KB (1,501 words) - 23:30, 22 November 2023 |
algorithm • Y-stations • Yuliang Zheng Zeroisation • Zero-knowledge password proof • Zero-knowledge proof • Zfone • Zodiac (cipher) • ZRTP • Zimmermann–Sassaman... 67 KB (2,943 words) - 23:51, 25 November 2023 |
SQRL (category Password authentication) pseudonymous zero-knowledge proof rather than providing a user ID and password. This method is thought to be impervious to a brute-force password attack or... 16 KB (1,438 words) - 00:25, 26 January 2024 |
 | Alice and Bob (section Interactive proof systems) genders are alternated: Alice, Bob, Carol, Dave, Eve, etc. For interactive proof systems there are other characters: The names Alice and Bob are often used... 24 KB (2,023 words) - 07:18, 22 April 2024 |
Game theory (redirect from Two-person zero-sum game) mixed-strategy equilibria in two-person zero-sum game and its proof by John von Neumann. Von Neumann's original proof used the Brouwer fixed-point theorem... 158 KB (17,256 words) - 04:26, 6 May 2024 |
Padding (cryptography) (section Zero padding) small variations in payload size, such as plus or minus just one byte in a password-guessing attack for example. If the message sender is unlucky enough to... 23 KB (3,307 words) - 18:11, 14 February 2024 |
 | full version of MD4 can be forged with this knowledge. These attacks do not contradict the security proof of HMAC, but provide insight into HMAC based... 19 KB (2,305 words) - 09:57, 7 May 2024 |
{\displaystyle h^{\alpha \beta ab(x-y)}=h^{0}=1} . This proves correctness. Zero-knowledge proof Markus Jakobsson, Moti Yung (1996). "Proving without knowing: On... 8 KB (1,153 words) - 04:20, 15 January 2024 |
must use a unique 16-character alphanumeric password generated by Google instead of the user's normal password. Users who seek an even higher level of security... 13 KB (1,269 words) - 23:06, 28 April 2024 |
conflicted with the mechanism behind cryptographic zero-knowledge proofs. SpiderOak adopted the phrase "no knowledge" for their marketing. In November 2017, founder... 16 KB (1,283 words) - 12:53, 25 March 2024 |
List of Google Easter eggs (section Knowledge Graph) unit and its power adapter read H2G2-42 and MST3K-US, respectively. The password for Google Fi Wireless data only SIM cards is "h2g2", another reference... 144 KB (15,275 words) - 00:44, 11 May 2024 |
 | Vault 7 (section Part 1 – "Year Zero") Screwdriver malware that could use the Thunderbolt interface to bypass Apple's password firmware protection. On 31 March 2017, WikiLeaks published the third part... 70 KB (7,568 words) - 22:45, 29 April 2024 |
the hash of the original password, which may or may not be trivial. Reversing password encryption (e.g. to obtain a password to try against a user's account... 51 KB (5,763 words) - 18:12, 24 April 2024 |
smallest non-zero value that can be represented by an octuple-precision IEEE floating-point value. 1×10−6176 is equal to the smallest non-zero value that... 89 KB (9,912 words) - 17:24, 8 May 2024 |



